This document details Part 1 of the Structured Threat
Information Expression (STIX™) 2.0 Interoperability Test Documents. It defines
a set of test cases that software products, categorized by persona, must
implement to achieve STIXPreferred self-certification. The STIXPreferred
certification uses the term persona throughout the test cases to
represent a category of similar product capabilities in a security ecosystem.
See Section 1.3.2 for a full list of all persona used. To claim STIXPreferred
certification, implementations of one or more personas must adhere to expected
behaviors and outcomes as detailed in the test cases.
This document, Part 1, is the first in a series of documents
designed to be modular, i.e. new documents will be created as additional test
cases are developed. Subsequent documents will be created and numbered Part 2,
Part 3, ...etc. Each test document will describe what personas and test cases
are covered in that specific document version.
The OASIS Cyber Threat Intelligence Technical Committee (CTI
TC) recommends users of this test document become familiar with the STIX 2.0
Core Concepts, and STIX 2.0 Objects, and other supporting specifications (as
given in the Related Work section above) prior to implementing the test cases
in this document. An organization must submit the results for their specific
tests to the OASIS CTI TC Interoperability Subcommittee to achieve confirmation
of interoperability and to be listed on the OASIS website page showing the
organization’s compliance to STIX 2.0. Further submittal instructions are found
in Section 3 Persona Checklists.
NOTE: The STIX™ & TAXII™ specifications contain
normative references to other specifications with which an implementation may
need to reference and meet in order to comply with these specifications. This
document assumes that such requirements are also met.
1.1 IPR Policy
This specification is provided under the Non-Assertion Mode
of the OASIS IPR Policy, the mode chosen when the Technical Committee was
established. For information on whether any patents have been disclosed that
may be essential to implementing this specification, and any offers of patent
licensing terms, please refer to the Intellectual Property Rights section of
the TC’s web page (https://www.oasis-open.org/committees/cti/ipr.php).
1.2 Terminology
Security Infrastructure - Any software or hardware
instance that provides a function in the support of securing networks and
systems
Security Personnel - Any human being that is
performing a security function within an organization including threat
analysis; security operations; network operations, etc.
Producer - A software instance that creates STIX 2.0
content to share with other systems.
Respondent - A software instance that reads STIX 2.0
content and performs some action on that received data.
1.3 Overview
The approach that is being taken within the CTI TC is to
rely primarily on well-defined, common test cases to drive the demonstration of
interoperability between products using STIX 2.0 and the Trusted Automated
Exchange for Indicator Information (TAXII) version 2.0, also under development
within the CTI TC. Section 2 of this document outlines these common test cases
for organizations seeking to develop and demonstrate interoperability.
These test cases will enable personas (defined herein) of
the cyber threat intelligence information sharing community to build and test
information sharing files that are compliant with STIX 2.0 best practices.
1.3.1 Statement on
OPTIONAL Properties as defined in STIX™ 2.0
Note that this document includes tests that mandate the
presence of OPTIONAL STIX 2.0 object properties. These occurrences can be found
in required producer persona support, as well as test cases. In these
situations, producers must produce data containing these OPTIONAL properties in
order to demonstrate interoperability compliance as defined in this document.
Correspondingly, a respondent must properly process these OPTIONAL properties
to demonstrate interoperability.
1.3.2 Personas
The STIXPreferred personas shown in Figure 1 are used
throughout this document.
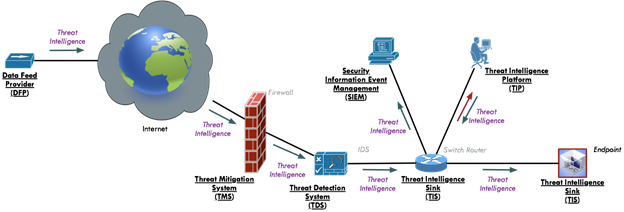
Figure 1 -
STIXPreferred Persona
●
Data Feed Provider (DFP)
○ Software
instance that acts as a producer of STIX 2.0 content.
●
Threat Intelligence Platform (TIP)
○ Software
instance that acts as a Producer and/or Respondent of STIX 2.0 content
primarily used to aggregate, refine and share intelligence with other machines
or security personnel operating other security infrastructure.
●
Security Incident and Event Management system (SIEM)
○ Software
instance that acts as a producer and/or Respondent of STIX 2.0 content. A SIEM
aggregates events, incidents and indicators and may produce STIX content based
on that security operations tasks associated with those activities. A SIEM that
consumes STIX content will typically consume sightings and/or indicators.
●
Threat Mitigation System (TMS)
○ Software
instance such as a firewall or Intrusion Prevention System (IPS), Endpoint
Detection and Response (EDR) software, etc. that acts on courses of action and
other threat mitigations.
●
Threat Detection System (TDS)
○ Software
instance such as Intrusion Detection System (IDS), Endpoint Detection and
Response (EDR) software, web proxy, etc. that monitors, detects and alerts.
●
Threat Intelligence Sink (TIS)
● Software
instance that consumes STIX 2.0 content in order to perform translations to
domain specific formats consumable by enforcement and/or detection systems that
do not natively support STIX 2.0. These consumers may or may not have the
capability of reporting sightings. A TIS will typically consume
intelligence identified in the STIX content but will not produce any STIX
content itself.
For an
organization to receive OASIS STIXPreferred self-certification, the software
instances must adhere to persona behavior and prescribed bundle contents as
detailed in the Required Producer Persona/Profile Support section of each test
case.
For documenting self-certification
for each persona tested, refer to the checklist and test requirements in
Section 3 Persona Checklist of this document.
The following Part 1 test cases are broken down into a
common set of test cases for each of the defined persona. There are also a set
of defined optional test cases for those persona that may choose to verify
additional capabilities.
The following test cases are defined in this document.
Table 1 - List of STIX Interoperability test cases
|
Description
|
Producer
Personas
|
Respondent
Personas
|
|
Indicator Sharing
|
DFP,
TIP
|
TMS,
TIS, TDS, TIP, SIEM
|
|
Sightings Sharing
|
DFP,
TIP, TMS, TDS
|
TIP,
SIEM
|
|
Versioning
|
All
|
All
|
|
Data Markings
|
All
|
All
|
|
Custom Objects & Properties
|
All
|
All
|
|
Course of Action Sharing
|
DFP,
TIP
|
TIP,
TMS, TIS, TDS
|
The following sections provide details on these test cases.
2.1 Common Test Case
Requirements
All test data must comply with the following set of
additional requirements.
1. Identities
Created
a.
All tests require the creation of an identity for the created_by_ref
property across all tests.
b.
The Identity created should represent the organization that is
responsible for the software instance under test.
c.
The following properties should be filled in:
i.
type with value ‘identity’
ii.
name with a value that represents the organization’s name
iii.
identity_class with value ‘organization’
iv.
id with a unique UUID
v.
Example:
“type":
"identity",
"name": "ACME Corp, Inc.",
"identity_class": "organization",
"id": "identity--f431f809-377b-45e0-aa1c-6a4751cae5ff"
2. x_interop_test use
a.
Throughout this test document this property is used to convey
a human-readable reference to the Interoperability document that defines the
required test content.
b.
Although this is a best practice to provide descriptive terms
for all intelligence produced, it is not mandatory for any producer to
generate and consume data that includes this property.
2.2 Indicator Sharing
One of the most common test cases that has emerged within
enterprises tracking threat intelligence globally and/or within Information
Sharing and Analysis Centers (ISACs) and Information Sharing and Analysis
Organizations (ISAOs) has been the sharing of Indicators (sometimes referred to
as Indicators of Compromise or IOCs) using a threat intelligence platform (TIP)
that integrates one or multiple Data Feed Providers (DFPs).
Indicators and other STIX data objects (SDOs), as defined in
the STIX 2.0 Specification, may be shared via proprietary feeds, open source
feeds and/or through a sharing community. The TIP is used to aggregate and
process the data and then map it to the STIX 2.0 data model. Some TIPs also
provide for data enrichment, analysis and indexing, visualization and
bi-directional IOC sharing with other security products through application
programming interfaces (APIs). The Respondents of the SDOs include both the
personas documented in this Committee Note for machine readable threat
intelligence (MRTI) and human analysts including, but not limited to: threat
intelligence analysts, fraud and risk analysts, malware analysts, and network
and endpoint guardians, among others. This high-level view is useful for
illustrating how a test case (in this case, sharing of Indicator objects) and a
persona will work together within this Committee Note for the purpose of
interoperability demonstration.
The following sections provide more detailed descriptions of
how a STIX 2.0 Indicator object may be used for the purpose of demonstrating
interoperability.
2.2.1 Description
A STIX 2.0 Indicator defines a pattern of STIX Cyber
Observable values of interest (e.g. suspicious or malicious). . There are
several common characteristics of data specified in test cases that will be
verified. The TIP producer persona, shown on Figure 3 operated by the
“Analyst”, has identified one or more Indicators that indicate malicious
content on the Internet. That content may be an entity of interest to consider
for monitoring activity. Also shown is how a TIP processes a STIX Bundle, and
it illustrates how the information is published as a Bundle to a TMS, which
then issues a response.
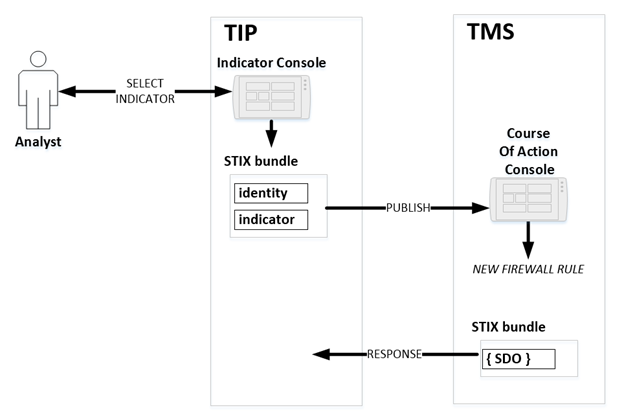
Figure 3 -
An analyst shares an indicator
2.2.2 Required Producer
Persona Support
The Producer persona must be able to create a STIX Bundle
with one or more indicators such as IP Address v4; IP Address v6 for all
Classless Inter-Domain Routing (CIDR) variations, and options.
Table 2 -
Producer Object Bundling Details
|
Personas
|
Behavior
|
|
DFP; TIP
|
1.
Producer allows a user to select or specify the IP Address associated
with Actor A and identify that Actor A’s IP address as an IOC to share to a
Respondent persona.
2.
The following data must be verified in the STIX bundle produced by the
persona:
a)
A bundle object must conform to mandatory attributes within the bundle
object including 'type'; 'id'; 'spec_version' and 'objects' where
i)
id has a globally unique identifier
ii)
spec_version is '2.0'
iii)
Within the objects array
1)
at least one Identity for the organization of the Producer
2)
at least one Indicator with the IP Address identified in the pattern
parameter
b)
The Identity object must conform to mandatory attributes within the
identity object spec including 'type'; 'name'; 'identity_class' and 'id'
where
i)
type is 'identity'
ii)
id has a globally unique identifier
iii)
identity_class is specified by the organization of the Producer
iv)
name is the name that the Producer wishes to associate with the
identity object
c)
The Indicator object must conform to mandatory attributes including
'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; 'pattern'' where
i)
created_by_ref must point to the identity of the Producer;
ii)
created and modified must match the timestamp to millisecond
granularity of when the user selected the Actor’s IP address to be an IOC
d)
The pattern attribute captures the various required fields that must
be supported by the Producer as defined in <ref 2.2.2.1>
|
2.2.3 Producer Test Case
Data
The following subsections provide the test case data for the
test. Verify for all test cases that the objects defined in each test are
produced either in a single bundle or across multiple bundles.
2.2.3.1 Indicator IPv4
Address
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"name":
"Bad IP1",
"description":
"IPv4 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value = '198.51.100.1']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.1,Indicator IPv4 Address",
}
]
2.2.3.2 Indicator IPv4
Address CIDR
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--86449d6c-c47a-4320-bb94-2eb7340928e8",
"name":
"Bad IP CIDR",
"description":
"IPv4 CIDR Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value ISSUBSET '198.51.100.0/24']"
"x_interop_test":
"STIX/TAXII 2.0 Interoperability Part 1, §2.2.3.2,Indicator IPv4
Address CIDR",
}
]
2.2.3.3 Two Indicators
with IPv4 Address CIDR
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--1b0eb2d2-cce4-4c18-a58d-cf238ceea505",
"name":
"Bad IP Subnets",
"description":
"Two IPv4 CIDR Indicators",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value ISSUBSET '198.51.100.0/24' OR ipv4-addr:value ISSUBSET
'196.45.200.0/24']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.3,Two Indicators with IPv4 Address CIDR",
}
]
2.2.3.4 Indicator with
IPv6 Address
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--919974fa-2461-4476-91ae-dd033c700f49",
"name":
"Bad IPv6-1",
"description":
"IPv6 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv6-addr:value = '2001:0db8:85a3:0000:0000:8a2e:0370:7334']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.4,Indicator with IPv6 Address",
}
]
2.2.3.5 Indicator with
IPv6 Address CIDR
"objects": [
{
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--b5dcc585-bf19-4ace-aa56-1e004448ee2a",
"name":
"Bad IPv6-CIDR",
"description":
"IPv6 CIDR Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv6-addr:value ISSUBSET '2001:DB8::0/120']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.5,IPv6 Address CIDR",
}
]
2.2.3.6 Multiple
Indicators within the same bundle
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--674aae52-d49b-412e-ab61-514e31f8021e",
"name":
"Bad IP Subnets",
"description":
"IPv4 CIDR Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value ISSUBSET '198.51.100.0/24' OR ipv4-addr:value ISSUBSET
'196.45.200.0/24']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.6,Multiple Indicators within the same bundle",
},
{
"type":
"indicator",
"id":
"indicator--e40f9107-9a76-4c92-89c0-d512fde1c120",
"name":
"Bad IP1",
"description":
"IPv4 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value = '198.51.100.12']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.6,Multiple Indicators within the same bundle",
}
]
2.2.3.7 Indicator FQDN
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--69a4eedb-05c5-463b-ba59-65257d652cf4",
"name":
"Bad Domain",
"description":
"FQDN Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[domain-name:value = 'www.5z8.info']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.7,Indicator FQDN",
}
]
2.2.3.8 Indicator URL
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--21edc30b-11c9-406d-867a-42fb4bdeedda",
"name":
"Bad URL",
"description":
"URL Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[url:value = 'https://www.5z8.info/foo']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.8,Indicator URL",
}
]
2.2.3.9 Indicator URL or
FQDN
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--81090d66-3036-4ff9-8032-c5facb50b20f",
"name":
"Bad URL or Domain",
"description":
"URL or FQDN Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified": "2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[url:value = 'https://www.5z8.info/foo' OR domain-name:value =
'www.5z8.info']"
"x_interop_test":
"STIX/TAXII 2.0 Interoperability Part 1, §2.2.3.9,Indicator URL or
FQDN",
}
]
2.2.3.10 Indicator File
hash with SHA256 or MD5 values
"objects": [
{
"type":
"identity",
"id":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"identity_class": "organization",
"name":
"ACME Corp, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--0cddd4c0-411a-47a7-8ccc-d0473d690a6f",
"name":
"Bad File1",
"description":
"File Hash Indicator",
"created_by_ref": "identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[file:hashes.'SHA-256' =
'bf07a7fbb825fc0aae7bf4a1177b2b31fcf8a3feeaf7092761e18c859ee52a9c' OR
file:hashes.MD5 = 'cead3f77f6cda6ec00f57d76c9a6879f']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.2.3.10,Indicator File hash with SHA256 or MD5 values",
}
]
2.2.4 Required
Respondent Support
The Respondent must be able to parse and display any
Indicator that has been shared with IP Address information.
Table 3 -
Respondent Object Bundling Details
|
Persona
|
Behavior
|
|
TIP
|
1.
TIP allows a user to receive a STIX bundle with an
a.
Identity and Indicator with the various required field pattern content
b.
Identity of the Producer
c.
Indicator with various required fields information contained in it
2.
Once received the TIP is able to display to the user the source of the
Indicator based on the identity's attribute 'name' and the identity_class
attribute
3.
For each Indicator, the TIP is able to verify that the created_by_ref
maps to an existing identity or one contained within the bundle received
4.
For each Indicator object, the TIP is able to display that the
indicator fields contained in the pattern represents an IOC.
|
|
TMS; TDS; TIS
|
1.
Respondent allows the reception of a STIX bundle with a(n)
a.
Bundle with an identity, and Indicator with content
b.
Identity of the Producer
c.
Indicator with the content information contained in it
2.
Once received the Respondent is able to verify the source of the
Indicator based on the identity's attribute 'name' and the identity_class
attribute and determines that is an allowed source of intelligence to act
upon
3.
For each Indicator, the Respondent is able to verify that the created
date represents an Indicator that has not been previously applied to its
network monitoring function and may update its rules to match on that
Indicator content
4.
For each Indicator object, the Respondent is able to capture network
information (packets or counts or flows) that the FileHash; IP; FQDN; URL
contained in the pattern matched against.
5.
Specifically, for the TMS persona, the TMS is able to block traffic based
on the Indicator pattern matched within a packet sequence.
|
|
SIEM
|
1.
SIEM allows the reception of a STIX Bundle with a(n)
a.
Bundle with an Identity and Indicator with the content
b.
Identity of the Producer
c.
Indicator with the content information contained in it
2.
Once received the SIEM is able to verify the source of the indicator
based on the Identity's attribute 'name' and the identity_class
attribute, and determines that it is an allowed source of intelligence to act
upon
3.
For each Indicator, the SIEM is able to verify that the created date
represents an indicator that has not been previously applied to its event
correlation and display functions, and updates its rules (if any) to match on
that indicator content
4.
For each Indicator object, the SIEM is able to display and/or alert
upon other relevant security information it has from other event log sources
(firewalls, sensors). The SIEM is able to show the overlap of previously
logged indicators and incoming indicator information including FileHash, IP,
FQDN, and URL. The SIEM may generate sightings based on the indicators.
|
2.2.5 Respondent Test
Case Data
This test case is primarily testing
the production of an Indicator and a Respondent's ability to parse and
represent and act on the Indicator data correctly. No other data is sent from
the Respondent back to the Producer.
2.3 Sighting Sharing
Another important scenario that will provide for
crowdsourcing in the context of a sharing community is the use of a Sighting
STIX Relationship Object (SRO). This is a unique form of a relationship object
that provides for the confirmation of a “sighting” of an Indicator SDO (as
evidenced by specific Cyber Observable objects) by a third-party; that is, by
an Identity separate from the original Producer of an Indicator SDO. The full
power of the use of trust communities within the ISAC and/or ISAO context
cannot be realized without the use of this SRO. Therefore, it is an important
test case to demonstrate for STIX interoperability.
2.3.1 Description
A STIX 2.0 Sighting object is an SRO primarily used to
capture documentation that some entity in the network has been seen by an
intelligence source. The Producer persona, shown on Figure 4 as an “Analyst”,
has selected one or more sightings observed by the supporting SIEM tool.
Consequently, the SIEM publishes a STIX Sighting Bundle and publishes it for
various receiving personas.
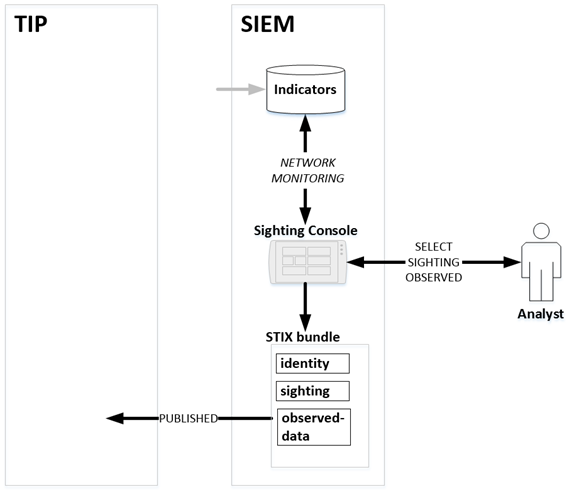
Figure 4 -
An analyst reports a sighting
2.3.2 Required Producer
Persona Support
The Producer persona must be able to create a STIX Bundle
with one or more Indicators as identified by the Indicator Sharing Producer
Test Case Data. All personas defined in Required Producer Persona Support are also
defined for Sighting Producer personas.
2.3.3 Producer Test Case
Data
Same as Indicator Sharing Producer Test
Case Data.
2.3.4 Required
Respondent Persona Support
The Respondent must be able to parse and display any
Indicator that has been shared as well as create a Sighting associated with the
Indicator.
Table 4 -
Producer Object Bundling Details
|
Persona
|
Behavior
|
|
TIP; SIEM
|
1.
Respondent supports all Respondent required behavior for Indicator
tests defined in Section 2.2.4.
2.
Respondent allows the user to create or select a Sighting object
observed and associated with each Indicator pattern identified in the
Producer's Bundle.
3.
Respondent in response allows user to send the Sighting information
back to the Producer and supports creation of a bundle with
a.
its own identity unique and different from the Producer
b.
a reference to each Indicator shared from the Producer
c.
a Sighting object
d.
an Observed Data object
4.
The Sighting object must have
a.
created_by_ref must point to the identity of the Respondent;
b.
created and modified must match the timestamp to
millisecond granularity of when the Sighting was created by the Respondent
c.
first_seen and last_seen must match when the observed
data was first and last seen by the system reporting the observed data
d.
count must match the number of times that the Indicator was
seen during the first and last seen values
e.
sighting_of_ref must match the Indicator sent by Producer
5.
The Observed Data object must have
a.
created_by_ref must point to the identity of the Respondent;
b.
created and modified must match the timestamp to
millisecond granularity of when the observed-data was created by the system
producing the observed-data
c.
first_observed and last_observed must match when the
observed data was first and last seen by the system reporting the Observed
Data
d.
number_observed must match the number of times that the
Indicator was seen during the start and stop values
e.
objects must match an Indicator pattern defined by the
Producer.
|
|
TMS
|
In addition to the verification
steps shown in the above row for TIP; SIEM, the TMS
SHALL provide evidence that it blocked the traffic identified by the patterns
in the Indicator.
|
|
TDS
|
In addition to the verification
steps shown in the above row for TIP; SIEM the TDS
SHALL show or provide statistics on how many packets or sessions matched the
Indicator content.
|
|
TIS
|
In addition to the verification
steps shown in the above row for TIP; SIEM the TIS
SHALL show or provide statistics on how many packets or sessions matched the
Indicator content.
|
2.3.5 Respondent Test
Case Data
The following subsections provide the
test case data for the test.
2.3.5.1 Sighting +
Indicator with IPv4 Address
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--ee20065d-2555-424f-ad9e-0f8428623c75",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"observed_data_refs": ["observed-data--455d15c6-415a-4008-addf-8a4405ede887"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.1 Sighting + Indicator with IPv4 Address",
},
{
"type":
"observed-data",
"id":
"observed-data--455d15c6-415a-4008-addf-8a4405ede887",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 50,
"objects": {
"0": {
"type":
"ipv4-addr",
"value":
"198.51.100.1"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.1 Sighting + Indicator with IPv4 Address",
}
]
2.3.5.2 Sighting +
Indicator with IPv4 Address Matching CIDR
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--da212f5f-3b58-4124-9faa-3f47536bac5c",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref": "indicator--86449d6c-c47a-4320-bb94-2eb7340928e8",
"observed_data_refs":
["observed-data--60c871de-5936-41f1-afbe-4ef829c3ee0a"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.2 Sighting + Indicator with IPv4 Address Matching CIDR",
},
{
"type":
"observed-data",
"id":
"observed-data--60c871de-5936-41f1-afbe-4ef829c3ee0a",
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.2 Sighting + Indicator with IPv4 Address Matching CIDR",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 50,
"objects": {
"0": {
"type":
"ipv4-addr",
"value":
"198.51.100.12"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.2 Sighting + Indicator with IPv4 Address Matching CIDR",
}
]
2.3.5.3 Sighting +
Indicator with IPv6 Address Matching CIDR
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--c3548e6f-4c45-40e0-a59e-d874e48b7f09",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref":
"indicator--b5dcc585-bf19-4ace-aa56-1e004448ee2a",
"observed_data_refs":
["observed-data--484a78ef-4a61-4c8d-b236-013fdafa4686"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.3 Sighting + Indicator with IPv6 Address Matching CIDR",
},
{
"type":
"observed-data",
"id":
"observed-data--484a78ef-4a61-4c8d-b236-013fdafa4686",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 50,
"objects": {
"0": {
"type":
"ipv6-addr",
"value":
"2001:0db8:0000:0000:0000:0000:0000:00af"
}
}
"x_interop_test":
"STIX/TAXII 2.0 Interoperability Part 1, §2.3.5.3 Sighting + Indicator
with IPv6 Address Matching CIDR",
}
]
2.3.5.4 Sighting +
Indicator with NO observed data
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--522bbde4-5960-413d-84df-62eee100fdb4",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref": "indicator--1b0eb2d2-cce4-4c18-a58d-cf238ceea505",
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.4 Sighting + Indicator with NO observed data",
}
]
2.3.5.5 Sighting +
Indicator with URL
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--3d9ee944-18c7-4731-84e0-b2847db251cf",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref": "indicator--21edc30b-11c9-406d-867a-42fb4bdeedda",
"observed_data_refs":
["observed-data--c80069a4-2cb6-47ba-88ab-76da10c3e4bf"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.5 Sighting + Indicator with URL",
},
{
"type":
"observed-data",
"id":
"observed-data--c80069a4-2cb6-47ba-88ab-76da10c3e4bf",
"created_by_ref": "identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 50,
"objects": {
"0": {
"type":
"url",
"value":
"https://www.5z8.info/foo"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.5 Sighting + Indicator with URL",
}
]
2.3.5.6 Sighting +
Indicator with File Hash
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--f5041831-bc0a-4ccd-b1a8-72ac021e0603",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 1,
"sighting_of_ref":
"indicator--0cddd4c0-411a-47a7-8ccc-d0473d690a6f",
"observed_data_refs":
["observed-data--2a31ca1e-b030-4e0c-91c1-26fd28d588ab"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.6 Sighting + Indicator with File Hash",
},
{
"type":
"observed-data",
"id":
"observed-data--2a31ca1e-b030-4e0c-91c1-26fd28d588ab",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 1,
"objects": {
"0": {
"type":
"file",
"hashes": {
"MD5": "cead3f77f6cda6ec00f57d76c9a6879f"
},
"size":
25536,
"name":
"foo.dll"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.3.5.6 Sighting + Indicator with File Hash",
}
]
2.4 Versioning
As additional information is discovered about an SDO, the
Producer of that object may version the original object using the versioning
approach outlined in Part 1 of the STIX 2.0 Specification. Other recipients of
the SDO will also be updated through their various personas as the original SDO
is versioned. This feature of the STIX 2.0 Specification allows for SDOs to be
updated as the context changes and the information becomes more complete, based
on enrichments and further intelligence discovery.
2.4.1 Description
A STIX 2.0 Producer or Respondent must support versioning of
objects to support interoperability within STIX.
2.4.2 Required Producer
Persona Creation Support
The Producer persona must be able to create a STIX Bundle
with one or more objects with the appropriate date representing when the object
was created for sharing.
The Producer persona has identified an STIX object that they
wish to share to Respondents.
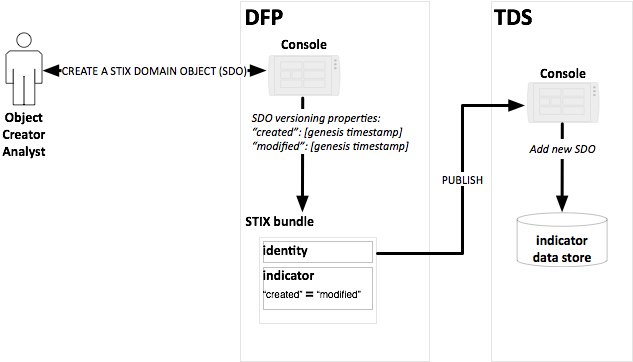
Figure 5 -
An analyst creates a new STIX object
NOTE: Not all personas defined in this spec create
Indicators.
Table 5 -
Producer Object Bundling Details
|
Persona
|
Behavior
|
|
All Indicator producer
personas
|
1.
Producer allows a user to select or specify STIX content to create and
send to a Respondent persona.
2.
The following data must be verified in the STIX content produced by
the persona:
a.
A bundle object must conform to mandatory attributes within the bundle
object including 'type'; 'id'; 'spec_version' and 'objects'
where
i.
id has a globally unique identifier
ii.
spec_version is '2.0'
iii.
Within the objects array, at least one;
1.
Identity for the organization of the Producer
2.
Indicator with the IP Address identified in the pattern parameter
b.
The identity object must conform to mandatory attributes within the
identity object spec including 'type'; 'name'; 'identity_class' and 'id'
where
i.
type is identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to share
associated with the Indicator
c.
The Indicator object must conform to mandatory attributes of Indicator
including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; 'pattern''
where
i.
created_by_ref must point to the Identity of the Producer;
ii.
created and modified must match the timestamp to
millisecond granularity of when the user selected the IP address to be an IOC
|
|
All Sighting producer
personas
|
1.
Producer allows a user to select or specify the STIX content to create
and send to a Respondent persona.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A Bundle object must conform to mandatory attributes within the object
including 'type'; 'id'; 'spec_version' and 'objects'
where
i.
id has a globally unique identifier
ii.
spec_version is '2.0'
iii.
Within the objects array, at least one;
1)
Identity for the organization of the Producer
2)
Sighting with the observed data for the indicator identified in the
pattern parameter
b)
The Identity object must conform to mandatory attributes within the
object spec including 'type'; 'name'; 'identity_class' and 'id' where
i)
type is Identity
ii)
id has a globally unique identifier
iii)
identity_class is specified by the organization of the Producer
iv)
name is the name that the Producer wishes to share associated
with the Sighting
c)
The Sighting object must conform to mandatory attributes of indicator
including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; 'pattern''
where
i)
created_by_ref must point to the identity of the Producer;
ii)
created and modified must match the timestamp to
millisecond granularity of when the Respondent created the Sighting
|
2.4.3 Producer Test Case
Data
The following subsections provide the test case data for the
test.
2.4.3.1 Creation of an
Indicator with Identity and Date
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--6cd5cd4f-ff42-4d67-8402-02aad22f8b63",
"name":
"Bad IP1",
"description":
"IPv4 Indicator",
"created_by_ref": "identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value = '198.51.100.1']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.3.1 Creation of an Indicator with Identity and Date",
}
]
2.4.3.2 Creation of a
Sighting with Identity and Date
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--f185c0e8-f187-4880-be0b-1f10df2d356f",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"observed_data_refs": ["observed-data--8fe6d276-56b9-4c3d-b99d-4ca4421b409c"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.3.2 Creation of a Sighting with Identity and Date",
},
{
"type":
"observed-data",
"id":
"observed-data--8fe6d276-56b9-4c3d-b99d-4ca4421b409c",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 50,
"objects": {
"0": {
"type":
"ipv4-addr",
"value":
"198.51.100.1"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.3.2 Creation of a Observed Data with Identity and Date",
}
]
2.4.4 Required
Respondent Creation Support
The Respondent must be able to parse and display the
creation and modification date of the objects received.
Table 6 -
Respondent Object Bundling Details
|
Persona
|
Behavior
|
|
All Indicator Respondent
Persona
|
1.
Respondent allows a user to receive a STIX Bundle with a(n)
a.
bundle with an identity and indicator with IP content
b.
identity of the producer
c.
indicator with IP address information contained in it
2.
Once received the Respondent is able to display to the user the
Producers of the indicator based on the identity's attribute 'name'
and the identity_class attribute
3.
For each Indicator, the Respondent is able to verify that the created_by_ref
maps to an existing identity received or one contained within the bundle
received
4.
For each Indicator, the Respondent may show the creation and modified
dates for them.
|
2.4.5 Respondent Test
Case Creation Data
This test case is primarily testing the production of an
Indicator; its related version information and a Respondent's ability to parse
and represent the data correctly. No other data is sent from the Respondent
back to the Producer.
2.4.6 Required Producer
Persona Modification Support
The Producer persona must be able
to create a STIX Bundle with one or more objects with the appropriate date
representing when the object was updated for sharing.
The Producer persona has identified
a STIX object that they wish to update and re-share to Respondents.
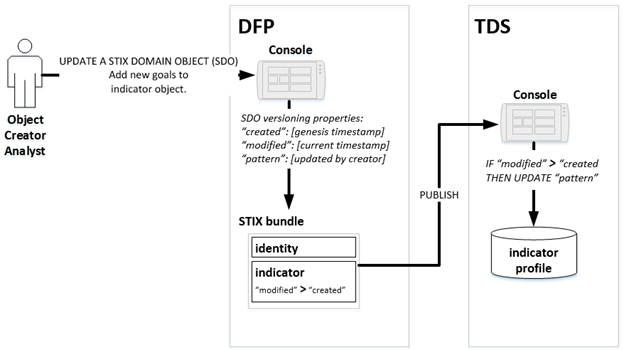
Figure 6 -
An analyst updates a STIX indicator object
Table 7 -
Producer Object Bundling Details
|
Persona
|
Behavior
|
|
All Indicator Producer Personas
|
1.
Producer allows a user to select a previously shared Indicator with IP
Address associated with Actor A.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A bundle object must conform to mandatory attributes within the bundle
object including 'type'; 'id'; 'spec_version' and 'objects' where
i.
id has a globally unique identifier
ii.
spec_version is '2.0'
iii.
Within the objects array, at least one;
1.
identity for the organization of the Producer
2.
indicator with the IP Address identified in the pattern
parameter
b.
The identity object must conform to mandatory attributes within the
identity object spec including 'type'; 'name'; 'identity_class' and 'id'
where
i.
type is identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to share associated
with the indicator
c.
The Indicator object must conform to mandatory attributes of indicator
including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; 'pattern''
where
i.
created_by_ref must point to the identity of the original
Producer
ii.
created must match the original creation timestamp to
millisecond granularity of when the user selected the IP address to be an IOC
originally
iii.
modified must match the new modified timestamp to millisecond granularity
of when the user updated the Indicator to be re-shared
iv.
description must be changed from the previously shared
Indicator
|
|
All Sighting Producer Personas
|
1.
Producer allows selection or specification of the STIX content to send
to a Respondent persona.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A bundle object must conform to mandatory attributes within the bundle
object including 'type'; 'id'; 'spec_version' and 'objects'
where
i.
id has a globally unique identifier
spec_version
is '2.0'
ii.
Within the objects array, at least one;
1.
identity for the organization of the Producer
2.
sighting with the observed data for the Indicator identified in
the pattern parameter
b.
The Identity object must conform to mandatory attributes within the
Identity object spec including 'type'; 'name'; 'identity_class' and 'id'
where
i.
type is identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to share associated
with the sighting
c.
The Sighting object must conform to mandatory attributes of sighting
including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; 'pattern''
where
i.
created_by_ref must point to the identity of the Producer;
ii.
created must match the original creation timestamp to
millisecond granularity of when the user selected the Observed Data object
shared previously
iii.
modified must match the new modified timestamp to millisecond
granularity of when the Sighting was updated with new Observed Data
iv.
count must be changed from the previously shared Sighting
v.
last_observed timestamp must be updated for the new sighting
information
|
2.4.7 Producer Test Case
Modification Data
The following subsections provide the test case data for the
test.
2.4.7.1 Modification of
an Indicator with Identity and Date
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"name":
"Bad IP1",
"description":
"IPv4 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-18T13:04:22.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value = '198.51.100.1' OR ipv4-addr:value =
'198.51.100.2']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.7.1 Modification of an Indicator with Identity and Date",
}
]
2.4.7.2 Modification of
a Sighting with Identity and Date
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--ee20065d-2555-424f-ad9e-0f8428623c75",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-18T13:04:22.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-07T09:14:26.000Z",
"count": 52,
"sighting_of_ref":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"observed_data_refs":
["observed-data--455d15c6-415a-4008-addf-8a4405ede887"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.7.2 Modification of a Sighting with Identity and Date",
},
{
"type":
"observed-data",
"id":
"observed-data--455d15c6-415a-4008-addf-8a4405ede887",
"created_by_ref": "identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-18T13:04:22.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-07T09:14:26.000Z",
"number_observed": 52,
"objects": {
"0": {
"type":
"ipv4-addr",
"value":
"198.51.100.1"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.7.2 Modification of a Observed Data with Identity and Date",
}
]
2.4.8 Required
Respondent Modification Support
The Respondent must be able to parse and display the
creation; modification dates as well as the changed field of the objects
received.
Table 8 Producer Object Bundling Details
|
Persona
|
Behavior
|
|
All Indicator Respondent
personas
|
1.
Respondent allows a user to receive a STIX Bundle with an
a.
Identity and Indicator with pattern content
b.
Identity of the producer
c.
Indicator information contained in it
2.
Once received the Respondent is able to display to the user the source
of the indicator based on the identity's attribute 'name' and the identity_class
attribute
3.
For each Indicator, the Respondent is able to verify that the created_by_ref
maps to an existing identity received or one contained within the bundle
received
4.
For each Indicator, the Respondent may show the creation and modified
dates for them.
|
|
All Sighting Respondent
personas
|
1.
Respondent allows a user to receive a STIX bundle with a(n)
a.
Identity and Sighting with pattern content
b.
Identity of the Producer
c.
Sighting information contained in it
2.
Once received the Respondent is able to display to the user the source
of the Sighting based on the identity's attribute 'name' and the identity_class
attribute
3.
For each Sighting of Observed Data, the Respondent is able to verify
that the created_by_ref maps to an existing Identity received or one
contained within the Bundle received
4.
For each Sighting, the Respondent may show the creation and modified
dates for them.
|
2.4.9 Respondent Test
Case Modification Data
This test case is primarily testing the production of an
Indicator; its related version information and a Respondent's ability to parse
and represent the data correctly. No other data is sent from the Respondent
back to the Producer.
2.4.10 Required Producer
Persona Revocation Support
The Producer persona must be able to create a STIX Bundle
with one or more objects with the appropriate date representing when the object
was revoked for sharing.
The producer persona has identified a STIX object that they
wish to update as revoked and re-share to Respondents.
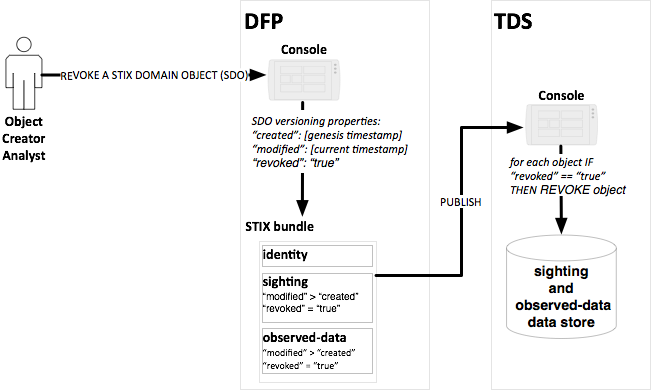
Figure 7 -
An analyst revokes a STIX sighting object and its related observed data
Table 9 - Producer Object Bundling Details
|
Persona
|
Behavior
|
|
All Indicator Producer personas
|
1.
Producer allows a user to select a previously shared Indicator that is
no longer valid and wishes to delete that Indicator.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A Bundle object must conform to mandatory attributes within the Bundle
object including 'type'; 'id'; 'spec_version' and 'objects' where
i.
id has a globally unique identifier
ii.
spec_versionis '2.0'
iii.
Within the objects array, at least one;
1.
Identity for the organization of the Producer
2.
Indicator with the IP Address identified in the pattern
parameter
b.
The Identity object must conform to mandatory attributes within the
Identity object spec including 'type'; 'name'; 'identity_class' and 'id'
where
i.
type is Identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to
share associated with the Indicator
c.
The Indicator object must conform to mandatory attributes of Indicator
including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; 'pattern''
where
i.
created_by_ref must point to the identity of the original
Producer;
ii.
created must match the original creation timestamp to
millisecond granularity of when the user selected the IP address to be an IOC
iii.
modified must match the last modified timestamp to millisecond
granularity of when the user updated the indicator to be revoked.
iv.
revoked must be set to true.
|
|
All Sighting Producer Personas
|
1.
Producer allows a user to select a previously shared Sighting (and associated
observed data) that is no longer valid and wishes to delete that sighting.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A Bundle object must conform to mandatory attributes within the bundle
object including 'type'; 'id'; 'spec_version' and 'objects' where
i.
id has a globally unique identifier
ii.
spec_versionis '2.0'
iii.
Within the objects array, at least one
1.
identity for the organization of the Producer
2.
sighting and associated observed_data object
b.
The Identity object must conform to mandatory attributes within the
object specification including 'type'; 'name'; 'identity_class' and 'id'
where
i.
type is Identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to share
associated with the Sighting and Observed Data
c.
The Sighting object must conform to mandatory attributes of indicator
including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; ‘revoked’
where
i.
created_by_ref must point to the Identity of the original
Producer;
ii.
created must match the original creation timestamp to
millisecond granularity of when the user selected the Sighting to be shared
iii.
modified must match the last modified timestamp to millisecond
granularity of when the user updated the Sighting to be revoked when the
revoked property was set to true.
iv.
revoked must be set to true.
v.
The previously shared optional Sighting attributes such as first_seen,
last_seen, count ...etc may not be included in the object
d.
The observed_data object must conform to mandatory attributes of
Indicator including 'type'; 'id'; 'created_by_ref'; 'created'; 'modified';
revoked where
i.
created_by_ref must point to the Identity of the original
Producer;
ii.
created must match the original creation timestamp to
millisecond granularity of when the user selected the observed_data to be
shared
iii.
modified must match the last modified timestamp to millisecond
granularity of when the user updated the observed_data to be revoked.
iv.
revoked must be set to true.
v.
The previously shared optional Observed Data attributes such as
objects may not be included in the object
|
2.4.11 Producer Test
Case Revocation Data
The following subsections provide the test case data for the
test.
2.4.11.1 Deletion of an
Indicator with Identity; Dates
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"name":
"Bad IP1",
"description":
"IPv4 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-18T14:24:56.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"revoked": true,
"labels":
["malicious-activity"],
"pattern":
"[ipv4-addr:value = '198.51.100.1' OR ipv4-addr:value =
'198.51.100.2']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.11.1 Deletion of an Indicator with Identity; Dates",
}
]
2.4.11.2 Deletion of a
Sighting and Associated Observed Data
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"sighting",
"id":
"sighting--ee20065d-2555-424f-ad9e-0f8428623c75",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-18T14:24:56.000Z",
"revoked": true,
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-07T09:14:26.000Z",
"count": 52,
"sighting_of_ref":
"indicator--12fd1bad-8306-4ed4-8c9b-7dfdd8ad5eb8",
"observed_data_refs":
["observed-data--455d15c6-415a-4008-addf-8a4405ede887"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"]
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.11.2 Deletion of a Sighting and Associated Observed Data",
},
{
"type":
"observed-data",
"id":
"observed-data--455d15c6-415a-4008-addf-8a4405ede887",
"created_by_ref": "identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-18T14:24:56.000Z",
"revoked": true,
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-07T09:14:26.000Z",
"number_observed": 52,
"objects": {
"0": {
"type":
"ipv4-addr",
"value":
"198.51.100.1"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.4.11.2 Deletion of a Sighting and Associated Observed Data",
}
]
2.4.12 Required
Respondent Revocation Support
The Respondent must be able to parse and display the
creation; modification dates and revoked field of the objects received.
Table 10 - Respondent Object Bundling Details
|
Persona
|
Behavior
|
|
All Indicator Respondent
Personas
|
1.
Respondent allows a user to receive a STIX Bundle with an
a.
Identity and Indicator with indicator content
b.
Identity of the Producer
c.
Indicator with pattern information contained in it
2.
Once received the Respondent is able to display to the user the source
of the Indicator based on the identity's attribute 'name' and the identity_class
attribute
3.
For each Indicator, the Respondent is able to verify that the created_by_ref
maps to an existing Identity received or one contained within the Bundle
received
4.
For each Indicator, the Respondent may show the creation and
modified dates for them.
|
|
All Sighting Respondent
Personas
|
1.
Respondent allows a user to receive a STIX bundle with a(n)
a.
Identity and sighting & observed_data content
b.
Identity of the Producer
c.
Sighting with associated observed_data object
2.
Once received the Respondent is able to display to the user the
source of the sighting based on the Identity's attribute 'name' and
the identity_class attribute
3.
For each sighting & observed_data the Respondent is
able to verify that the created_by_ref maps to an existing Identity
received or one contained within the Bundle received
4.
For each Sighting, the Respondent may show the creation and
modified dates for them and that the object has been revoked.
|
2.4.13 Respondent Test
Case Revocation Data
This test case is primarily testing
the production of an Indicator or Sighting, its related version information,
and a Respondent's ability to parse and represent the data correctly. No other
data is sent from the Respondent back to the producer.
2.5 Data Markings
2.5.1 Description
A STIX 2.0 Producer or Respondent must support markings
applied to objects and the related operations around them. The Data Markings
test cases focus on how markings should be represented. How consumers mitigate
markings and their related Indicator(s) is not prescribed in this
specification. Data Markings can be produced at an object level and at an
attribute level. Data Markings at the attribute level are known as granular
markings.
This section describes basic tests for assigning Data
Markings to shared data using the traffic light protocol (TLP). “TLP is a set of
designations used to ensure that sensitive information is shared with the
appropriate audience.” It is defined
by a Forum of Incident Response and Security Teams (FIRST) Special Interest
Group (SIG).
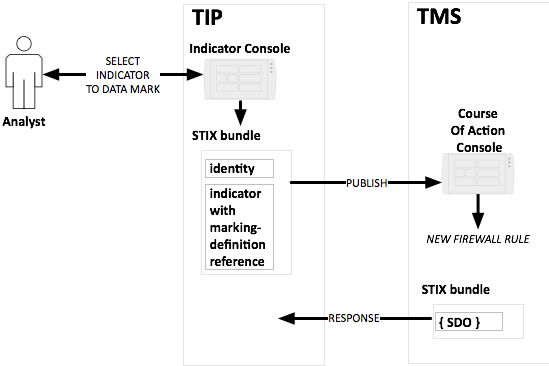
Figure 8 -
An analyst marks an indicator with a TLP designation
2.5.2 Required Producer
Persona Support
For these test cases, STIX TLP
data markings must be accompanied by at least one Indicator. The producer
persona must be able to create a STIX bundle with one or more Indicators as
identified by the Indicator Sharing Producer Test Case Data. All personas defined in Indicator Sharing Required Producer Persona Support are also defined for Data Markings producer personas.
Producers should allow users to
create marking-definitions and apply object level markings to an SDO or SRO at
all TLP levels.
Table 11 - Producer Object Bundling Details
|
Persona
|
Behavior
|
|
DFP; TIP
|
1.
Producer allows a user or an administrator
to apply object level markings to a variety of Indicators that are being
shared.
2.
Producer may provide TLP object
level markings at any level.
a.
Producer verifies that objects to
be marked do exist in the bundle.
b.
Producer must NOT mark Indicator
objects with more than one TLP level markings.
3.
The Producer creates the marking-definition
object for the request:
a.
For different objects, the user can
apply different TLP levels including: tlp “green”; tlp “amber”;
tlp “red”; tlp “white”.
b.
The marking-definition must conform to its mandatory
UUID references including:
i.
marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9
if tlp “white”
ii.
marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da
if tlp “green”
iii.
marking-definition--f88d31f6-486f-44da-b317-01333bde0b82
if tlp “amber”
iv.
marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed
if tlp “red”
4.
The SDO object_marking_refs list
of marking-definition is populated with markings created by Producer
and the id that matches the intended TLP marking.
|
2.5.3 Producer Test Case
Data
The following subsections provide the test case data for the
test. In all cases the data markings referenced by the other objects in the
content are using the TLP predefined constants.
2.5.3.1 TLP Green +
Indicator with IPv4 Address
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"name":
"Bad IP1",
"id":
"indicator--8e2e2d2b-17d4-4cbf-938f-98ee46b3cd3f",
"description":
"IPv4 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"object_marking_refs":
["marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"],
"pattern":
"[ipv4-addr:value = '198.51.100.1']"
"x_interop_test": "STIX/TAXII
2.0 Interoperability Part 1, §2.5.3.1 TLP Green + Indicator with IPv4 Address",
}
]
2.5.3.2 TLP Amber + Two
Indicators with IPv4 Address CIDR
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class":
"organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--2713b690-877e-4d25-a992-6e80efefa49f",
"name":
"Bad IP Subnets",
"description":
"IPv4 CIDR Indicator",
"created_by_ref": "identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"object_marking_refs":
["marking-definition--f88d31f6-486f-44da-b317-01333bde0b82"],
"pattern":
"[ipv4-addr:value ISSUBSET '198.51.100.0/24' OR ipv4-addr:value ISSUBSET
'196.45.200.0/24']"
"x_interop_test": "STIX/TAXII
2.0 Interoperability Part 1, §2.5.3.2 TLP Amber + Two Indicators with IPv4
Address CIDR",
}
]
2.5.3.3 TLP White and
TLP Red + Indicator with IPv6 Address
"objects": [
{
"type": "identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
"object_marking_refs": ["marking-definition--613f2e26-407d-48c7-9eca-b8e91df99dc9"]
},
{
"type":
"indicator",
"id":
"indicator--c6b3dbc6-f279-4193-90c2-2967a0a16485",
"name":
"Bad IPv6-1",
"description":
"IPv6 Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[ipv6-addr:value = '2001:0db8:85a3:0000:0000:8a2e:0370:7334']",
"object_marking_refs":
["marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed"]
"x_interop_test": "STIX/TAXII
2.0 Interoperability Part 1, §2.5.3.3 TLP White and TLP Red + Indicator with
IPv6 Address",
}
]
2.5.3.4 TLP Red +
Sighting and Indicator
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class":
"organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id": "indicator--3b9cc57a-1026-4622-9ffb-56cdab6bd4aa",
"name":
"Bad IP CIDR",
"description":
"IPv4 CIDR Indicator",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"object_marking_refs":
["marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed"],
"pattern":
"[ipv4-addr:value ISSUBSET '198.51.100.12/24']"
"x_interop_test": "TIX/TAXII
2.0 Interoperability Part 1, §2.5.3.4 TLP Red + Sighting and Indicator",
},
{
"type":
"sighting",
"id":
"sighting--038992fa-a727-4f2d-9bdf-256a95c1ce8c",
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.5.3.4 TLP Red + Sighting and Indicator",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_seen":
"2017-12-21T19:00:00.000Z",
"last_seen":
"2018-01-06T19:00:00.000Z",
"count": 50,
"sighting_of_ref":
"indicator--3b9cc57a-1026-4622-9ffb-56cdab6bd4aa",
"observed_data_refs":
["observed-data--857d8389-9b7a-4ce8-a2ee-b0bf225dcfba"],
"where_sighted_refs":
["identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb"],
"object_marking_refs":
["marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed"]
},
{
"type":
"observed-data",
"id":
"observed-data--857d8389-9b7a-4ce8-a2ee-b0bf225dcfba",
"created_by_ref":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"first_observed": "2017-12-21T19:00:00.000Z",
"last_observed":
"2018-01-06T19:00:00.000Z",
"number_observed": 1,
"object_marking_refs":
["marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed"],
"objects": {
"0": {
"type":
"ipv4-addr",
"value":
"198.51.100.1"
}
}
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.5.3.4 TLP Red + Sighting and Indicator",
}
]
2.5.4 Required
Respondent Support
The Respondent must be able to
parse and display any Indicator that has been shared with IP Address
information and data markings, if present. All required Respondent support
defined in 2.2.4 Required Respondent Support also applies to Data Markings.
Table 12 - Respondent Object Bundling Details
|
Persona
|
Behavior
|
|
TIP; SIEM
|
1.
Respondent receives the STIX bundle
with
a.
A Bundle the various required field
pattern content as follows
i.
An Identity of the producer
ii.
An Indicator with various
required fields
iii.
An Indicator with data
markings applied
iv.
The Indicator’s object_marking_refs, must be associated with a correct marking
definition
v.
If the Indicator identifies
a marking-definition object that does not exist, then the Respondent should
reject the Indicator
2.
Once received the Respondent can
display to the user the source of the Indicator based on the Identity's
attribute 'name' and the identity_class attribute
3.
For each Indicator object
the Respondent is able to verify that the created_by_ref maps to an
existing Identity received or one contained within the bundle received
4.
For each set of objects, the
Respondent must display or filter the objects based on the associated Data
Markings applied to that object. This ensures that the user accessing the
set of objects has appropriate marking authorization for TLP green, TLP
amber, TLP red and TLP white depending on the test case performed.
|
2.6 Custom Objects and
Properties
2.6.1 Description
If an organization produces or consumes custom STIX objects
or properties, the following tests verify that the capability is done
correctly.
2.6.2 Required Producer
Persona Support
The Producer persona must be able to create a STIX Bundle
with one or more objects with the appropriate date representing when the object
was created for sharing.
NOTE: Not all personas defined in this specification create Indicators.
Table 13 - Producer Object Bundling Details
|
Persona
|
Behavior
|
|
All Producer personas that
generate custom objects
|
1.
Producer allows a user to select or specify the STIX custom object
content to send to a Respondent persona.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A Bundle object must conform to mandatory attributes within the
bundle object including 'type'; 'id'; 'spec_version' and
'objects' where
i.
type is Bundle
ii.
id has a globally unique identifier
iii.
spec_versionis '2.0'
iv.
Within the objects array
1.
at least one Identity for the organization of the Producer
2.
at least one custom object where the custom object type
name is prefixed with “x-”
b.
The Identity object must conform to mandatory attributes within
the identity object spec including the following:
i.
type is identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to share associated
with the custom object
c.
The custom object must conform to mandatory attributes including
'type'; 'id'; 'created_by_ref'; 'created'; 'modified'; and one or more custom
attributes where
i.
created_by_ref must point to the identity of the Producer;
ii.
created and modified must match the timestamp to
millisecond granularity of when the user selected the custom object
|
|
All Producer personas that
generate custom properties on SDOs
|
1.
Producer allows a user to select or specify the STIX SDO object
content to send to a Respondent persona including the custom property
associated with the SDO.
2.
The following data must be verified in the STIX produced by the
persona:
a.
A Bundle object must conform to mandatory attributes within the
bundle object including:
i.
type is Bundle
ii.
id has a globally unique identifier
iii.
spec_versionis '2.0'
iv.
Within the objects array
1.
at least one Identity for the organization of the Producer
2.
at least one STIX SDO with at least 1 custom property prefixed
with “x_”
b.
The Identity object must conform to mandatory attributes within
the identity object spec including:
i.
type is identity
ii.
id has a globally unique identifier
iii.
identity_class is specified by the organization of the Producer
iv.
name is the name that the Producer wishes to share associated
with the SDO
c.
The custom object property must conform to mandatory attributes
including 'type'; 'id'; 'created_by_ref'; 'created';
'modified'; and include one or more custom properties where
i.
created_by_ref must point to the identity of the Producer;
ii.
created and modified must match the timestamp to
millisecond granularity of when the user selected the custom object
iii.
x-{custom property name} exists
|
2.6.3 Producer Test Case
Data
The following subsections provide the test case data for the
test.
2.6.3.1 Custom Object
Creation
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"x-example-com-customobject",
"id":
"x-example-com-customobject--0d7fe7d9-13b5-4a52-b1db-00eaf89f984d",
"description":
"Custom Object",
"created_by_ref": "identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"some_custom_stuff": 14,
"other_custom_stuff": "hello"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.6.3.1 Custom Object Creation",
}
]
2.6.3.2 Custom Property
Creation
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"indicator",
"id":
"indicator--2ac04b47-a639-4769-b29a-e65c2956c418",
"name":
"Bad IP1",
"description":
"Custom Property",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"x_acme_custom_property": 10,
"pattern":
"[ipv4-addr:value = '198.51.100.1']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.6.3.2 Custom Property Creation",
}
]
2.6.4 Required
Respondent Support
A Respondent receiving custom objects or properties must
conform to the following tests.
Table 14 - Respondent Object Bundling Details
|
Persona
|
Behavior
|
|
All Respondent Personas that
may receive custom objects
|
1.
Respondent receives a STIX Bundle with
a.
A Bundle with an Identity and custom object or custom
properties on standard STIX object
2.
Once received the Respondent is able to display to the user the source
of the Indicator based on the Identity's attribute 'name' and
the identity_class attribute
3.
For each custom object, the Respondent must be able to determine that
it is a custom object and not a SDO and can verify that the created_by_ref
maps to an existing Identity received or one contained within the bundle
received.
4.
Respondent must be able to ingest all other SDOs in the Bundle
5.
If the Respondent supports the custom object, then for each custom
object, the Respondent may show the creation and modified dates for them. If
the Respondent does not support the custom object, then the Respondent’s
console should be able to continue servicing the user without crashing, and
support remaining SDOs in the Bundle.
|
|
All Respondent Personas that
may receive custom properties
|
1.
Respondent receives a STIX Bundle with
a.
an Identity and
b.
SDO with custom properties
2.
Once received the Respondent is able to display to the user the source
of the SDO based on the identity's attribute 'name' and the identity_class
attribute
3.
For each SDO the Respondent must be able to determine that it is a SDO
and able to ingest/parse all mandatory fields.
4.
If the Respondent supports the custom property, then they may show or
use the custom property included in the SDO.
5.
If the Respondent does not support the custom property, then the
Respondent may discard or show to the user that the SDO has been rejected.
The Respondent’s console should be able to continue servicing the user
without crashing, and support remaining SDOs in the Bundle.
|
2.6.5 Respondent Test
Case Data
This test case is primarily testing the production of custom
objects, its related core property information, and a Respondent's ability to
parse and ingest (not reject) all content that may be bundled with SDOs. No
data is sent from the Respondent back to the Producer.
2.7 Course Of Action
Sharing
2.7.1 Description
A Course of Action (COA) is a recommendation to respond to
some form of threat. Typically, a COA would be created as a separate object
that is then connected to other intelligence objects that, when detected, can
be mitigated by the playbook sequencing called by the COA object.
However, the COA object in STIX 2.0 is a stub. It is
included to support basic test cases (such as sharing prose courses of action)
but, at this time, it does not support the ability to represent automated
courses of action or contain properties to represent metadata about courses of
action.
The COA SDO primarily focuses on a textual description of
the mitigating action.
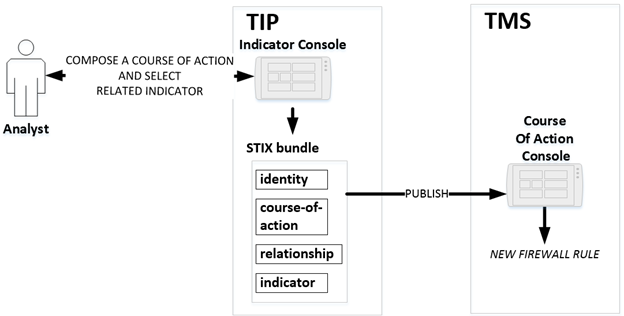
Figure 9 -
Sharing Course Of Action
2.7.2 Required Producer
Persona Support
The Producer must be able to populate the ‘name’ and ‘description’
with the textual information for the mitigating action to perform.
Table 15 - Producer Object Bundling Details
|
Personas
|
Behavior
|
|
All Course of Action producer
personas
|
1.
Producer allows a user to select or specify the STIX content to send
to a Respondent persona.
2.
The following data must be verified in the STIX produced by the
persona:
a)
A Bundle object must conform to mandatory attributes within the
Bundle object including:
i)
id has a globally unique identifier
ii)
spec_version is '2.0'
iii)
Within the objects array
1)
at least one identity for the organization of the Producer
2)
at least one course of action with the required fields
populated
b)
The Identity object must conform to mandatory attributes within
the Identity object spec including:
i)
type is 'identity'
ii)
id has a globally unique identifier
iii)
identity_class is specified by the organization of the Producer
iv)
name is the name that the Producer wishes to share
c)
The course-of-action object must conform to its mandatory
attributes including 'type', 'id', and the following where
i)
created_by_ref must point to the identity of the Producer;
ii)
created and modified must match the timestamp to
millisecond granularity of when the user created the object
iii)
name that assigns a title to the course-of-action
iv)
description that provides more details and context about the course-of-action,
potentially including its purpose and its key characteristics.
|
2.7.3 Producer Test Case
Data
The following subsections provide the test case data for the
test.
2.7.3.1 Create COA
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"course-of-action",
"id":
"course-of-action--97250bf1-7ab6-4c79-b8c0-b59f6fc62e9d",
"name":
"Add TCP port 80 Filter Rule to the existing Block UDP 1434 Filter",
"description":
"Course Of Action",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
"x_interop_test":
"STIX/TAXII 2.0 Interoperability Part 1, §2.7.3.1 Create COA",
}
]
2.7.3.2 Create COA with
Relationship
"objects": [
{
"type":
"identity",
"id":
"identity--f6e43aa5-76cc-45ca-9b06-be2d65f26bfb",
"identity_class": "organization",
"name":
"ACME Corp Sighting, Inc.",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
},
{
"type":
"course-of-action",
"id":
"course-of-action--17ce1618-0aab-4366-a93a-9d290282995e",
"name":
"Add TCP port 80 Filter Rule to the existing Block UDP 1434 Filter",
"description":
"COA Relationship",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z"
"x_interop_test":
"STIX/TAXII 2.0 Interoperability Part 1, §2.7.3.2 Create COA with
Relationship",
},
{
"type":
"relationship",
"id":
"relationship--1d79e2b8-c4e2-4f64-a9b3-739de42bc1c6",
"created_by_ref": "identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"source_ref":
"course-of-action--17ce1618-0aab-4366-a93a-9d290282995e",
"target_ref":
"indicator--bc7a2301-d711-465d-a8bf-97d50e1cb68f",
"relationship_type": "related-to"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.7.3.2 Create COA with Relationship",
},
{
"type":
"indicator",
"id":
"indicator--bc7a2301-d711-465d-a8bf-97d50e1cb68f",
"name":
"Poison Ivy Malware",
"description":
"Hash Indicator",
"created_by_ref":
"identity--f431f809-377b-45e0-aa1c-6a4751cae5ff",
"created":
"2018-01-17T11:11:13.000Z",
"modified":
"2018-01-17T11:11:13.000Z",
"valid_from":
"2018-01-01T00:00:00.000Z",
"labels":
["malicious-activity"],
"pattern":
"[file:hashes.MD5 = '3773a88f65a5e780c8dff9cdc3a056f3']"
"x_interop_test": "STIX/TAXII 2.0 Interoperability Part 1,
§2.7.3.2 Create COA with Relationship",
}
]
2.7.4 Required
Respondent Persona Support
The Respondent must be able to parse and display all
COA Properties.
Table 16 - Respondent Object Bundling Details
|
Persona
|
Behavior
|
|
All Course of Action Respondent
personas
|
1.
Respondent allows a user to receive a STIX Bundle with
a.
A Bundle with an Identity and course-of-action with
various content
b.
An identity of the Producer
c.
One or more course-of-action with required fields information
contained in it
2.
Once received, the Respondent is able to display to the user
the source of the course-of-action based on the Identity's attribute
'name' and the identity_class attribute
3.
For each course-of-action, the Respondent must be
able to verify that the created_by_ref maps to an existing Identity
received or one contained within the Bundle received
4.
For each course-of-action object the Respondent is able
to display the information from the course-of-action fields to the user.
|
The following checklists summarize all tests that a persona
(Producer or Respondent) must conform to within that persona. An organization
must submit the results for their specific persona(s) to the OASIS CTI TC
Interoperability SC to achieve confirmation of interoperability and to be
listed on the OASIS website page showing the organization’s compliance to STIX
2.0.
Results must be submitted to the STIX Interoperability
sub-committee for verification.
Results may be submitted as separate logs; documents;
screenshots; any other proof such that the reviewers can assess whether the
organization has confirmed compliance to STIX 2.0 interoperability tests for
their specific instance.
Instructions to organizations:
1) Fill
in the section relevant to your instance
2) For
each test, add a reference in the results column on what evidence documentation
supports compliance results.
3) Submit
both the filled in section and all supporting documentation.
After review and verification of the demonstration
submittal, the OASIS CTI TC Interoperability SC will post confirmation. Our
listing will include the following:
1. Name,
address and contact information of the company performing the demonstration
2. Name
of the conforming product
3. Summary
of the references that substantiate interoperability conformance.
No independent testing will be performed directly by the
Interoperability SC; rather the verification process will confirm that the
documentation is complete and accurate as claimed by the submitting party.
3.1 Data Feed Provider
(DFP)
For the purpose of this document a DFP is a software
instance that acts as a Producer of STIX 2.0 content.
Any instance being qualified as a DFP must confirm test
results for the following test cases.
Table 17 - Data Feed Provider (DFP) Test Verification List
|
test
case
|
Test
|
Verification
|
Results
|
|
Indicator Sharing
|
2.2.3.1 Indicator IPv4 Address
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.2 Indicator IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.3 Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.4 Indicator with IPv6 Address
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.5 Indicator with IPv6 Address CIDR
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.6 Multiple Indicators within the same bundle
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.7 Indicator FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.8 Indicator URL
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.9 Indicator URL or FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.10 Indicator File hash with SHA256 or MD5 values
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.3 Producer Test Case Data
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.1 Sighting + Indicator with IPv4 Address
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.2 Sighting + Indicator with IPv4 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.3 Sighting + Indicator with IPv6 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.4 Sighting + Indicator with NO observed data
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.5 Sighting + Indicator with URL
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.6 Sighting + Indicator with File Hash
|
Optional
|
<if supported, fill in>
|
|
Versioning
|
2.4.3.1 Creation of an Indicator with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.2 Creation of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.1 Modification of an Indicator with Identity
and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.2 Modification of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.1 Deletion of an Indicator with Identity; Dates
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.2 Deletion of a Sighting and Associated Observed
Data
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.1 TLP Green + Indicator with IPv4 Address
|
Optional
|
<fill in>
|
|
Data Markings
|
2.5.3.2 TLP Amber + Two Indicators with IPv4 Address CIDR
|
Optional
|
<fill in>
|
|
Data Markings
|
2.5.3.3 TLP White and TLP Red + Indicator with IPv6
Address
|
Optional
|
<if supported, fill in>
|
|
Data Markings
|
2.5.3.4 TLP Red + Sighting and Indicator
|
Optional
|
<if supported, fill in>
|
|
Custom Object Creation
|
2.6.3.1 Custom Object Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Property Creation
|
2.6.3.2 Custom Property Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Ingestion
|
2.6.4 Required Respondent Support
|
n/a
|
n/a
|
|
Create COA
|
2.7.3.1 Create COA
|
Optional
|
<if supported, fill in>
|
|
Create COA Relationship
|
2.7.3.2 Create COA with Relationship
|
Optional
|
<if supported, fill in>
|
3.2 Threat Intelligence
Platform (TIP)
For the purpose of this document a TIP is defined as a
software instance that acts as a Producer and/or Respondent of STIX 2.0 content
primarily used to aggregate, refine and share intelligence with other machines
or security personnel operating other security infrastructure.
Any instance being qualified as a TIP must confirm test
results for the following test cases.
Table 18 - Threat Intelligence Platform (TIP) Test Verification
List
|
test
case
|
Test
|
Verification
|
Results
|
|
Indicator Sharing
|
2.2.3.1 Indicator IPv4 Address
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.2 Indicator IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.3 Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.4 Indicator with IPv6 Address
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.5 Indicator with IPv6 Address CIDR
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.6 Multiple Indicators within the same bundle
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.7 Indicator FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.8 Indicator URL
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.9 Indicator URL or FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.10 Indicator File hash with SHA256 or MD5 values
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.3 Producer Test Case Data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.1 Sighting + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.2 Sighting + Indicator with IPv4 Address Matching
CIDR
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.3 Sighting + Indicator with IPv6 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.4 Sighting + Indicator with NO observed data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.5 Sighting + Indicator with URL
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.6 Sighting + Indicator with File Hash
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.1 Creation of an Indicator with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.2 Creation of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.1 Modification of an Indicator with Identity
and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.2 Modification of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.1 Deletion of an Indicator with Identity; Dates
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.2 Deletion of a Sighting and Associated Observed
Data
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.1 TLP Green + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.2 TLP Amber + Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.3 TLP White and TLP Red + Indicator with IPv6
Address
|
Optional
|
<if supported, fill in>
|
|
Data Markings
|
2.5.3.4 TLP Red + Sighting and Indicator
|
Optional
|
<if supported, fill in>
|
|
Custom Object Creation
|
2.6.3.1 Custom Object Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Property Creation
|
2.6.3.2 Custom Property Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Ingestion
|
2.6.4 Required Respondent Support
|
Mandatory
|
<fill in>
|
|
Create COA
|
2.7.3.1 Create COA
|
Optional
|
<if supported, fill in>
|
|
Create COA Relationship
|
2.7.3.2 Create COA with Relationship
|
Optional
|
<if supported, fill in>
|
3.3 Security Incident
and Event Management (SIEM)
For the purpose of this document a SIEM is a software
instance that acts as a Producer and/or Respondent of STIX 2.0 content. The
primary Respondent role of a SIEM is report Indicators and other high-level information.
The Producer SIEM primarily reports Indicators.
Any instance being qualified as a SIEM must confirm test
results for the following test cases.
Table 19 - Security Incident and Event Management (SIEM) Test
Verification List
|
test
case
|
Test
|
Verification
|
Results
|
|
Indicator Sharing
|
2.2.3.1 Indicator IPv4 Address
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.2 Indicator IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.3 Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.4 Indicator with IPv6 Address
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.5 Indicator with IPv6 Address CIDR
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.6 Multiple Indicators within the same bundle
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.7 Indicator FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.8 Indicator URL
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.9 Indicator URL or FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.10 Indicator File hash with SHA256 or MD5 values
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.3 Producer Test Case Data
|
Optional
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.1 Sighting + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.2 Sighting + Indicator with IPv4 Address Matching
CIDR
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.3 Sighting + Indicator with IPv6 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.4 Sighting + Indicator with NO observed data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.5 Sighting + Indicator with URL
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.6 Sighting + Indicator with File Hash
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.1 Creation of an Indicator with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.2 Creation of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.1 Modification of an Indicator with Identity
and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.2 Modification of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.1 Deletion of an Indicator with Identity; Dates
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.2 Deletion of a Sighting and Associated Observed
Data
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.1 TLP Green + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.2 TLP Amber + Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.3 TLP White and TLP Red + Indicator with IPv6
Address
|
Optional
|
<fill in>
|
|
Data Markings
|
2.5.3.4 TLP Red + Sighting and Indicator
|
Optional
|
<fill in>
|
|
Custom Object Creation
|
2.6.3.1 Custom Object Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Property Creation
|
2.6.3.2 Custom Property Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Ingestion
|
2.6.4 Required Respondent Support
|
Mandatory
|
<fill in>
|
|
Create COA
|
2.7.3.1 Create COA
|
Optional
|
<if supported, fill in>
|
|
Create COA Relationship
|
2.7.3.2 Create COA with Relationship
|
Optional
|
<if supported, fill in>
|
3.4 Threat Mitigation
System (TMS)
For the purpose of this document a TMS is a software
instance that mitigates threats in a network. It may act as both a Producer and
Respondent some test cases. The Respondent TMS primarily reports Indicators.
The Producer TMS primarily reports Sightings.
Any instance being qualified as a TMS must confirm test
results for the following test cases.
Table 20 - Threat Mitigation System (TMS) Test Verification List
|
test
case
|
Test
|
Verification
|
Results
|
|
Indicator Sharing
|
2.2.3.1 Indicator IPv4 Address
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.2 Indicator IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.3 Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.4 Indicator with IPv6 Address
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.5 Indicator with IPv6 Address CIDR
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.6 Multiple Indicators within the same bundle
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.7 Indicator FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.8 Indicator URL
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.9 Indicator URL or FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.10 Indicator File hash with SHA256 or MD5 values
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.3 Producer Test Case Data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.1 Sighting + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.2 Sighting + Indicator with IPv4 Address Matching
CIDR
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.3 Sighting + Indicator with IPv6 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.4 Sighting + Indicator with NO observed data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.5 Sighting + Indicator with URL
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.6 Sighting + Indicator with File Hash
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.1 Creation of an Indicator with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.2 Creation of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.1 Modification of an Indicator with Identity
and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.2 Modification of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.1 Deletion of an Indicator with Identity; Dates
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.2 Deletion of a Sighting and Associated Observed
Data
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.1 TLP Green + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.2 TLP Amber + Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.3 TLP White and TLP Red + Indicator with IPv6
Address
|
Optional
|
<fill in>
|
|
Data Markings
|
2.5.3.4 TLP Red + Sighting and Indicator
|
Optional
|
<fill in>
|
|
Custom Object Creation
|
2.6.3.1 Custom Object Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Property Creation
|
2.6.3.2 Custom Property Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Ingestion
|
2.6.4 Required Respondent Support
|
Mandatory
|
<fill in>
|
|
Create COA
|
2.7.3.1 Create COA
|
Optional
|
<if supported, fill in>
|
|
Create COA Relationship
|
2.7.3.2 Create COA with Relationship
|
Optional
|
<if supported, fill in>
|
3.5 Threat Detection System
(TDS)
For the purpose of this document a TDS detects threats in a
network without necessarily mitigating the threat. It may act as both a
Producer and Respondent depending on the type of test case. The Respondent is
primarily concerned with Indicators. The Producer role is primarily concerned
with Sightings.
Any instance being qualified as a TDS must confirm test
results for the following test cases.
Table 21 - Threat Detection System (TDS) Test Verification List
|
test
case
|
Test
|
Verification
|
Results
|
|
Indicator Sharing
|
2.2.3.1 Indicator IPv4 Address
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.2 Indicator IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.3 Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.4 Indicator with IPv6 Address
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.5 Indicator with IPv6 Address CIDR
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.6 Multiple Indicators within the same bundle
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.7 Indicator FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.8 Indicator URL
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.9 Indicator URL or FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.10 Indicator File hash with SHA256 or MD5 values
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.3 Producer Test Case Data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.1 Sighting + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.2 Sighting + Indicator with IPv4 Address Matching
CIDR
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.3 Sighting + Indicator with IPv6 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.4 Sighting + Indicator with NO observed data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.5 Sighting + Indicator with URL
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.6 Sighting + Indicator with File Hash
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.1 Creation of an Indicator with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.2 Creation of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.1 Modification of an Indicator with Identity
and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.2 Modification of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.1 Deletion of an Indicator with Identity; Dates
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.2 Deletion of a Sighting and Associated Observed
Data
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.1 TLP Green + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.2 TLP Amber + Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.3 TLP White and TLP Red + Indicator with IPv6
Address
|
Optional
|
<fill in>
|
|
Data Markings
|
2.5.3.4 TLP Red + Sighting and Indicator
|
Optional
|
<fill in>
|
|
Custom Object Creation
|
2.6.3.1 Custom Object Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Property Creation
|
2.6.3.2 Custom Property Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Ingestion
|
2.6.4 Required Respondent Support
|
Mandatory
|
<fill in>
|
|
Create COA
|
2.7.3.1 Create COA
|
Optional
|
<if supported, fill in>
|
|
Create COA Relationship
|
2.7.3.2 Create COA with Relationship
|
Optional
|
<if supported, fill in>
|
3.6 Threat Intelligence
Sink (TIS)
For the purpose of this document, a (TIS) is a software instance
that consumes STIX 2.0 content in order to perform translations to domain
specific formats. Those translations are consumable by enforcement and/or
detection systems that do not natively support STIX 2.0. These TIS consumers
may or may not have the capability of reporting sightings. A (TIS) that
consumes STIX content will typically consume indicators.
Any software instance being qualified as a (TIS) must
confirm test results for the following test cases.
Table 22 - Threat Intelligence Sink (TIS) Test Verification List
|
test
case
|
Test
|
Verification
|
Results
|
|
Indicator Sharing
|
2.2.3.1 Indicator IPv4 Address
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.2 Indicator IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.3 Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.4 Indicator with IPv6 Address
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.5 Indicator with IPv6 Address CIDR
|
Optional
|
<if supported, fill in>
|
|
Indicator Sharing
|
2.2.3.6 Multiple Indicators within the same bundle
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.7 Indicator FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.8 Indicator URL
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.9 Indicator URL or FQDN
|
Mandatory
|
<fill in>
|
|
Indicator Sharing
|
2.2.3.10 Indicator File hash with SHA256 or MD5 values
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.3 Producer Test Case Data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.1 Sighting + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.2 Sighting + Indicator with IPv4 Address Matching
CIDR
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.3 Sighting + Indicator with IPv6 Address Matching
CIDR
|
Optional
|
<if supported, fill in>
|
|
Sighting Sharing
|
2.3.5.4 Sighting + Indicator with NO observed data
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.5 Sighting + Indicator with URL
|
Mandatory
|
<fill in>
|
|
Sighting Sharing
|
2.3.5.6 Sighting + Indicator with File Hash
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.1 Creation of an Indicator with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.3.2 Creation of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.1 Modification of an Indicator with Identity
and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.7.2 Modification of a Sighting with Identity and Date
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.1 Deletion of an Indicator with Identity; Dates
|
Mandatory
|
<fill in>
|
|
Versioning
|
2.4.11.2 Deletion of a Sighting and Associated Observed
Data
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.1 TLP Green + Indicator with IPv4 Address
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.2 TLP Amber + Two Indicators with IPv4 Address CIDR
|
Mandatory
|
<fill in>
|
|
Data Markings
|
2.5.3.3 TLP White and TLP Red + Indicator with IPv6
Address
|
Optional
|
<fill in>
|
|
Data Markings
|
2.5.3.4 TLP Red + Sighting and Indicator
|
Optional
|
<fill in>
|
|
Custom Object Creation
|
2.6.3.1 Custom Object Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Property Creation
|
2.6.3.2 Custom Property Creation
|
Optional
|
<if supported, fill in>
|
|
Custom Ingestion
|
2.6.4 Required Respondent Support
|
Mandatory
|
<fill in>
|
|
Create COA
|
2.7.3.1 Create COA
|
Optional
|
<if supported, fill in>
|
|
Create COA Relationship
|
2.7.3.2 Create COA with Relationship
|
Optional
|
<if supported, fill in>
|
Appendix
A Acknowledgments
Interoperability Subcommittee Chairs:
Allan Thomson,
LookingGlass,
Jason Keirstead, IBM
Additional Editors
Jane Ginn, Cyber Threat Intelligence
Network, Inc.
Special Thanks:
Substantial contributions to this specification from the
following individuals are gratefully acknowledged:
Participants:
The following individuals were members of the OASIS CTI
Technical Committee during the creation of this specification and their
contributions are gratefully acknowledged:
|
Robert
|
Coderre
|
Accenture
|
|
Kyle
|
Maxwell
|
Accenture
|
|
David
|
Crawford
|
Aetna
|
|
Marcos
|
Orallo
|
Airbus Group SAS
|
|
Roman
|
Fiedler
|
AIT Austrian Institute of Technology
|
|
Florian
|
Skopik
|
AIT Austrian Institute of Technology
|
|
Ryan
|
Clough
|
Anomali
|
|
Wei
|
Huang
|
Anomali
|
|
Angela
|
Nichols
|
Anomali
|
|
Hugh
|
Njemanze
|
Anomali
|
|
Katie
|
Pelusi
|
Anomali
|
|
Nicholas
|
Hayden
|
Anomali
|
|
Dean
|
Thompson
|
Australia and New Zealand Banking Group (ANZ Bank)
|
|
Alexander
|
Foley
|
Bank of America
|
|
Radu
|
Marian
|
Bank of America
|
|
Sounil
|
Yu
|
Bank of America
|
|
Vicky
|
Laurens
|
Bank of Montreal
|
|
Alexandre
|
Dulaunoy
|
CIRCL
|
|
Andras
|
Iklody
|
CIRCL
|
|
Christian
|
Studer
|
CIRCL
|
|
RaphaÎl
|
Vinot
|
CIRCL
|
|
Sarah
|
Kelley
|
CIS
|
|
Syam
|
Appala
|
Cisco Systems
|
|
Ted
|
Bedwell
|
Cisco Systems
|
|
David
|
McGrew
|
Cisco Systems
|
|
Mark-David
|
McLaughlin
|
Cisco Systems
|
|
Pavan
|
Reddy
|
Cisco Systems
|
|
Omar
|
Santos
|
Cisco Systems
|
|
Sam
|
Taghavi Zargar
|
Cisco Systems
|
|
Jyoti
|
Verma
|
Cisco Systems
|
|
Jart
|
Armin
|
Cyber Threat Intelligence Network, Inc. (CTIN)
|
|
Doug
|
DePeppe
|
Cyber Threat Intelligence Network, Inc. (CTIN)
|
|
Ben
|
Ottoman
|
Cyber Threat Intelligence Network, Inc. (CTIN)
|
|
David
|
Powell
|
Cyber Threat Intelligence Network, Inc. (CTIN)
|
|
Andreas
|
Sfakianakis
|
Cyber Threat Intelligence Network, Inc. (CTIN)
|
|
Jane
|
Ginn
|
Cyber Threat Intelligence Network, Inc. (CTIN)
|
|
Andrew
|
Byrne
|
Dell
|
|
Jeff
|
Odom
|
Dell
|
|
Sreejith
|
Padmajadevi
|
Dell
|
|
Ravi
|
Sharda
|
Dell
|
|
Will
|
Urbanski
|
Dell
|
|
Evette
|
Maynard-Noel
|
DHS Office of Cybersecurity and Communications (CS&C)
|
|
Sean
|
Sobieraj
|
DHS Office of Cybersecurity and Communications (CS&C)
|
|
Marlon
|
Taylor
|
DHS Office of Cybersecurity and Communications (CS&C)
|
|
Preston
|
Werntz
|
DHS Office of Cybersecurity and Communications (CS&C)
|
|
Wouter
|
Bolsterlee
|
EclecticIQ
|
|
Adam
|
Bradbury
|
EclecticIQ
|
|
Marko
|
Dragoljevic
|
EclecticIQ
|
|
Oliver
|
Gheorghe
|
EclecticIQ
|
|
Joep
|
Gommers
|
EclecticIQ
|
|
Christopher
|
O'Brien
|
EclecticIQ
|
|
Sergey
|
Polzunov
|
EclecticIQ
|
|
Rutger
|
Prins
|
EclecticIQ
|
|
Andrei
|
SÓrghi
|
EclecticIQ
|
|
Raymon
|
van der Velde
|
EclecticIQ
|
|
Tom
|
Vaughan
|
EclecticIQ
|
|
Ben
|
Sooter
|
Electric Power Research Institute (EPRI)
|
|
Chris
|
Ricard
|
Financial Services Information Sharing and Analysis Center
(FS-ISAC)
|
|
Phillip
|
Boles
|
FireEye, Inc.
|
|
Prasad
|
Gaikwad
|
FireEye, Inc.
|
|
Will
|
Green
|
FireEye, Inc.
|
|
Rajeev
|
Jha
|
FireEye, Inc.
|
|
Anuj
|
Kumar
|
FireEye, Inc.
|
|
James
|
Meck
|
FireEye, Inc.
|
|
Scott
|
Shreve
|
FireEye, Inc.
|
|
Jon
|
Warren
|
FireEye, Inc.
|
|
Remko
|
Weterings
|
FireEye, Inc.
|
|
Sean
|
Barnum
|
FireEye, Inc.
|
|
Shyamal
|
Pandya
|
FireEye, Inc.
|
|
Paul
|
Patrick
|
FireEye, Inc.
|
|
Tim
|
Jones
|
ForeScout
|
|
Gavin
|
Chow
|
Fortinet Inc.
|
|
Steve
|
Fossen
|
Fortinet Inc.
|
|
Kenichi
|
Terashita
|
Fortinet Inc.
|
|
Daisuke
|
Murabayashi
|
Fujitsu Limited
|
|
Derek
|
Northrope
|
Fujitsu Limited
|
|
Ryusuke
|
Masuoka
|
Fujitsu Limited
|
|
Toshitaka
|
Satomi
|
Fujitsu Limited
|
|
Koji
|
Yamada
|
Fujitsu Limited
|
|
Kunihiko
|
Yoshimura
|
Fujitsu Limited
|
|
David
|
Lemire
|
G2
|
|
Jonathan
|
Algar
|
GDS
|
|
Adam
|
Cooper
|
GDS
|
|
Mike
|
McLellan
|
GDS
|
|
Tyrone
|
Nembhard
|
GDS
|
|
Chris
|
O'Brien
|
GDS
|
|
James
|
Penman
|
GDS
|
|
Howard
|
Staple
|
GDS
|
|
Chris
|
Taylor
|
GDS
|
|
Laurie
|
Thomson
|
GDS
|
|
Alastair
|
Treharne
|
GDS
|
|
Julian
|
White
|
GDS
|
|
Bethany
|
Yates
|
GDS
|
|
Iain
|
Brown
|
GDS
|
|
Robert
|
van Engelen
|
Genivia
|
|
Eric
|
Burger
|
Georgetown University
|
|
Allison
|
Miller
|
Google Inc.
|
|
Mark
|
Risher
|
Google Inc.
|
|
Yoshihide
|
Kawada
|
Hitachi, Ltd.
|
|
Jun
|
Nakanishi
|
Hitachi, Ltd.
|
|
Akihito
|
Sawada
|
Hitachi, Ltd.
|
|
Yutaka
|
Takami
|
Hitachi, Ltd.
|
|
Kazuo
|
Noguchi
|
Hitachi, Ltd.
|
|
Masato
|
Terada
|
Hitachi, Ltd.
|
|
Adrian
|
Bishop
|
Huntsman Security
|
|
Eldan
|
Ben-Haim
|
IBM
|
|
Allen
|
Hadden
|
IBM
|
|
Sandra
|
Hernandez
|
IBM
|
|
Chenta
|
Lee
|
IBM
|
|
Devesh
|
Parekh
|
IBM
|
|
Laura
|
Rusu
|
IBM
|
|
Jason
|
Keirstead
|
IBM
|
|
John
|
Morris
|
IBM
|
|
Ron
|
Williams
|
IBM
|
|
Paul
|
Martini
|
iboss, Inc.
|
|
Vasileios
|
Mavroeidis
|
IFI
|
|
Jerome
|
Athias
|
Individual
|
|
Joerg
|
Eschweiler
|
Individual
|
|
Alex
|
Pinto
|
Individual
|
|
Stefan
|
Hagen
|
Individual
|
|
Elysa
|
Jones
|
Individual
|
|
Terry
|
MacDonald
|
Individual
|
|
Tim
|
Casey
|
Intel Corporation
|
|
Julie
|
Modlin
|
Johns Hopkins University Applied Physics Laboratory
|
|
Mark
|
Moss
|
Johns Hopkins University Applied Physics Laboratory
|
|
Mark
|
Munoz
|
Johns Hopkins University Applied Physics Laboratory
|
|
Nathan
|
Reller
|
Johns Hopkins University Applied Physics Laboratory
|
|
Pamela
|
Smith
|
Johns Hopkins University Applied Physics Laboratory
|
|
Subodh
|
Kumar
|
JPMorgan Chase Bank, N.A.
|
|
David
|
Laurance
|
JPMorgan Chase Bank, N.A.
|
|
Russell
|
Culpepper
|
Kaiser Permanente
|
|
Michael
|
Slavick
|
Kaiser Permanente
|
|
Beth
|
Pumo
|
Kaiser Permanente
|
|
Gus
|
Creedon
|
Logistics Management Institute
|
|
Wesley
|
Brown
|
LookingGlass
|
|
Himanshu
|
Kesar
|
LookingGlass
|
|
Ian
|
Truslove
|
LookingGlass
|
|
Chris
|
Wood
|
LookingGlass
|
|
Jamison
|
Day
|
LookingGlass
|
|
Dennis
|
Hostetler
|
LookingGlass
|
|
Allan
|
Thomson
|
LookingGlass
|
|
Kent
|
Landfield
|
McAfee
|
|
Richard
|
Struse
|
Mitre Corporation
|
|
Desiree
|
Beck
|
Mitre Corporation
|
|
Michael
|
Chisholm
|
Mitre Corporation
|
|
Sam
|
Cornwell
|
Mitre Corporation
|
|
Michael
|
Kouremetis
|
Mitre Corporation
|
|
Nicole
|
Parrish
|
Mitre Corporation
|
|
Larry
|
Rodrigues
|
Mitre Corporation
|
|
Jon
|
Salwen
|
Mitre Corporation
|
|
Charles
|
Schmidt
|
Mitre Corporation
|
|
Alex
|
Tweed
|
Mitre Corporation
|
|
Emmanuelle
|
Vargas-Gonzalez
|
Mitre Corporation
|
|
Greg
|
Back
|
Mitre Corporation
|
|
Jonathan
|
Baker
|
Mitre Corporation
|
|
Ivan
|
Kirillov
|
Mitre Corporation
|
|
Chris
|
Lenk
|
Mitre Corporation
|
|
Richard
|
Piazza
|
Mitre Corporation
|
|
John
|
Wunder
|
Mitre Corporation
|
|
James
|
Cabral
|
MTG Management Consultants, LLC.
|
|
Scott
|
Algeier
|
National Council of ISACs (NCI)
|
|
Denise
|
Anderson
|
National Council of ISACs (NCI)
|
|
Josh
|
Poster
|
National Council of ISACs (NCI)
|
|
Mike
|
Boyle
|
National Security Agency
|
|
Joe
|
Brule
|
National Security Agency
|
|
Jessica
|
Fitzgerald-McKay
|
National Security Agency
|
|
David
|
Kemp
|
National Security Agency
|
|
Shaun
|
McCullough
|
National Security Agency
|
|
Jason
|
Romano
|
National Security Agency
|
|
Michael
|
Pepin
|
NC4
|
|
Benjamin
|
Yates
|
NC4
|
|
John
|
Anderson
|
NC4
|
|
Michael
|
Butt
|
NC4
|
|
Mark
|
Davidson
|
NC4
|
|
Daniel
|
Dye
|
NC4
|
|
Natalie
|
Suarez
|
NC4
|
|
Sarah
|
Brown
|
NCI Agency
|
|
Oscar
|
Serrano
|
NCI Agency
|
|
Daichi
|
Hasumi
|
NEC Corporation
|
|
Lauri
|
Korts-P‰rn
|
NEC Corporation
|
|
Takahiro
|
Kakumaru
|
NEC Corporation
|
|
Danny
|
Purcell
|
New Context Services, Inc.
|
|
Trey
|
Darley
|
New Context Services, Inc.
|
|
John-Mark
|
Gurney
|
New Context Services, Inc.
|
|
Christian
|
Hunt
|
New Context Services, Inc.
|
|
Daniel
|
Riedel
|
New Context Services, Inc.
|
|
Andrew
|
Storms
|
New Context Services, Inc.
|
|
Drew
|
Varner
|
NineFX, Inc.
|
|
Stephen
|
Banghart
|
NIST
|
|
David
|
Darnell
|
North American Energy Standards Board
|
|
James
|
Crossland
|
Northrop Grumman
|
|
Robert
|
Van Dyk
|
Northrop Grumman
|
|
Cheolho
|
Lee
|
NSRI
|
|
Cory
|
Casanave
|
Object Management Group
|
|
Vishaal
|
Hariprasad
|
Palo Alto Networks
|
|
Aharon
|
Chernin
|
Perch
|
|
Dave
|
Eilken
|
Perch
|
|
Sourabh
|
Satish
|
Phantom
|
|
Philip
|
Royer
|
Phantom
|
|
John
|
Tolbert
|
Queralt Inc.
|
|
Jay
|
Heidecker
|
Seekintoo
|
|
Joseph
|
Brand
|
Semper Fortis Solutions
|
|
Duncan
|
Sparrell
|
sFractal Consulting LLC
|
|
Thomas
|
Schreck
|
Siemens AG
|
|
Rob
|
Roel
|
Southern California Edison
|
|
Armen
|
Tashjian
|
Southern California Edison
|
|
Dave
|
Cridland
|
Surevine Ltd.
|
|
Chris
|
Larsen
|
Symantec Corp.
|
|
Efrain
|
Ortiz
|
Symantec Corp.
|
|
Mingliang
|
Pei
|
Symantec Corp.
|
|
Kenneth
|
Schneider
|
Symantec Corp.
|
|
Arnaud
|
Taddei
|
Symantec Corp.
|
|
Brian
|
Witten
|
Symantec Corp.
|
|
Bret
|
Jordan
|
Symantec Corp.
|
|
Robert
|
Keith
|
Symantec Corp.
|
|
Curtis
|
Kostrosky
|
Symantec Corp.
|
|
Michael
|
Mauch
|
Symantec Corp.
|
|
Aubrey
|
Merchant
|
Symantec Corp.
|
|
Juha
|
Haaga
|
Synopsys
|
|
Greg
|
Reaume
|
TELUS
|
|
Alan
|
Steer
|
TELUS
|
|
Crystal
|
Hayes
|
The Boeing Company
|
|
Andrew
|
Gidwani
|
ThreatConnect, Inc.
|
|
Cole
|
Iliff
|
ThreatConnect, Inc.
|
|
Andrew
|
Pendergast
|
ThreatConnect, Inc.
|
|
Jason
|
Spies
|
ThreatConnect, Inc.
|
|
Ryan
|
Trost
|
ThreatQuotient, Inc.
|
|
Nir
|
Yosha
|
ThreatQuotient, Inc.
|
|
Patrick
|
Coughlin
|
TruSTAR Technology
|
|
Chris
|
Roblee
|
TruSTAR Technology
|
|
Mark
|
Angel
|
U.S. Bank
|
|
Brian
|
Fay
|
U.S. Bank
|
|
Joseph
|
Frazier
|
U.S. Bank
|
|
Mark
|
Heidrick
|
U.S. Bank
|
|
Richard
|
Shok
|
U.S. Bank
|
|
Ehab
|
Al-Shaer
|
UNCC
|
|
Bill
|
Chu
|
UNCC
|
|
Eoghan
|
Casey
|
US Department of Defense (DoD)
|
|
James
|
Bohling
|
US Department of Defense (DoD)
|
|
Gary
|
Katz
|
US Department of Defense (DoD)
|
|
Jeffrey
|
Mates
|
US Department of Defense (DoD)
|
|
Evette
|
Maynard-Noel
|
US Department of Homeland Security
|
|
Eric
|
Osterweil
|
VeriSign
|
|
Lee
|
Chieffalo
|
Viasat
|
|
Wilson
|
Figueroa
|
Viasat
|
|
Andrew
|
May
|
Viasat
|
|
Ales
|
Cernivec
|
XLAB
|
|
Anthony
|
Rutkowski
|
Yanna Technologies LLC
|
Appendix
B. Revision History
|
Revision
|
Date
|
Editor
|
Changes Made
|
|
01
|
2018-04-13
|
Allan Thomson
|
Fixed
-
Missed created/modified dates from identity object examples
-
Hyperlinks broken in doc
-
Fixed all test data samples using Trey’s test validated content
-
Added TIS persona to test list
|
|
Final Draft (Rejected at Ballot)
|
2018-05-04
|
Allan Thomson
|
Fixed
-
Date/Title for ballot
|
|
02
|
2018-06-20
|
Allan Thomson
|
Fixed
-
Added IPR Policy Section
-
Removed modified timestamps from marking definitions; fixed TLP
references to resolve Issue https://github.com/oasis-open/cti-interop/issues/4
-
Fixed text description for marking definition tests using TLP to
resolve issue https://github.com/oasis-open/cti-interop/issues/3
-
Added recommendation to Section 2.1 for x_interop_description use to
resolve issue https://github.com/oasis-open/cti-interop/issues/2
-
Made testing of Sighting producer for DFP optional to
resolve issue https://github.com/oasis-open/cti-interop/issues/1
-
Changed Use Case to Test Case in Section 2 title
|
|
03
|
07/31/18
|
Allan Thomson
|
Fixed
-
Added proposed introduction of a ‘persona’ text
-
Editorial comments addressed
-
Changed x_interop_description to x_interop_test
-
Changed revocation figure to correctly reference property and logic
-
Removed marking definitions being transmitted
-
Changed marking tests to optioanl for DFP
|
|
FD-01
|
08/01/18
|
Allan Thomson
|
Publication for ballot.
|








