Exchange Header Envelope (XHE) Version 1.0
Committee Specification 03
13 December 2020
- This stage:
- https://docs.oasis-open.org/bdxr/xhe/v1.0/cs03/xhe-v1.0-cs03.xml
(Authoritative)
https://docs.oasis-open.org/bdxr/xhe/v1.0/cs03/xhe-v1.0-cs03-oasis.html
https://docs.oasis-open.org/bdxr/xhe/v1.0/cs03/xhe-v1.0-cs03-oasis.pdf
- Technical Committee:
- OASIS Business Document Exchange (BDXR) TC
- Chairs:
- (OASIS TC Chair) Kenneth Bengtsson (kbengtsson@efact.pe), Individual
(UN/CEFACT Project Chair) Anders Grangard (anders.grangard@GS1.ORG), GS1
- Editor:
- G. Ken Holman (gkholman@CraneSoftwrights.com), Crane Softwrights Ltd.
- Related work:
This specification supersedes:
[BDE 1.1] Business Document Envelope Version 1.1 Edited by G. Ken Holman and Kenneth Bengtsson. 05 December 2016. OASIS Committee Specification 01. Latest version: https://docs.oasis-open.org/bdxr/bdx-bde/v1.1/bdx-bde-v1.1.html.
- Declared XML Namespaces:
- Abstract:
This specification defines a business-oriented artefact either referencing (as a header) or containing (as an envelope) a payload of one or more business documents or other artefacts with supplemental semantic information about the collection of payloads as a whole. This is distinct from any transport-layer infrastructure header or envelope that may be required to propagate documents from one system to another. An exchange header envelope describes contextual information important to the sender and receiver about the payloads, without having to modify the payloads in any fashion.
- Status:
This document has been prepared and submitted both to the OASIS Business Document Exchange (BDXR) TC and to the UN/CEFACT Methodology and Technology PDA. It is the intent of both groups to share any further proposed changes to both panels and to approve identical final versions. Final approval by one or both organizations may also require their mutual commitment to approve and maintain one and the same final specification.
This document was last approved by the OASIS Business Document Exchange (BDXR) TC on the above date. The level of approval is also listed above. Check the “Latest version” location noted above for possible later revisions of this document. Any other numbered Versions and other technical work produced by the Technical Committee (TC) are listed at https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=bdxr#technical.
TC members should send comments on this specification to the TC’s email list. Others should send comments to the TC’s public comment list, after subscribing to it by following the instructions at the “Send A Comment” button on the TC’s web page at https://www.oasis-open.org/committees/bdxr/.
This specification is being developed under the Non-Assertion Mode of the OASIS IPR Policy, the mode chosen when the Technical Committee was established. All members of the TC should be familiar with this document, which may create obligations regarding the disclosure and availability of a member’s patent, copyright, trademark and license rights that read on an approved OASIS specification. For information on whether any patents have been disclosed that may be essential to implementing this specification, and any offers of patent licensing terms, please refer to the Intellectual Property Rights section of the TC’s web page (https://www.oasis-open.org/committees/bdxr/ipr.php).
Note that any machine-readable content (Computer Language Definitions) declared Normative for this Work Product is provided in separate plain text files. In the event of a discrepancy between any such plain text file and display content in the Work Product’s prose narrative document(s), the content in the separate plain text file prevails.
- Citation format:
When referencing this specification the following citation format should be used:
[XHE-V1.0] Exchange Header Envelope (XHE) Version 1.0. Edited by G. Ken Holman. 13 December 2020. OASIS Committee Specification 03. https://docs.oasis-open.org/bdxr/xhe/v1.0/cs03/xhe-v1.0-cs03-oasis.html. Latest version: https://docs.oasis-open.org/bdxr/xhe/v1.0/xhe-v1.0-oasis.html.
Notices
Copyright © OASIS Open 2020. All Rights Reserved.
All capitalized terms in the following text have the meanings assigned to them in the OASIS Intellectual Property Rights Policy (the “OASIS IPR Policy”). The full Policy may be found at the OASIS website.
This document and translations of it may be copied and furnished to others, and derivative works that comment on or otherwise explain it or assist in its implementation may be prepared, copied, published, and distributed, in whole or in part, without restriction of any kind, provided that the above copyright notice and this section are included on all such copies and derivative works. However, this document itself may not be modified in any way, including by removing the copyright notice or references to OASIS, except as needed for the purpose of developing any document or deliverable produced by an OASIS Technical Committee (in which case the rules applicable to copyrights, as set forth in the OASIS IPR Policy, must be followed) or as required to translate it into languages other than English.
The limited permissions granted above are perpetual and will not be revoked by OASIS or its successors or assigns.
This document and the information contained herein is provided on an “AS IS” basis and OASIS DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT INFRINGE ANY OWNERSHIP RIGHTS AND ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
OASIS requests that any OASIS Party or any other party that believes it has patent claims that would necessarily be infringed by implementations of this OASIS Committee Specification or OASIS Standard notify OASIS TC Administrator and provide an indication of its willingness to grant patent licenses to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification.
OASIS invites any party to contact the OASIS TC Administrator if it is aware of a claim of ownership of any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may include such claims on its website, but disclaims any obligation to do so.
OASIS takes no position regarding the validity or scope of any intellectual property or other rights that might be claimed to pertain to the implementation or use of the technology described in this document or the extent to which any license under such rights might or might not be available; neither does it represent that it has made any effort to identify any such rights. Information on OASIS’ procedures with respect to rights in any document or deliverable produced by an OASIS Technical Committee can be found on the OASIS website. Copies of claims of rights made available for publication and any assurances of licenses to be made available, or the result of an attempt made to obtain a general license or permission for the use of such proprietary rights by implementers or users of this OASIS Committee Specification or OASIS Standard, can be obtained from the OASIS TC Administrator. OASIS makes no representation that any information or list of intellectual property rights will at any time be complete, or that any claims in such list are, in fact, Essential Claims.
The name “OASIS” is a trademark of OASIS, the owner and developer of this specification, and should be used only to refer to the organization and its official outputs. OASIS welcomes reference to, and implementation and use of, specifications, while reserving the right to enforce its marks against misleading uses. Please see https://www.oasis-open.org/policies-guidelines/trademark/ for guidance.
Table of Contents
- 1 Introduction
- 2 Header and envelope information
- 3 XHE digital signatures
- 4 Conformance
- 5 XML syntax expression
Appendixes
File or document headers have long been used to describe the information about a set of payloads in an entity that is kept separate and arm’s-length from the payloads themselves.
The metaphor of a paper envelope in which one places business documents for transport or management is apt to describe the role of an exchange header envelope in a container relationship to its payloads. Concepts of routing, authentication, non-repudiation and concealment all apply in both the metaphor and the electronic equivalent.
The Exchange Header Envelope (XHE) specifies an XML vocabulary [XML] expressing in machine-processable syntax the semantics of describing either a header to or an envelope of a set of payloads of content with information about that content. This vocabulary is modeled using the UN/CEFACT Core Component Technical Specification Version 2.01 [CCTS 2.01].
XHE, a specification developed jointly by UN/CEFACT and OASIS, is the successor to the UN/CEFACT Standard Business Document Header (SBDH) version 1.3 [SBDH] and the OASIS Business Document Envelope (BDE) version 1.1 [BDE].
Note regarding publications
The UN/CEFACT Exchange Header Envelope and the OASIS Exchange Header Envelope are the same specification developed in collaboration and published as standards by the two organizations following the practices of each.
This specification enumerates the information components of a payload header envelope and formally describes the semantics of each component.
Normative markings
All clauses not marked as “informative” and also not a subclause of a clause marked as “informative” are to be considered normative. All notes and examples are informative.
The XHE is designed to be either a header as an integral part of a business document (e.g. either XML instance document or EDI interchange), an object associated with the business document itself, or as an envelope functioning as wrapper that contains one or more business documents.
This specification mandates a suite of XML schemas [XMLSCHEMA-1][XMLSCHEMA-2] and additional limitations describing the document constraints against which a conforming instance SHALL validate without error.
There exist several business document exchange architectures and approaches, some using EDI formats and approaches, some using XML document types, and yet others use different document formats or non-standardized approaches. The XHE is designed to work with any document format and business process, whether standardized or not, and as such supports both the EDI, the XML and any other e-business community. Including a XHE in each instance of the business document reduces the effort needed to route and process documents and permits trading partner organizations to use different implementation approaches.
When implementing EDI, the provision of an additional business document header may not always be necessary, since EDI interchanges already contain functionality for some of the information in the XHE. An example is the EDIFACT UNB interchange header, the UNH message header, and the ‘function’ part of the BGM. The XHE specification allows for this existing approach and provides an option to express additional functionality, such as service and correlation information.
Many users, implementers and supporting industry standard bodies are in agreement on the need for an Exchange Header Envelope. In their business-to-business activities, the XHE facilitates several different business needs:
The routing of business documents from one point to another. This refers not only to the transfer of information from an external originator to receiver, but also from one intermediate application to another. Information in the XHE can help ensure that a document gets to the correct recipient.
Ensuring integrity and confidentiality of business documents when routed over multiple hops, intermediaries, routers or access points, such as in 4-corner networks and architectures.
Simplifying the bundling of several business documents or support documents into one package for simplified exchange.
Facilitating the exchange of location pointers and access credentials to externally located business documents, not suitable for sending through an e-business network. This is necessary when the sending party needs to keep the business document confidential until a specified date (such as in tendering processes), and when sending very large files.
The simplified processing of documents. Processing refers to taking action on data, for example transforming it from one format into another. Information in the XHE can reduce the effort required to determine the correct processing actions.
Associating a data message with its originator is important from a business and legal perspective. It is especially important when using intermediaries for data transfer, as information from the transport protocol, may be lost after the initial transmission. Because information in the XHE is retained, it can help ensure that a document’s originator is correctly identified.
In addition to header functions provided by the XHE for routing and/or processing of business documents, there is the need for a completely separate technical communications transport layer. This deals with communications protocols and physical addresses which are outside the scope of this technical specification. Transport specifications including EDIINT-AS2 and ebXML Message Service (ebMS) are among a number of possible transport options that address technical communications needs by defining a separate technical header. The transport layer is completely outside the scope as it is a different layer of the stack.
This specification accommodates both CEFACT and OASIS naming conventions of all semantic identifiers by documenting the two values for every business information entity. In each table row in Section 2, “Header and envelope information” the semantic identifiers are provided in two sub-rows, the upper one carrying the CEFACT semantic identifier and the lower one carrying the OASIS semantic identifier.
All organizations that manage infrastructure operations and business processes for various functional areas (e.g. ordering, invoicing, planning, or financial), all service provider organizations and associations, as well as e-business networks and infrastructures, which create, route and process business documents can benefit from the use of the Exchange Header Envelope.
The entities defined by this specification are realized as schema validation artefacts using the conventions specified by the OASIS Business Document Naming and Design Rules [BD-NDR] and the OASIS semantic identifiers.
The key words MUST, MUST NOT, REQUIRED, SHALL, SHALL NOT, OPTIONAL and SHOULD in this document are to be interpreted as described in [RFC2119].
- schema, noun
An expression of constraints placed on XML content.
- value constraints, noun
An expression of constraints placed on the values of attributes and textual content.
[CCTS 2.01] UN/CEFACT Core Components Technical Specification, Version 2.0115 November 2003 http://www.unece.org/fileadmin/DAM/cefact/codesfortrade/CCTS/CCTS_V2-01_Final.pdf
[RFC2119] , Key words for use in RFCs to Indicate Requirement Levels, BCP 14, RFC 2119, DOI 10.17487/RFC2119, March 1997, <http://www.rfc-editor.org/info/rfc2119>.
[XML] Extensible Markup Language (XML) 1.0 (Fifth Edition), , , , , , Editors, W3C Recommendation, November 26, 2008, http://www.w3.org/TR/2008/REC-xml-20081126/. Latest version available at http://www.w3.org/TR/xml/.
[XMLDSIG-CORE1] XML-Signature Syntax and Processing Version 1.1, , , , , , , , Editors, W3C Recommendation, April 11, 2013, http://www.w3.org/TR/2013/REC-xmldsig-core1-20130411/. Latest version available at http://www.w3.org/TR/xmldsig-core1/.
[XMLSCHEMA-1] XML Schema Part 1: Structures Second Edition, , , , , Editors, W3C Recommendation, October 28, 2004, http://www.w3.org/TR/2004/REC-xmlschema-1-20041028/. Latest version available at http://www.w3.org/TR/xmlschema-1/.
[XMLSCHEMA-2] XML Schema Part 2: Datatypes Second Edition, , , Editors, W3C Recommendation, October 28, 2004, http://www.w3.org/TR/2004/REC-xmlschema-2-20041028/. Latest version available at http://www.w3.org/TR/xmlschema-2/.
[BDE] Business Document Envelope Version 1.1 Edited by G. Ken Holman and Kenneth Bengtsson. 05 December 2016. OASIS Committee Specification 01. Latest version: http://docs.oasis-open.org/bdxr/bdx-bde/v1.1/bdx-bde-v1.1.html.
[BD-NDR] Business Document Naming and Design Rules Version 1.0. Edited by Tim McGrath, Andy Schoka and G. Ken Holman. 14 July 2016. OASIS Committee Specification 01. http://docs.oasis-open.org/ubl/Business-Document-NDR/v1.0/cs01/Business-Document-NDR-v1.0-cs01.html. Latest version: http://docs.oasis-open.org/ubl/Business-Document-NDR/v1.0/Business-Document-NDR-v1.0.html.
[RFC5652] , Cryptographic Message Syntax (CMS), STD 70, RFC 5652, DOI 10.17487/RFC5652,September 2009, https://tools.ietf.org/html/rfc5652.
[genericode] Code List Representation (Genericode) Version 1.0. Edited by Anthony B. Coates. 28 December 2007. Committee Specification 01. http://docs.oasis-open.org/codelist/genericode/. Latest version: http://docs.oasis-open.org/codelist/genericode/doc/oasis-code-list-representation-genericode.html.
[RFC4880] , , , , and , OpenPGP Message Format, RFC4880, DOI 10.17487/RFC4880, November 2007, https://tools.ietf.org/html/rfc4880.
[SBDH] CEFACT Standard Business Document Header https://www.gs1.org/sites/default/files/docs/gs1_un-cefact_%20xml_%20profiles/CEFACT_SBDH_TS_version1.3.pdf
[XAdES] XML Advanced Electronic Signatures. ETSI TS 101 903 V1.4.1, June 2009 http://uri.etsi.org/01903/v1.4.1/ts_101903v010401p.pdf
[XMLENC-CORE1] XML Encryption Syntax and Processing Version 1.1, , , , , W3C Recommendation April 22, 2013, http://www.w3.org/TR/2013/REC-xmlenc-core1-20130411/. Latest version available at http://www.w3.org/TR/xmlenc-core1/.
This specification is being developed under the Non-Assertion Mode of the OASIS IPR Policy, the mode chosen when the Technical Committee was established. All members of the TC should be familiar with this document, which may create obligations regarding the disclosure and availability of a member’s patent, copyright, trademark and license rights that read on an approved OASIS specification. For information on whether any patents have been disclosed that may be essential to implementing this specification, and any offers of patent licensing terms, please refer to the Intellectual Property Rights section of the TC’s web page (https://www.oasis-open.org/committees/bdxr/ipr.php).
The information derived for XHE has been distilled into a suite of CCTS Aggregate Business Information Entities (ABIEs), each comprised of a set of Basic Business Information Entities (BBIEs) and/or Association Business Information Entities (ASBIEs).
Each entity is listed with its two semantic identifiers, one specified by CEFACT members of the development team, and one specified by OASIS members of the development team. See Section 1.1.5, “Dual Semantic Identifiers” for more information.
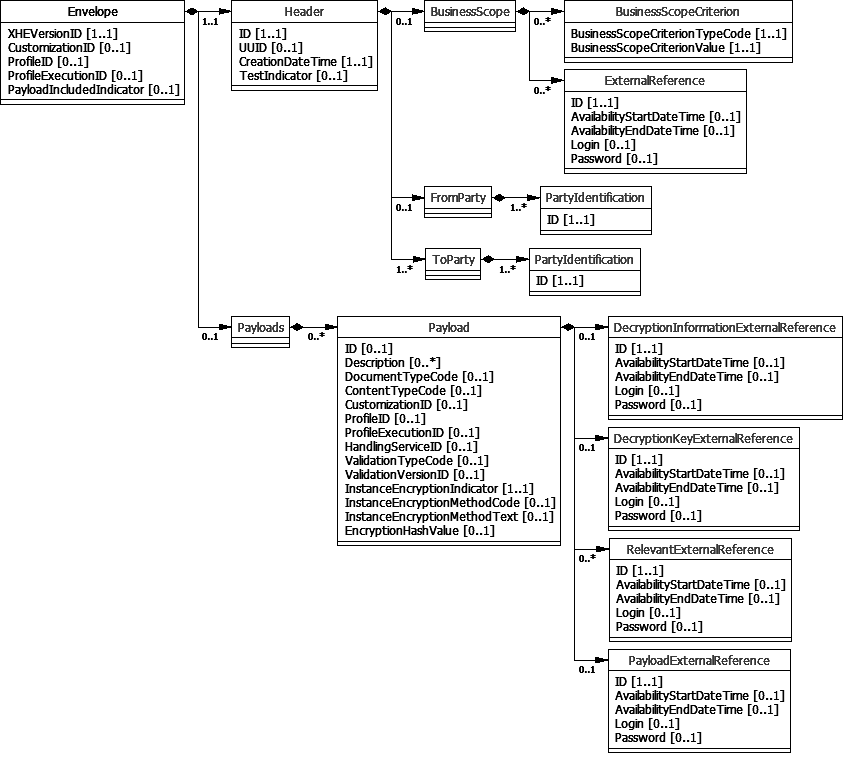
The relationships between these business information entities are depicted in this class diagram using the CEFACT names:
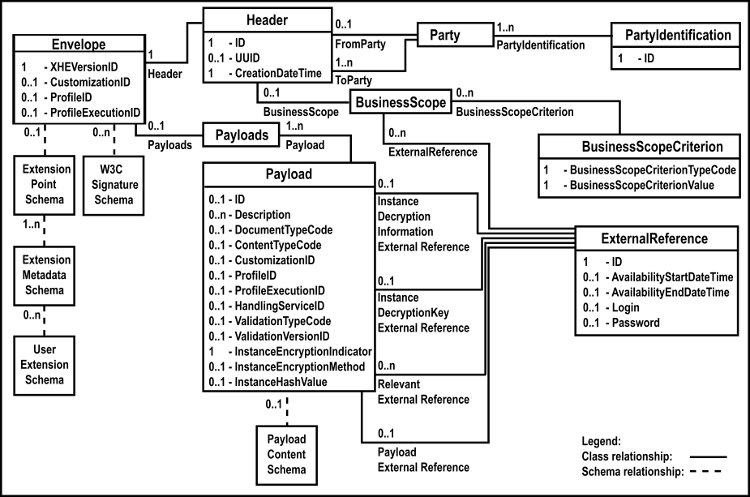
The relationships between these business information entities are depicted in this class diagram using the OASIS names:
Metadata information about the header envelope itself, independent of the information it contains, includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Envelope. Details | N/A | The Exchange Header Envelope |
| XHE. Details | ||
| XHE_ Envelope. Version. Identifier | 1 | The version of the specific envelope model in use. |
| XHE. XHE Version Identifier. Identifier | ||
| XHE_ Envelope. Customization. Identifier | 0..1 | The identification of a customization or use of the envelope model. |
| XHE. Customization Identifier. Identifier | ||
| XHE_ Envelope. Profile. Identifier | 0..1 | The identification of a specific profile found within the customization. |
| XHE. Profile Identifier. Identifier | ||
| XHE_ Envelope. Profile Execution. Identifier | 0..1 | The identification of a particular instance of using the given profile. |
| XHE. Profile Execution Identifier. Identifier | ||
| XHE_ Envelope. Metadata. XHE_ Document | 1 | Information relevant to the handling of the envelope. |
| XHE. Header | ||
| XHE_ Envelope. Included. XHE_ Payload | 0..1 | The set of payloads |
| XHE. Payloads |
The information for a header envelope begins with an additional optional extensions item that is neither a BBIE nor an ASBIE and so is not modeled using CCTS. Rather, this extensions item is a schema artefact. This extensions item has the cardinality 0..1. See Section 5.6.2, “Extension content” for more information.
The information for a header envelope ends with an additional optional and repeatable number of digital signatures that are neither a BBIE nor an ASBIE and so are not modeled using CCTS. Rather, these signatures are a schema artefact published by the W3C. See Section 3.1, “Signing the exchange header envelope” for more information.
Metadata information about the header envelope itself, independent of the information it contains or references, includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Document. Identification. Identifier | 1 | Unique ID of the envelope for tracking purposes. |
| Header. Identifier | ||
| XHE_ Document. UUID. Identifier | 0..1 | An additional identifier of the envelope. |
| Header. UUID | ||
| XHE_ Document. Creation. Date Time | 1 | Date and time when the envelope was created. |
| Header. Creation Date Time. Date Time | ||
| XHE_ Document. Scope. XHE_ Context | 0..1 | Documentation of the scope of business or other contextual details useful to understand the purpose of the envelope and its contents. For examples: Europe vs Asia, Direct-to-Consumer vs Replenishment, or Prepaid vs Credit. |
| Header. Business Scope | ||
| XHE_ Document. Sender. XHE_ Party | 0..1 | Information about the party that originated the envelope. |
| Header. From_ Party. Party | ||
| XHE_ Document. Recipient. XHE_ Party | 1..n | Information about the parties to receive the envelope. |
| Header. To_ Party. Party |
The information about a party includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Party. Specified. XHE_ Identity | 1..n | Unambiguous identifications of a party. |
| Party. Party Identification |
The information about a party’s identification includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Party. Specified. XHE_ Identity | 1 | An unambiguous identification of a party. |
| Party Identification. Identifier |
Documentation of the scope of business or other contextual details useful to understand the purpose of the envelope and its contents includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Context. Specified. XHE_ Parameter | 0..n | Internal specification of the scope and/or context of business. |
| Business Scope. Business Scope Criterion | ||
| XHE_ Context. Scope. XHE_ Reference | 0..n | External documentation of the scope and/or context of business. |
| Business Scope. External Reference |
Documentation of one criterion of the scope of business or other contextual detail useful to understand the purpose of the envelope and its contents includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Parameter. Type. Code | 1 | Identifies the property of the scope by a code. |
| Business Scope Criterion. Business Scope Criterion Type. Code | ||
| XHE_ Parameter. Value. Text | 1 | Specifies the value of the given property. |
| Business Scope Criterion. Business Scope Criterion Value. Text |
A reference to a business case, document or other issues which are relevant to the handling of the envelope includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Reference. Identification. Identifier | 1 | Identifies the referenced object by some identifier or URI. |
| External Reference. Identifier | ||
| XHE_ Reference. Start_ Availability. Date Time | 0..1 | The start date and time when the information is available |
| External Reference. Availability Start Date Time. Date Time | ||
| XHE_ Reference. End_ Availability. Date Time | 0..1 | The end date and time when the information is available |
| External Reference. Availability End Date Time. Date Time | ||
| XHE_ Reference. Login. Text | 0..1 | Text describing any login details to access the information. |
| External Reference. Login. Text | ||
| XHE_ Reference. Password. Text | 0..1 | A password needed to access the information. |
| External Reference. Password. Text |
Information about the complete set of payloads includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Payload. Included. XHE_ Payload Instance | 1..n | The actual payload instance, such as a single invoice, conveyed within the envelope. |
| Payloads. Payload |
Information about an individual payload within the set of payloads includes the following:
| Semantic identifier | Card. | Definition |
|---|---|---|
| XHE_ Payload Instance. Identification. Identifier | 0..1 | A unique identification of this payload instance contained within the envelope. |
| Payload. Identifier | ||
| XHE_ Payload Instance. Description. Text | 0..n | Text description of the payload instance. |
| Payload. Description. Text | ||
| XHE_ Payload Instance. Document_ Type. Code | 0..1 | Identifies the abstract archetype of the payload instance. |
| Payload. Document Type Code. Code | ||
| XHE_ Payload Instance. Content_ Type. Code | 0..1 | Identifies the file format or octet representation of the payload instance. |
| Payload. Content Type Code. Code | ||
| XHE_ Payload Instance. Customization. Identifier | 0..1 | Identifies the customization that applies to the payload instance. |
| Payload. Customization Identifier. Identifier | ||
| XHE_ Payload Instance. Profile. Identifier | 0..1 | Identifies the profile that the payload instance is part of. |
| Payload. Profile Identifier. Identifier | ||
| XHE_ Payload Instance. Profile Execution. Identifier | 0..1 | Identifies the particular instance of an executing profile that the payload instance is part of. |
| Payload. Profile Execution Identifier. Identifier | ||
| XHE_ Payload Instance. Handling Service. Identifier | 0..1 | Identifies the service that should process the payload instance. |
| Payload. Handling Service Identifier. Identifier | ||
| XHE_ Payload Instance. Validation_ Type. Code | 0..1 | The validation type of the payload, used for the task of verifying that the grammar of a payload is valid. |
| Payload. Validation Type. Code | ||
| XHE_ Payload Instance. Validation Version. Identifier | 0..1 | Descriptor containing version information of the validation type. |
| Payload. Validation Version Identifier. Identifier | ||
| XHE_ Payload Instance. Encrypted. Indicator | 1 | Indicator to state whether the payload instance is encrypted or not. |
| Payload. Instance Encryption Indicator. Indicator | ||
| XHE_ Payload Instance. Encryption Method. Text | 0..1 | Method used to encrypt the payload instance. |
| Payload. Instance Encryption Method. Text | ||
| XHE_ Payload Instance. Encryption Hash Value. Text | 0..1 | SHA-256 hash total of the unencrypted payload instance. |
| Payload. Instance Hash Value. Text | ||
| XHE_ Payload Instance. Decryption. XHE_ Reference | 0..1 | Decryption information that is available external to the envelope. |
| Payload. Instance Decryption Information_ External Reference. External Reference | ||
| XHE_ Payload Instance. Decryption Key. XHE_ Reference | 0..1 | Decryption key data that is available external to the envelope. |
| Payload. Instance Decryption Key_ External Reference. External Reference | ||
| XHE_ Payload Instance. Relevant. XHE_ Reference | 0..n | A reference to a business case, document or other issues which are relevant to the handling of the payload. |
| Payload. Relevant_ External Reference. External Reference | ||
| XHE_ Payload Instance. Payload. XHE_ Reference | 0..1 | The reference to the payload when it is not included within the envelope. |
| Payload. Payload_ External Reference. External Reference |
The information for an individual payload ends with an additional optional payload content item that is neither a BBIE nor an ASBIE and so is not modeled using CCTS. Rather, this content item is a schema artefact. This content item has the cardinality 0..1. This content item can have as its child either text only (no elements) or a single element, but not a combination of both nor more than one element. See Section 5.6.3, “Payload content” for more information.
Through the use of extension metadata and content, additional user-defined information that is not modelled by the CCTS classes can be added to the envelope instance.
The extension point is an optional construct as the initial child of the document element. The extension point, when it exists, SHALL contain one or more user-defined extensions,. Each extension contains optional extension metadata identifying properties of the extension as well as the extension content.
Name (Unqualified Data Type) |
Description |
Crd |
Rationale |
|
XHEExtensions | A container for all extensions present in the document. | 0..1 | This is the single point of access to all extensions as the first child of the main document. |
|
XHEExtension | A single extension for private use. | 1..n | There may be many extensions added to a single document. |
|
ExtensionID (Identifier) | An identifier for the Extension assigned by the creator of the extension. | 0..1 | This identifies the extension amongst other extensions within the document. |
|
ExtensionName (Name) | A name for the Extension assigned by the creator of the extension. | 0..1 | This identifies the extension in natural language within the document. |
|
ExtensionAgencyID (Identifier) | An agency that maintains one or more Extensions. | 0..1 | This identifies who created the extension. |
|
ExtensionAgencyName (Name) | The name of the agency that maintains the Extension. | 0..1 | This identifies who created the extension. |
|
ExtensionAgencyURI (Identifier) | A URI for the Agency that maintains the Extension. | 0..1 | This identifies who created the extension. |
ExtensionVersionID (Identifier) | The version of the Extension. | 0..1 | This distinguishes one version of the extension from another. |
|
ExtensionURI (Identifier) | A URI for the Extension. | 0..1 | This identifies the extension amongst other extensions outside of any document. |
ExtensionReasonCode (Code) | A code for the reason the Extension is being included. | 0..1 | This gives the author the opportunity to give rationale by way of a code. |
ExtensionReason (Text) | A description of the reason for the Extension. | 0..1 | This gives the author the opportunity to give rationale by way of a text description. |
|
ExtensionContent | The definition of the extension content. | 1 | This is the parent element of the extension content. |
There are no restrictions on the extension content. See Section 5.6.2, “Extension content” for more information.
Using the IETF/W3C XML Digital Signature specification [XMLDSIG-CORE1] one can add multiple “non-final” signatures or a single “final” signature to the exchange header envelope as the last children of the document element, that is, after the last BIE of the document element. A non-final signature digitally signs all content other than any of the other sibling signature elements that may exist in the document. A final signature digitally signs all content including the other sibling signature elements that may exist in the document.
The schema fragment for Section 5.6.2, “Extension content” included in this distribution provides for using digital signature extensions supporting XML Advanced Electronic Signatures [XAdES] (ETSI TS 101 903), when the electronic signing of an exchange header envelope is necessary to satisfy legal and technical requirements. The schema fragment can be modified to accommodate such future extension requirements without impacting on the conformance clauses of this specification.
In this conformance clause, the following abbreviated references to semantic identifiers are used for readability:
payload information item
(CEFACT) XHE_ Payload. Included. XHE_ Payload Instance
(OASIS) Payloads. Payload
payload external reference information item
(CEFACT) XHE_ Payload Instance. Payload. XHE_ Reference
(OASIS) Payload. Payload_ External Reference. External Reference
An Exchange Header Envelope instance exhibits conformance when complying with all of the following semantic criteria:
All semantic components defined by this specification, that is all information that is not found inside payload content or extension content, SHALL NOT have no value (that is, it SHALL NOT be empty).
When the XHE is embedded in a bounding document as a header, the properties of the first of all payload information items, if any are present, SHALL apply to the bounding document and SHALL NOT have either payload content nor the payload external reference information item child. Subsequent payload information items, if any are present, SHALL have one or the other of payload content or the payload external reference information item child (that is, it SHALL NOT have both and SHALL NOT have neither).
When the XHE is standalone in its own document as an envelope, all payload information items SHALL have one or the other of payload content or the payload external reference information item child (that is, it SHALL NOT have both and SHALL NOT have neither).
Each payload content SHALL NOT have a combination of text and an XML element (that is, it SHALL either be a non-empty string of text or be a single XML element).
The structural document constraints of the header envelope are expressed normatively as a set of W3C XSD XML Schemas [XMLSCHEMA-1][XMLSCHEMA-2].
The following XML namespace URI strings are specified in the XSD schemas to be used in the XML syntax expressions:
| http://docs.oasis-open.org/bdxr/ns/XHE/1/ExchangeHeaderEnvelope |
| http://docs.oasis-open.org/bdxr/ns/XHE/1/AggregateComponents |
| http://docs.oasis-open.org/bdxr/ns/XHE/1/BasicComponents |
| http://docs.oasis-open.org/bdxr/ns/XHE/1/ExtensionComponents |
| http://docs.oasis-open.org/bdxr/ns/XHE/1/QualifiedDataTypes |
| http://docs.oasis-open.org/bdxr/ns/XHE/1/UnqualifiedDataTypes |
The schemas are delivered in two subdirectories:
In both subdirectories there is a single subdirectory of imported and included schema fragments:
imported and included schema fragments by all other fragments
The following is the only Document ABIE schema:
the base header envelope schema fragment that incorporates other schema fragments
The following is the runtime version of the schema that has documentary annotations removed:
the base header envelope schema fragment that incorporates other schema fragments
The following are read-only schema fragments in the fragments/
subdirectory:
XHE-AggregateComponents-1.0.xsdthe Library ABIE element declarations
the Library BBIE element declarations
XHE-ExtensionComponents-1.0.xsdthe Document ABIE extension metadata declarations
XHE-QualifiedDataTypes-1.0.xsdthe qualified data types (empty; none are defined)
XHE-UnqualifiedDataTypes-1.0.xsdthe unqualified data types based on the core component types
see Section 5.7, “Unqualified data type attributes” for more details
the XML Digital Signature schema driver fragment copyrighted by W3C
the XML Digital Signature schema fragment copyrighted by W3C
XHE-xmldsig-core-schema-1.0.xsdthe XML Digital Signature Core schema fragment copyrighted by W3C
the Core Component Types schema fragment copyrighted by UN/CEFACT
There are two content data type schema fragments in the fragments/
subdirectory, one for each of the extension content and the payload content. These are the
only schemas intended to be edited by users should they wish to validate the content of
their extensions or payloads. No changes are necessary to the schemas if it is not
important to validate these portions of the document.
Should users wish to impose constraints on the extension or the payload contents, the only edits necessary of the content schema are for the importation of the schemas to be engaged for validation purposes. No edits are necessary for the content element, though one may wish to do so to exclude content other than that for which schemas are provided.
The extension content schema fragment describes constraints on content placed in extensions.
The extension content element’s name is <{extensions
prefix}:ExtensionContent>, for example,
<ext:ExtensionContent>. It is the last child element of
<{extensions prefix}:XHEExtension>.
Any given extension content may have zero or one apex (or top-most) element in the XML element tree. The absence of content is provided for situations where a processing application chooses to remove foreign unrecognized-namespace elements from the XML element tree.
The distributed version of this file imports the version of XAdES schemas that are current at the time of publication. XAdES constructs are used within W3C XML Digital Signatures. These import directives can be replaced with the importation of future versions of XAdES schemas as needed.
XHE-XAdES01903v132-201601-1.0.xsdthe v1.3.2 XAdES schema fragment from the etsi.org web site
XHE-XAdES01903v141-201601-1.0.xsdthe v1.4.1 XAdES schema fragment from the etsi.org web site
The payload content schema fragment describes constraints on content placed in payloads.
The payload content element’s name is <{aggregate
prefix}:PayloadContent>, for example,
<eac:PayloadContent>. It is the last child element of
<{aggregate prefix}:Payload>.
Any given payload content element may have as its child exactly one apex (or top-most) element in the XML element tree, or it may consist solely of text that would typically represent encrypted content or non-XML content. Special care needs to be taken that all non-XML payload content is encoded according to XML text encoding rules, such as the escaping of special markup characters, so as to permit an XML processing application to correctly interpret the non-XML content.
The schema declarations are unable to trigger a constraint error in the situation where the payload content has a combination of both text and a single element. Detecting such a condition is the responsibility of the processing agent.
The schema declarations are unable to trigger a constraint error in the situation where the payload content is empty. Detecting such a condition is the responsibility of the processing agent.
In the Exchange Header Envelope model each BBIE is indicated to have a particular component name (specifying the element name) and to be of a particular unqualified data type (specifying the base type value constraints and the attributes). Writers of extensions using CCTS and their own BBIEs need to know the available unqualified data types for their extended business objects.
Based on the 10 approved core component types described in section 8.1 of [CCTS 2.01], there are 20 available unqualified data types for BBIE values. Each data type has a constraint on its content (the component) and a possibly-empty selection of available possibly-mandatory attributes (the supplementary components).
Note
Not all of the unqualified data types listed in this table are used in the standardized components of the header envelope. All defined types are enumerated here for completeness in the event that a CCTS-based extension is created by a community of users that relies on one of the unqualified data types not used by the standardized components of the header envelope.
Appendix A Package structure (Informative)
This Committee Specification 03 is published as a zip archive in the https://docs.oasis-open.org/bdxr/xhe/v1.0/cs03/ directory. Unzipping this archive creates a directory tree containing a number of files and subdirectories. Note that while the two XML files comprise the revisable version of this specification, this revisable XML may not be directly viewable in all currently available web browsers.
The base directory has the following files:
The revisable form of the document.
An HTML rendering of the document.
A PDF rendering of the document.
The document model is expressed in four ways, found in four files of the model subdirectory:
model information expressed in an Open Office spreadsheet
model information expressed in an Excel spreadsheet
model information expressed in a genericode [genericode] file
model information expressed in hyperlinked human-readable tables as HTML
These are the informative subdirectories in the package:
Diagrams and illustrations used in this specification.
DocBook stylesheets for viewing in HTML the XML of this work product.
Demonstrative validation of the example instances with the header envelope schemas.
See Appendix E, Demonstration XML environment (Informative) for details.
The normative subdirectories in the package are listed in normative clauses.
Appendix B Revision History (Informative)
XHE version 1.0 establishes the initial suite of semantic components as a basis for all subsequent minor revisions of the Exchange Header Envelope.
This also establishes the namespaces to be used for all subsequent minor revisions of the Exchange Header Envelope.
Committee Specification 02 differs from Committee Specification 01 by rewording the conformance clauses to accommodate an enveloped header.
Appendix C Acknowledgements (Informative)
The following individuals have participated in the creation of this specification and are gratefully acknowledged:
| Kenneth Bengtsson (co-chair) |
| Michel Bormans |
| Gait Boxman |
| Anders Grangard (co-chair) |
| G. Ken Holman (editor) |
Appendix D Encrypting payloads to multiple recipients (Informative)
The XHE supports sending business documents to multiple recipients using a single envelope, which is obtained by adding multiple instances of the ToParty element to the XHE envelope.
When encrypting payloads of envelopes with multiple recipients, users SHOULD make use of encryption technologies that support multiple recipients so that an encrypted payload to multiple recipients can be contained in a single instance of an XHE envelope’s PayloadContent. Examples of encryption technologies supporting multiple recipients are [RFC5652], [RFC4880] and [XMLENC-CORE1].
The workings of individual encryption technologies and methodologies are beyond the scope of this specification.
Appendix E Demonstration XML environment (Informative)
A working example of using the schemas with an XML instance is demonstrated in the
val/ directory.
The following support files are in this directory:
Windows invocation of the testing of the sample files
shell invocation of the testing of the sample files
Windows invocation of the two-pass validation of a single file
shell invocation of the two-pass validation of a single file
Windows invocation of the schema validation of a single file
shell invocation of the schema validation of a single file
Windows invocation of XSLT transformation on a single file
shell invocation of XSLT transformation on a single file
This directory has a number of simple test files:
a simple envelope with three payload instances, the second of which is simple text (note the escaped special characters) and the other two of which are XML
<?xml version="1.0" encoding="UTF-8"?> <XHE xmlns="oasis-cefact-xhe-1.0-ExchangeHeaderEnvelope" xmlns:xhb="oasis-cefact-xhe-1.0-BasicComponents" xmlns:xha="oasis-cefact-xhe-1.0-AggregateComponents" xmlns:ext="oasis-cefact-xhe-1.0-ExtensionComponents"> <xhb:XHEVersionID>1.0</xhb:XHEVersionID> <xha:Header> <xhb:ID>123</xhb:ID> <xhb:CreationDateTime>2015-02-08T20:34:00-04:00</xhb:CreationDateTime> <xha:BusinessScope> <xha:BusinessScopeCriterion> <xhb:BusinessScopeCriterionTypeCode >test</xhb:BusinessScopeCriterionTypeCode> <xhb:BusinessScopeCriterionValue>123</xhb:BusinessScopeCriterionValue> </xha:BusinessScopeCriterion> <xha:ExternalReference> <xhb:ID>http://www.company.com</xhb:ID> </xha:ExternalReference> </xha:BusinessScope> <xha:FromParty> <xha:PartyIdentification> <xhb:ID>A</xhb:ID> </xha:PartyIdentification> </xha:FromParty> <xha:ToParty> <xha:PartyIdentification> <xhb:ID>B</xhb:ID> </xha:PartyIdentification> </xha:ToParty> </xha:Header> <xha:Payloads> <xha:Payload> <xhb:InstanceEncryptionIndicator>false</xhb:InstanceEncryptionIndicator> <xha:PayloadContent> <myDocumentHere> <myElement>My Content</myElement> <myElement>My Content</myElement> <myElement>My Content</myElement> </myDocumentHere> </xha:PayloadContent> </xha:Payload> <xha:Payload> <xhb:ContentTypeCode>text/plain</xhb:ContentTypeCode> <xhb:InstanceEncryptionIndicator>false</xhb:InstanceEncryptionIndicator> <xha:PayloadContent> Non-XML payload here, with sensitive characters escaped such as &, < and ]]>. Any text, provided it has been escaped, can be included in a payload. </xha:PayloadContent> </xha:Payload> <xha:Payload> <xhb:InstanceEncryptionIndicator>false</xhb:InstanceEncryptionIndicator> <xha:PayloadContent> <myOtherDocumentHere> <myOtherElement>My Content</myOtherElement> <myOtherElement>My Content</myOtherElement> <myOtherElement>My Content</myOtherElement> </myOtherDocumentHere> </xha:PayloadContent> </xha:Payload> </xha:Payloads> </XHE>an envelope document with an XML well-formedness error (the end tag for the creation date and time is missing the closing right-angle bracket)
an envelope document with an XML validity error (a misspelled element for the creation date and time)
a simple envelope with a user-defined extension adding information to the envelope
a simple envelope with a user-defined extension adding information to the envelope
To invoke the schemas with the demonstration instances, navigate to the directory and invoke the test script:
in Windows:
test.batin shell:
sh test.sh
The result on the screen should appear as follows:
val $ sh test.sh
############################################################
Validating simpleExample.xml
############################################################
============== Phase 1: XSD schema validation ==============
No schema validation errors.
============ Phase 2: XSLT code list validation ============
No code list validation errors.
############################################################
Validating simpleExampleTyped.xml
############################################################
============== Phase 1: XSD schema validation ==============
No schema validation errors.
============ Phase 2: XSLT code list validation ============
No code list validation errors.
############################################################
Validating simpleExampleFailSyntax.xml
############################################################
============== Phase 1: XSD schema validation ==============
org.xml.sax.SAXParseException; systemId: file:///Users/admin/t/
artefacts-xhe-v1.0-csd01wd04-test/val/simpleExampleFailSyntax.xml;
lineNumber: 10; columnNumber: 5; The end-tag for element type
"xhb:CreationDateTime" must end with a '>' delimiter.
at org.apache.xerces.parsers.AbstractSAXParser.parse(Unknown Source)
at org.apache.xerces.jaxp.SAXParserImpl$JAXPSAXParser.parse(Unknown Source)
at org.apache.xerces.jaxp.SAXParserImpl.parse(Unknown Source)
at javax.xml.parsers.SAXParser.parse(SAXParser.java:274)
at com.nwalsh.parsers.XJParser.xsdParse(Unknown Source)
at com.nwalsh.parsers.XJParser.parse(Unknown Source)
at com.nwalsh.parsers.XJParse.run(Unknown Source)
at com.nwalsh.parsers.XJParse.main(Unknown Source)
Exception in thread "main" java.lang.NullPointerException
at com.nwalsh.parsers.XJParser.printParseStats(Unknown Source)
at com.nwalsh.parsers.XJParse.run(Unknown Source)
at com.nwalsh.parsers.XJParse.main(Unknown Source)
Attempting well-formed, namespace-aware parse
Fatal error:file:///Users/admin/t/artefacts-xhe-v1.0-csd01wd04-test/
val/simpleExampleFailSyntax.xml:10:5:The end-tag for element type
"xhb:CreationDateTime" must end with a '>' delimiter.
############################################################
Validating simpleExampleFailModel.xml
############################################################
============== Phase 1: XSD schema validation ==============
Attempting well-formed, namespace-aware parse
Error:file:///Users/admin/t/artefacts-xhe-v1.0-csd01wd04-test/val/
simpleExampleFailModel.xml:9:29:cvc-complex-type.2.4.a: Invalid content
was found starting with element 'xhb:CreationDateTimeXX'. One of
'{"oasis-cefact-xhe-1.0-BasicComponents":CreationDateTime}' is expected.
Parse succeeded (0.7) with 1 error and no warnings.
############################################################
Validating simpleExampleExtension.xml
############################################################
============== Phase 1: XSD schema validation ==============
No schema validation errors.
============ Phase 2: XSLT code list validation ============
No code list validation errors.
val $ The test script invokes the validation script using the following::
in Windows:
validate.bat schema-file instance-filein shell:
sh validate.sh schema-file instance-file
The validation script invokes the schema script using the following:
in Windows:
w3cschema.bat schema-file instance-filein shell:
sh w3cschema.sh schema-file instance-file
The validation script invokes the XSLT script using the following:
in Windows:
xslt.bat instance-file stylesheet-file output-filein shell:
sh xslt.sh instance-file stylesheet-file output-file
The empty stylesheet XHE-DefaultDTQ-1.0.xsl is a placebo that would be replaced
with an XSLT stylesheet imposing value validation constraint checking on a given instance of
an exchange header envelope. An example of such data type qualification checking would be for
code list enumerations.
Components of two freely available software distributions were used to create the tools in
the val directory. Sources are given below so that these components can be
updated as later releases become available.
xjparse.jar(renamed fromxjparse-2.0.1.jar) and the files in the “val/lib” directory are from the Xjparse 2.0.1 distribution atsaxon.jaris from the Saxon 6.5.5 distribution at