XACML MAP Authorization Profile Version 1.0
OASIS Standard
19 January 2015
Specification URIs
This version:
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/os/xacml-map-authz-v1.0-os.doc (Authoritative)
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/os/xacml-map-authz-v1.0-os.html
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/os/xacml-map-authz-v1.0-os.pdf
Previous version:
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/csprd01/xacml-map-authz-v1.0-csprd01.doc (Authoritative)
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/csprd01/xacml-map-authz-v1.0-csprd01.html
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/csprd01/xacml-map-authz-v1.0-csprd01.pdf
Latest version:
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/xacml-map-authz-v1.0.doc (Authoritative)
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/xacml-map-authz-v1.0.html
http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/xacml-map-authz-v1.0.pdf
Technical Committee:
OASIS eXtensible Access Control Markup Language (XACML) TC
Chairs:
Bill Parducci (bill@parducci.net), Individual
Hal Lockhart (hal.lockhart@oracle.com), Oracle
Editors:
Richard Hill (richard.c.hill@boeing.com), The Boeing Company
John Tolbert (john.tolbert@queraltinc.com), Queralt, Inc.
Steve Legg (steven.legg@viewds.com), ViewDS
Related work:
This specification is related to:
Abstract:
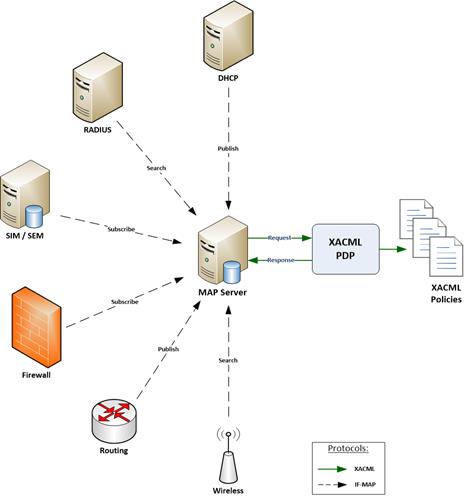
This specification defines a profile for the use of XACML in expressing policies for TCG TNC Metadata Access Points (MAP). It defines standard attribute identifiers useful in such policies, in which a MAP utilizes an XACML PDP to make MAP content authorization decisions.
Status:
This document was last revised or approved by the membership of OASIS on the above date. The level of approval is also listed above. Check the “Latest version” location noted above for possible later revisions of this document. Any other numbered Versions and other technical work produced by the Technical Committee (TC) are listed at https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml#technical.
TC members should send comments on this specification to the TC’s email list. Others should send comments to the TC by using the “Send A Comment” button on the Technical Committee’s web page at https://www.oasis-open.org/committees/xacml/.
For information on whether any patents have been disclosed that may be essential to implementing this specification, and any offers of patent licensing terms, please refer to the Intellectual Property Rights section of the Technical Committee web page (https://www.oasis-open.org/committees/xacml/ipr.php).
Citation format:
When referencing this specification the following citation format should be used:
[xacml-map-authz-v1.0]
XACML MAP Authorization Profile Version 1.0. Edited by Richard Hill, John Tolbert, and Steve Legg. 19 January 2015. OASIS Standard. http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/os/xacml-map-authz-v1.0-os.html. Latest version: http://docs.oasis-open.org/xacml/xacml-map-authz/v1.0/xacml-map-authz-v1.0.html.
Notices
Copyright © OASIS Open 2015. All Rights Reserved.
All capitalized terms in the following text have the meanings assigned to them in the OASIS Intellectual Property Rights Policy (the "OASIS IPR Policy"). The full Policy may be found at the OASIS website.
This document and translations of it may be copied and furnished to others, and derivative works that comment on or otherwise explain it or assist in its implementation may be prepared, copied, published, and distributed, in whole or in part, without restriction of any kind, provided that the above copyright notice and this section are included on all such copies and derivative works. However, this document itself may not be modified in any way, including by removing the copyright notice or references to OASIS, except as needed for the purpose of developing any document or deliverable produced by an OASIS Technical Committee (in which case the rules applicable to copyrights, as set forth in the OASIS IPR Policy, must be followed) or as required to translate it into languages other than English.
The limited permissions granted above are perpetual and will not be revoked by OASIS or its successors or assigns.
This document and the information contained herein is provided on an "AS IS" basis and OASIS DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT INFRINGE ANY OWNERSHIP RIGHTS OR ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
OASIS requests that any OASIS Party or any other party that believes it has patent claims that would necessarily be infringed by implementations of this OASIS Committee Specification or OASIS Standard, to notify OASIS TC Administrator and provide an indication of its willingness to grant patent licenses to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification.
OASIS invites any party to contact the OASIS TC Administrator if it is aware of a claim of ownership of any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may include such claims on its website, but disclaims any obligation to do so.
OASIS takes no position regarding the validity or scope of any intellectual property or other rights that might be claimed to pertain to the implementation or use of the technology described in this document or the extent to which any license under such rights might or might not be available; neither does it represent that it has made any effort to identify any such rights. Information on OASIS' procedures with respect to rights in any document or deliverable produced by an OASIS Technical Committee can be found on the OASIS website. Copies of claims of rights made available for publication and any assurances of licenses to be made available, or the result of an attempt made to obtain a general license or permission for the use of such proprietary rights by implementers or users of this OASIS Committee Specification or OASIS Standard, can be obtained from the OASIS TC Administrator. OASIS makes no representation that any information or list of intellectual property rights will at any time be complete, or that any claims in such list are, in fact, Essential Claims.
The name "OASIS" is a trademark of OASIS, the owner and developer of this specification, and should be used only to refer to the organization and its official outputs. OASIS welcomes reference to, and implementation and use of, specifications, while reserving the right to enforce its marks against misleading uses. Please see https://www.oasis-open.org/policies-guidelines/trademark for above guidance.
Table of Contents
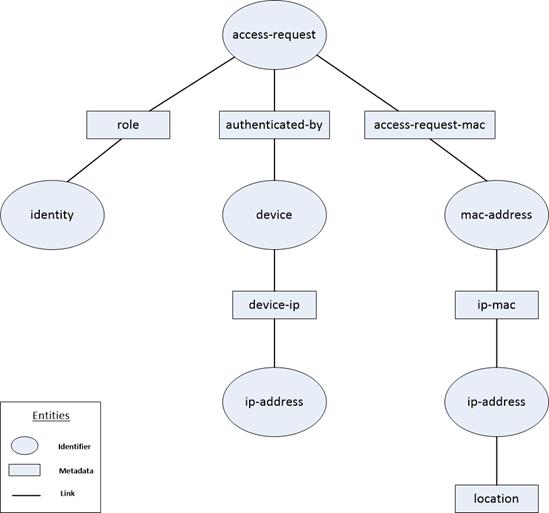
2.2.4 Is-Map-Client-Identifier