Electronic Identity Credential Trust Elevation Framework Version 1.0
Committee Specification 01
22 May 2014
Specification URIs
This version:
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/cs01/trust-el-framework-v1.0-cs01.doc (Authoritative)
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/cs01/trust-el-framework-v1.0-cs01.html
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/cs01/trust-el-framework-v1.0-cs01.pdf
Previous version:
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/csprd01/trust-el-framework-v1.0-csprd01.doc (Authoritative)
Latest version:
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/trust-el-framework-v1.0.doc (Authoritative)
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/trust-el-framework-v1.0.html
http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/trust-el-framework-v1.0.pdf
Technical Committee:
OASIS Electronic Identity Credential Trust Elevation Methods (Trust Elevation) TC
Chairs:
Abbie Barbir (abbie.barbir@bankofamerica.com), Bank of America
Don Thibeau (don@openidentityexchange.org), Open Identity Exchange
Editors:
Peter Alterman (peter.alterman@nih.gov), SAFE-BioPharma Assn
Shaheen Abdul Jabbar (shaheen.abduljabbar@jpmchase.com), JPMorgan Chase Bank, N.A.
Abbie Barbir (abbie.barbir@bankofamerica.com), Bank of America
Mary Ruddy (mary@meristic.com), Identity Commons
Steve Olshansky (steveo@luminagroup.com), Individual
Related work:
This specification is related to:
Abstract:
This document is a specification that recommends particular methods as satisfying defined degrees of assurance for elevating trust in an electronic identity credential, to assure the submitter's identity sufficiently to support elevation between each pair of assurance levels to transact business where material amounts of economic value or personally identifiable data are involved. Alternative and optional methods may be included. The description of each recommended method shall include functional definitions of the types of identity and assertion data employed by each method, and may include specification of the data services required in each elevation, substantive data exchange patterns or models, message exchange patterns or models, and such other elements as the TC deems useful.
Status:
This document was last revised or approved by the OASIS Electronic Identity Credential Trust Elevation Methods (Trust Elevation) TC on the above date. The level of approval is also listed above. Check the “Latest version” location noted above for possible later revisions of this document.
Technical Committee members should send comments on this specification to the Technical Committee’s email list. Others should send comments to the Technical Committee by using the “Send A Comment” button on the Technical Committee’s web page at https://www.oasis-open.org/committees/trust-el/.
For information on whether any patents have been disclosed that may be essential to implementing this specification, and any offers of patent licensing terms, please refer to the Intellectual Property Rights section of the Technical Committee web page (https://www.oasis-open.org/committees/trust-el/ipr.php).
Citation format:
When referencing this specification the following citation format should be used:
[trust-el-framework-v1.0]
Electronic Identity Credential Trust Elevation Framework Version 1.0. Edited by Peter Alterman, Shaheen Abdul Jabbar, Abbie Barbir, Mary Ruddy, and Steve Olshansky. 22 May 2014. OASIS Committee Specification 01. http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/cs01/trust-el-framework-v1.0-cs01.html. Latest version: http://docs.oasis-open.org/trust-el/trust-el-framework/v1.0/trust-el-framework-v1.0.html.
Notices
Copyright © OASIS Open 2014. All Rights Reserved.
All capitalized terms in the following text have the meanings assigned to them in the OASIS Intellectual Property Rights Policy (the "OASIS IPR Policy"). The full Policy may be found at the OASIS website.
This document and translations of it may be copied and furnished to others, and derivative works that comment on or otherwise explain it or assist in its implementation may be prepared, copied, published, and distributed, in whole or in part, without restriction of any kind, provided that the above copyright notice and this section are included on all such copies and derivative works. However, this document itself may not be modified in any way, including by removing the copyright notice or references to OASIS, except as needed for the purpose of developing any document or deliverable produced by an OASIS Technical Committee (in which case the rules applicable to copyrights, as set forth in the OASIS IPR Policy, must be followed) or as required to translate it into languages other than English.
The limited permissions granted above are perpetual and will not be revoked by OASIS or its successors or assigns.
This document and the information contained herein is provided on an "AS IS" basis and OASIS DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT INFRINGE ANY OWNERSHIP RIGHTS OR ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
OASIS requests that any OASIS Party or any other party that believes it has patent claims that would necessarily be infringed by implementations of this OASIS Committee Specification or OASIS Standard, to notify OASIS TC Administrator and provide an indication of its willingness to grant patent licenses to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification.
OASIS invites any party to contact the OASIS TC Administrator if it is aware of a claim of ownership of any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may include such claims on its website, but disclaims any obligation to do so.
OASIS takes no position regarding the validity or scope of any intellectual property or other rights that might be claimed to pertain to the implementation or use of the technology described in this document or the extent to which any license under such rights might or might not be available; neither does it represent that it has made any effort to identify any such rights. Information on OASIS' procedures with respect to rights in any document or deliverable produced by an OASIS Technical Committee can be found on the OASIS website. Copies of claims of rights made available for publication and any assurances of licenses to be made available, or the result of an attempt made to obtain a general license or permission for the use of such proprietary rights by implementers or users of this OASIS Committee Specification or OASIS Standard, can be obtained from the OASIS TC Administrator. OASIS makes no representation that any information or list of intellectual property rights will at any time be complete, or that any claims in such list are, in fact, Essential Claims.
The name "OASIS" is a trademark of OASIS, the owner and developer of this specification, and should be used only to refer to the organization and its official outputs. OASIS welcomes reference to, and implementation and use of, specifications, while reserving the right to enforce its marks against misleading uses. Please see https://www.oasis-open.org/policies-guidelines/trademark for above guidance.
Table of Contents
2.1 A Word About Credential-Based Trust vs. Transactional Trust
2.2 Goals of the Third Deliverable
3 Methodology for Third Deliverable
3.1 Threat Vectors and Trust Elevation Techniques.
3.2 Authentication Risk Vectors and Mitigation Strategies
4 Risk Assessment Methodologies and Authentication Strength
4.2 Authentication Risk Assessment
4.3.1 Authentication Strength Evaluation
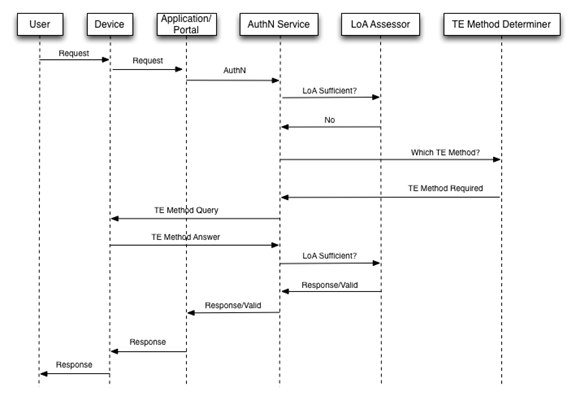
A.1 Use Case Example of Trust Elevation
1.1 Terminology
The key words “MUST”, “MUST NOT”, “REQUIRED”, “SHALL”, “SHALL NOT”, “SHOULD”, “SHOULD NOT”, “RECOMMENDED”, “MAY”, and “OPTIONAL” in this document are to be interpreted as described in [RFC2119].
1.2 Normative References
[RFC2119] Bradner, S., “Key words for use in RFCs to Indicate Requirement Levels”, BCP 14, RFC 2119, March 1997. http://www.ietf.org/rfc/rfc2119.txt.
1.3 Non-Normative References
NIST SP800-53-3 Joint Task Force Transformation Initiative, Recommended Security Controls for Federal Information Systems and Organizations, August 2009. http://csrc.nist.gov/publications/nistpubs/800-53-Rev3/sp800-53-rev3-final_updated-errata_05-01-2010.pdf
NIST SP 800-63-1 Burr, William E., Dodson, Donna F., Newton, Elaine M., Perlner, Ray A., Polk, W. Timothy, Gupta, Sarbari, Nabbus, Emad A., Electronic Authentication Guideline, Recommendations of the National Institute of Standards and Technology, December 2011. http://csrc.nist.gov/publications/nistpubs/800-63-1/SP-800-63-1.pdf
ITU-T X.1254 ITU Telecommunication Standardization Sector (ITU-T) Entity authentication assurance framework, September 2012. http://www.itu.int/rec/T-REC-X.1254/en
NIST SP 800-53-2 (Proposed text) Wilsher, R.,
Zygma LLC, Detailed mapping of IS27001:2005 (requirements and controls),
prepared as a potential Annex for SP 800-53 Rev2, April 2008.
http://www.zygma.biz/Pdf/NIST_SP800-53-rev2_v1-0-0_IS27001mapping.pdf
(Note that this Publication has been superseded by SP 800-53-3 and -4; see note in text for further comment.)
OMB M-04-04 Joshua B. Bolten, U.S.
Government Office of Management and Budget,
E- Authentication Guidance for Federal Agencies, December 2003.
http://www.whitehouse.gov/sites/default/files/omb/memoranda/fy04/m04-04.pdf
Risk Assessment
Methodologies National Strategy for Trusted Identities in Cyberspace (NSTIC), April 25, 2013, http://nstic.blogs.govdelivery.com/2013/04/25/risk-assessment-methodologies-and-authentication-strength/
Trust Elevation
Use Case National Strategy for Trusted Identities in
Cyberspace (NSTIC) Identity
Ecosystem Steering Group
https://www.idecosystem.org/wiki/Trust_Elevation_Use_Case
FICAM Trust
Framework
Solutions Federal Identity, Credential and
Access Management (FICAM)
http://www.idmanagement.gov/trust-framework-solutions
Federal Public
Key Infrastructure
(PKI) Policy
Authority http://www.idmanagement.gov/federal-public-key-infrastructure-policy-authority
NISTIR 7298,
R2 Richard Kissel, Editor, NIST
Computer Security Division, Information Technology Laboratory, Glossary
of Key Information Security Terms, May 2013
http://nvlpubs.nist.gov/nistpubs/ir/2013/NIST.IR.7298r2.pdf
CNSS Instruction
(CNSSI) 4009 Committee on National Security
Systems (CNSS) Instruction No. 4009, National Information Assurance (IA)
Glossary, April 2010
https://www.cnss.gov/Assets/pdf/cnssi_4009.pdf
NSTIC Pilot
Common
Considerations 3 National Strategy for Trusted
Identities in Cyberspace (NSTIC) Risk Assessment Methodologies
and Authentication Strength
http://nstic.blogs.govdelivery.com/2013/04/25/risk-assessment-methodologies-and-authentication-strength/
ISO/IEC
27001:2013 ISO (International Organization for Standardization) and IEC (International Electrotechnical Commission) Information technology -- Security techniques -- Information security management systems -- Requirements http://www.iso.org/iso/home/store/catalogue_ics/catalogue_detail_ics.htm?csnumber=54534
CESG Good
Practice Guide 44 CESG (UK National Technical Authority on Information Assurance) and UK Cabinet Office, Government Digital Services, Authentication Credentials in Support of HMG Online Services, May 2013, Issue No: 1.2
https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/204447/GPG_44_-_authentication_credentials_in_support_of_HMG_online_services_issue_1.2_May_2013_1_.pdf
CESG Good
Practice Guide 45 CESG (UK National Technical Authority on Information Assurance) and UK Cabinet Office, Government Digital Services, Identity Proofing and Verification of an Individual, issue 2.1, September 2013, https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/204448/GPG_45_Identity_proofing_and_verification_of_an_individual_2.0_May-2013.pdf
This document, the third deliverable of the OASIS Trust Elevation Technical Committee, builds on the work of the first two. To recap: the first deliverable, Survey of Methods of Trust Elevation Version 1.0, consists of a broad overview of current and near-future online trust elevation techniques used for (or capable of) raising a relying party’s assurance that the user requesting access to its resources is actually the person he or she claims to be. The second deliverable, Analysis of Methods of Trust Elevation Version 1.0, evaluated how each of the identified trust elevation mechanisms operated and what threats they mitigated that added to the relying party’s confidence in the identity asserted. A discussion of the methodology used to analyze the mechanisms has been included in that deliverable.
As has been the pattern for this TC’s deliverables, this third one builds on the work of the first two and seeks to formulate a useful approach for enabling relying parties to implement one or more trust elevation methods in order to raise their confidence in the identity of the users requesting access to their online systems and resources to the extent necessary to adequately mitigate their risk exposures.
The third deliverable is an abstraction that helps to develop applications conforming to an accepted way of elevating trust on an electronic identity. Adopting this framework reduces research time and cost. It improves efficiency in the architectural and engineering efforts of building an electronic identity system. This will also help in the integration of systems built by various parties and may impact existing systems that are not in conformity.
2.1 A Word About Credential-Based Trust vs. Transactional Trust
The eCommerce and eGov Services cyber-world currently uses two models for secure trusted transactions. One is the credential model, in which the credential carries the trust, and its trustworthiness comes from the credential issuer. This model presumes a user with one or more credentials of various degrees of trustworthiness using an appropriate credential to log on to a networked application. In the social media world, it’s the OpenID userID/password pair. In the U.S. eGov world, it’s the digital certificate. The online application (or its proxy) receives the credential, validates it, and then makes a decision about whether to grant the user access to a resource based upon an authorization determination. The credential model allows the trust and data contained in the credential to be used by many applications at many sites. In the credential model, all the applications must trust the credential issuer as much as or more than the credential user.
The other, the transaction model, is the extent to which users are deemed to be who they say they are based upon factors and tests that the application applies. To the user, this model appears very similar to the credential model: user logs on to an application with some sort of assertion of identity, explicitly (e.g., userID/password) or implicitly (e.g., RP application scans user’s machine for a previously-issued cookie) but instead of validating the credential and authenticating the user into the application proper, the application starts a series of tests and challenges. The transaction model allows each application to determine trust and reliability each time the user goes to a different application, and the application (or an authentication layer at the RP) manages responsibility for that trust by creating and managing its own trust architecture (based on some risk model). Thus the extent to which users are deemed to be who they say they are depends on factors and tests that the application applies. The first deliverable of this TC summarized the types of tests and challenges currently in general use or soon to be in general use on the Internet.
While the trust elevation methods described and analyzed by this TC form the preponderance of tests and challenges in use by many online applications and services, they may be used freely in conjunction with credential-based authentication services as well. That is, some transaction-based authentication services may consume identity credentials secondarily to increase their confidence in the identity of the user at the other side of the transaction. Likewise, some credential-based authentication services may increase their trust in the identity asserted by the credential by employing one or more of the described methods secondarily. Therefore, the methods described in this and the prior documents apply equally to both approaches to electronic identity assertion.
2.2 Goals of the Third Deliverable
· to identify a single set of criteria that many risk and risk mitigation models could be evaluated against (ITU-T X.1254),
· to array each of the models against those criteria in such a way that they could be compared to each other (the columns), and
· to create viable crosswalks between models by aligning each one’s elements with the common threat vectors from X.1254 in rows.
Achieving these goals will make possible translation between credential-based trust models and transaction-based trust models, as well as between individual applications and Trust Frameworks, which can enable further interoperability and trust between differing domains. Note that the focus of this document is trust elevation, and not credential management.
The authors note the distinction between roles and certifications vs. data elements about the individual, and acknowledge that required attribute bundles are not fixed. The Identity Provider (IdP) makes its assertion based on its own rules/regulations or other determination, which may include what the Relying Party (RP) wants. Trust Elevation enables enhanced confidence in the assertion of one or more data elements that the IdP asserts.
There is a weak binding between user and device, and thus it cannot be assumed that device == user unless additional contextual factors are integrated and associated with the user-device pair. Binding user to device is often transaction-based.
Continuous authentication can be viewed as elevating trust at various points (or stages of transactions) based upon some risk value. Trust Elevation is not static, but rather it is a multi-vector process -- access control based upon a dynamic view of identity, and configurable policies.
Note: dynamic authorization and continuous authentication are becoming very important topics, and are being addressed elsewhere. Thus they are out of scope for this document.
The focus of this document is on the combination of data elements that IdPs use
to assert an identity online, separate from all other data elements related to the
individual or their associated device(s). Note that one of the most frequently
used methods of Trust Elevation is to require additional attributes about the
user requesting access, therefore Trust Elevation can occur when additional
attributes extrinsic to the initial identity assertion data elements are
utilized. However, we consider extended attributes to be outside of the
immediate scope of this document.
The intended audience for this document is IT staff or management with a general familiarity with security concepts, threats, and risk mitigation approaches.
Fundamentally, all identity assertion processes are designed to identify a user. The fact that the application requires identification in the first place demonstrates that it recognizes some degree of risk to itself, its business processes, and/or its data is inherent in engaging in online transactions. In that context, both credential-based methods for asserting identity and transaction-based methods for asserting identity aim to mitigate that perceived risk to the extent that Relying Parties are willing to engage in the online transaction with end users (with a known acceptable risk to the application owner). All methods aim to mitigate one or more understood risk vectors. This is the locus where identity management and IT security blend into one another.
There are many standards and frameworks for identifying and controlling the known set of risk vectors. Because that set is more or less common to all the standards and frameworks (only the associated analysis and controls processes differ), the TC chose to use the ITU-T X.1254 catalog of risk vectors as the standard list and to prune them down to only those affecting authentication risks. This list is the baseline against which the trust elevation methods have been arrayed. ISO/IEC 29115:2013 is equivalent to ITU-T X.1254 from a technical perspective. As there are no substantive difference between them, the TC chose to focus on ITU-T X.1254 as the framework of this document.
3.1 Threat Vectors and Trust Elevation Techniques
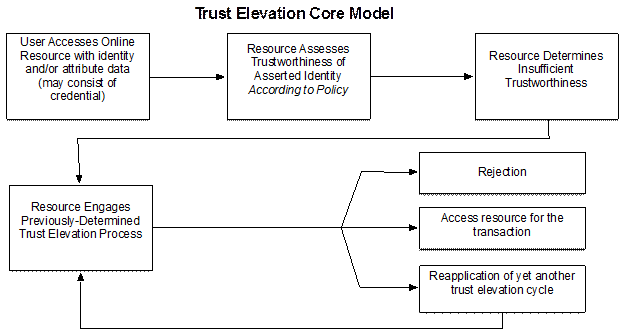
Trust Elevation is a process for mitigating unaddressed threats or substantially improving trust in relation to a previously mitigated threat.
Recommendation on trust elevation implementation: Based upon an assessment of the state of the art by the TC membership, trust in the transaction is increased by what may be comparable to one NIST LoA when one trust elevation technique satisfies either of the following criteria:
1. The technique mitigates a different threat vector — e.g., implementing an additional factor which doesn't share the same vulnerability as the factors previously engaged, or
2. The technique leads to increase in confidence in an existing factor by enhancing a mitigation strategy that has been applied previously.
The way in which a relying party (RP) implements any particular trust elevation method will affect the increment of trust elevation it provides. This determination is clearly a judgment call on the part of the RP and the extent to which it is interoperable with other RPs' practices is dependent upon prior shared policy and practice agreements.
This table arrays threat vectors and mitigation methods for
those particular threat vectors described in ITU-T X.1254. Utilize the table to
identify threat vectors that the initial credential does not mitigate, and then
employ one or more of the associated methods to raise the trust in the
transaction. The TC arrayed the threats and controls in ITU-T X.1254 against
mitigation methods described in NIST SP 800-63-1 and information security
consultant Zygma LLC's analysis of controls from NIST SP 800-53-2. Any LoA or similar model can be used — the NIST LoAs used
here are an example. LoA is simply one configuration, and every RP should
evaluate how to calculate the difference in trust elevation based upon its own
methodology. The TC is aware that all of the documents referenced are
continually being revised, and so this table will need to be revised from time
to time as substantive changes to the source documents are published. The
latest version of this table will be referenced on the TC page:
https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=trust-el.
3.2 Authentication Risk Vectors and Mitigation Strategies
|
Legend: NIST 800-53 Controls |
|
|
· AC-20 Use of External Information Systems · IA-1 Identification and Authentication Policy and Procedures · IA-2 Identification and Authentication (Organizational Users) · IA-3 Device Identification and Authentication · IA-4 Identifier Management · IA-5 Authenticator Management · IA-6 Authenticator Feedback · IA-7 Cryptographic Module Authentication |
· IA-8 Identification and Authentication (Non-Organizational Users) · IA-9 Service Identification and Authentication · IA-10 Adaptive Identification and Authentication · IA-11 Re-authentication · PE-3 Physical Access Control · PE-4 Access Control for Transmission Medium · SA-9 External Information System Services |