TAXII[™] Version 1.1.1. Part 5: Default
Query
Committee Specification Draft 01 /
Public Review Draft 01
06 November 2015
Specification URIs
This version:
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part5-query/taxii-v1.1.1-csprd01-part5-query.docx
(Authoritative)
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part5-query/taxii-v1.1.1-csprd01-part5-query.html
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part5-query/taxii-v1.1.1-csprd01-part5-query.pdf
Previous version:
N/A
Latest version:
http://docs.oasis-open.org/cti/taxii/v1.1.1/taxii-v1.1.1-part5-query.docx
(Authoritative)
http://docs.oasis-open.org/cti/taxii/v1.1.1/taxii-v1.1.1-part5-query.html
http://docs.oasis-open.org/cti/taxii/v1.1.1/taxii-v1.1.1-part5-query.pdf
Technical Committee:
OASIS Cyber Threat Intelligence (CTI)
TC
Chair:
Richard Struse (Richard.Struse@hq.dhs.gov), DHS Office of
Cybersecurity and Communications (CS&C)
Editors:
Mark Davidson (mdavidson@mitre.org), MITRE Corporation
Charles Schmidt (cmschmidt@mitre.org), MITRE Corporation
Bret Jordan (bret.jordan@bluecoat.com), Blue Coat Systems, Inc.
Additional artifacts:
This prose specification is one component of a
Work Product that also includes:
· TAXII Version
1.1.1. Part 1: Overview.
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part1-overview/taxii-v1.1.1-csprd01-part1-overview.html
· TAXII Version
1.1.1. Part 2: Services.
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part2-services/taxii-v1.1.1-csprd01-part2-services.html
· TAXII Version
1.1.1. Part 3: HTTP Protocol Binding.
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part3-http/taxii-v1.1.1-csprd01-part3-http.html
· TAXII Version
1.1.1. Part 4: XML Message Binding.
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part4-xml/taxii-v1.1.1-csprd01-part4-xml.html
· TAXII Version
1.1.1. Part 5: Default Query (this document).
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part5-query/taxii-v1.1.1-csprd01-part5-query.html
· XML schemas:
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/schemas/
Related work:
This specification replaces or supersedes:
· The TAXII
Default Query Specification Version 1.0.
http://taxii.mitre.org/specifications/version1.1/TAXII_Default_Query_Specification.pdf.
This specification is related to:
· TAXII Content
Binding Reference.
http://taxiiproject.github.io/releases/1.1/TAXII_ContentBinding_Reference_v3.pdf
Declared XML namespaces:
· http://docs.oasis-open.org/cti/ns/taxii/xml/binding-1.1.1
· http://docs.oasis-open.org/cti/ns/taxii/default-query-1.1.1
Abstract:
This document describes the TAXII default query.
Status:
This document was last revised or approved by the OASIS Cyber
Threat Intelligence (CTI) TC on the above date. The level of approval is also listed
above. Check the “Latest version” location noted above for possible later
revisions of this document. Any other numbered Versions and other technical work
produced by the Technical Committee (TC) are listed at https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=cti#technical.
TC members should send comments on this specification to the
TC’s email list. Others should send comments to the TC’s public comment
list, after subscribing to it by following the instructions at the “Send A
Comment” button on the TC’s web page at https://www.oasis-open.org/committees/cti/.
For information on whether any patents have been disclosed that
may be essential to implementing this specification, and any offers of patent
licensing terms, please refer to the Intellectual Property Rights section of the
TC’s web page (https://www.oasis-open.org/committees/cti/ipr.php).
Citation format:
When referencing this specification the following citation format
should be used:
[TAXII-Query]
TAXII[™] Version 1.1.1. Part 5: Default Query. Edited
by Mark Davidson, Charles Schmidt, and Bret Jordan. 06 November 2015. OASIS Committee
Specification Draft 01 / Public Review Draft 01.
http://docs.oasis-open.org/cti/taxii/v1.1.1/csprd01/part5-query/taxii-v1.1.1-csprd01-part5-query.html.
Latest version: http://docs.oasis-open.org/cti/taxii/v1.1.1/taxii-v1.1.1-part5-query.html.
Copyright © OASIS Open 2015. All Rights Reserved.
All capitalized terms in the following text have the meanings
assigned to them in the OASIS Intellectual Property Rights Policy (the "OASIS IPR
Policy"). The full Policy may be found at the
OASIS website.
This document and translations of it may be copied and furnished
to others, and derivative works that comment on or otherwise explain it or assist in
its implementation may be prepared, copied, published, and distributed, in whole or
in part, without restriction of any kind, provided that the above copyright notice
and this section are included on all such copies and derivative works. However, this
document itself may not be modified in any way, including by removing the copyright
notice or references to OASIS, except as needed for the purpose of developing any
document or deliverable produced by an OASIS Technical Committee (in which case the
rules applicable to copyrights, as set forth in the OASIS IPR Policy, must be
followed) or as required to translate it into languages other than English.
The limited permissions granted above are perpetual and will not
be revoked by OASIS or its successors or assigns.
This document and the information contained herein is provided
on an "AS IS" basis and OASIS DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING
BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT
INFRINGE ANY OWNERSHIP RIGHTS OR ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS
FOR A PARTICULAR PURPOSE.
OASIS requests that any OASIS Party or any other party that
believes it has patent claims that would necessarily be infringed by implementations
of this OASIS Committee Specification or OASIS Standard, to notify OASIS TC
Administrator and provide an indication of its willingness to grant patent licenses
to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical
Committee that produced this specification.
OASIS invites any party to contact the OASIS TC Administrator if
it is aware of a claim of ownership of any patent claims that would necessarily be
infringed by implementations of this specification by a patent holder that is not
willing to provide a license to such patent claims in a manner consistent with the
IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may
include such claims on its website, but disclaims any obligation to do so.
OASIS takes no position regarding the validity or scope of any
intellectual property or other rights that might be claimed to pertain to the
implementation or use of the technology described in this document or the extent to
which any license under such rights might or might not be available; neither does it
represent that it has made any effort to identify any such rights. Information on
OASIS' procedures with respect to rights in any document or deliverable produced by
an OASIS Technical Committee can be found on the OASIS website. Copies of claims of
rights made available for publication and any assurances of licenses to be made
available, or the result of an attempt made to obtain a general license or permission
for the use of such proprietary rights by implementers or users of this OASIS
Committee Specification or OASIS Standard, can be obtained from the OASIS TC
Administrator. OASIS makes no representation that any information or list of
intellectual property rights will at any time be complete, or that any claims in such
list are, in fact, Essential Claims.
The name "OASIS" is a trademark of OASIS, the owner and developer of this
specification, and should be used only to refer to the organization and its official
outputs. OASIS welcomes reference to, and implementation and use of, specifications,
while reserving the right to enforce its marks against misleading uses. Please see
https://www.oasis-open.org/policies-guidelines/trademark
for above guidance.
Portions copyright © United States Government
2012-2015. All Rights Reserved.
STIX[™], TAXII[™], AND CybOX[™] (STANDARD
OR STANDARDS) AND THEIR COMPONENT PARTS ARE PROVIDED “AS IS” WITHOUT ANY
WARRANTY OF ANY KIND, EITHER EXPRESSED, IMPLIED, OR STATUTORY, INCLUDING, BUT NOT
LIMITED TO, ANY WARRANTY THAT THESE STANDARDS OR ANY OF THEIR COMPONENT PARTS WILL
CONFORM TO SPECIFICATIONS, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A
PARTICULAR PURPOSE, OR FREEDOM FROM INFRINGEMENT, ANY WARRANTY THAT THE STANDARDS OR
THEIR COMPONENT PARTS WILL BE ERROR FREE, OR ANY WARRANTY THAT THE DOCUMENTATION, IF
PROVIDED, WILL CONFORM TO THE STANDARDS OR THEIR COMPONENT PARTS. IN NO EVENT
SHALL THE UNITED STATES GOVERNMENT OR ITS CONTRACTORS OR SUBCONTRACTORS BE LIABLE FOR
ANY DAMAGES, INCLUDING, BUT NOT LIMITED TO, DIRECT, INDIRECT, SPECIAL OR
CONSEQUENTIAL DAMAGES, ARISING OUT OF, RESULTING FROM, OR IN ANY WAY CONNECTED WITH
THESE STANDARDS OR THEIR COMPONENT PARTS OR ANY PROVIDED DOCUMENTATION, WHETHER OR
NOT BASED UPON WARRANTY, CONTRACT, TORT, OR OTHERWISE, WHETHER OR NOT INJURY WAS
SUSTAINED BY PERSONS OR PROPERTY OR OTHERWISE, AND WHETHER OR NOT LOSS WAS SUSTAINED
FROM, OR AROSE OUT OF THE RESULTS OF, OR USE OF, THE STANDARDS, THEIR COMPONENT
PARTS, AND ANY PROVIDED DOCUMENTATION. THE UNITED STATES GOVERNMENT DISCLAIMS ALL
WARRANTIES AND LIABILITIES REGARDING THE STANDARDS OR THEIR COMPONENT PARTS
ATTRIBUTABLE TO ANY THIRD PARTY, IF PRESENT IN THE STANDARDS OR THEIR COMPONENT PARTS
AND DISTRIBUTES IT OR THEM “AS IS.”
1 Introduction. 7
1.1 The Default TAXII[™] Query
Specification. 7
1.1.1 TAXII[™] Query Format ID for
XML. 7
1.2 Terminology.
7
1.3 Normative References. 7
1.4 Terms and Definitions. 7
1.4.1 Default TAXII[™] Query
Terms. 7
2 Status Types. 8
3 TAXII[™] Default
Query. 10
3.1 Query Structure. 10
3.1.1 XML Representation. 11
3.2 Query Information
Structure. 13
3.2.2 XML Representation. 14
3.3 Query Evaluation. 15
4 Targeting
Expressions. 17
4.1 Targeting Expression
Syntax. 17
4.2 Targeting Expression
Vocabularies. 17
4.2.1 STIX[™] Targeting Expression
Vocabulary. 17
4.2.2 Third Party Targeting Expression
Vocabularies. 18
4.2.3 Example Third Party Targeting
Expression Vocabulary. 18
5 Capability
Modules. 19
5.1 Capability Module: Core. 19
5.1.1 Relationship: equals. 19
5.1.2 Relationship:
not_equals. 19
5.1.3 Relationship:
greater_than. 20
5.1.4 Relationship: greater_than_or_equal
20
5.1.5 Relationship: less_than. 20
5.1.6 Relationship: less_than_or_equal
20
5.1.7 Relationship: does_not_exist
21
5.1.8 Relationship: exists. 21
5.1.9 Relationship:
begins_with. 21
5.1.10 Relationship:
ends_with. 21
5.1.11 Relationship: contains. 22
5.2 Capability Module: Regular
Expression. 22
5.2.1 Relationship: matches. 22
5.3 Capability Module –
Timestamp. 22
5.3.1 Relationship: equals. 23
5.3.2 Relationship:
greater_than. 23
5.3.3 Relationship:
greater_than_or_equals. 23
5.3.4 Relationship: less_than. 23
5.3.5 Relationship:
less_than_or_equals. 24
6 Examples. 25
6.1 Query Information Structure
Example. 25
6.2 Query Structure Example -
1. 25
6.3 Query Structure Example –
2. 26
7 Conformance. 27
Appendix A. Acknowledgments. 28
Appendix B. Revision History. 32
The
TAXII[™] Services Specification 1.1.1 defines the TAXII Query capability, which
is an extension point within TAXII. This document defines the Default TAXII Query,
which is one implementation of the TAXII 1.1.1 Query extension point.
1.1 The Default TAXII[™] Query Specification [comment?]
This specification defines the Default TAXII Query, which is one
extension of TAXII Query. As required by the TAXII Services Specification, this
document defines structures to be used for TAXII Query (the Query Structure and Query
Information Structure) as well as semantics and workflows for processing those
structures.
The Default TAXII Capability Specification defines the Default
TAXII Query structure, processing rules for the Default TAXII Query, an XML
representation of the Default TAXII Query structure to be used in conjunction with
the TAXII 1.1.1 XML Message Binding, and concepts fundamental to the Default TAXII
Query.
1.1.1 TAXII[™] Query Format ID for XML [comment?]
The TAXII Query Format ID for the version of the Default TAXII
Query described in this specification is:
urn:oasis:cti:taxii:query:1.1.1
The key words “MUST”, “MUST NOT”,
“REQUIRED”, “SHALL”, “SHALL NOT”,
“SHOULD”, “SHOULD NOT”, “RECOMMENDED”,
“MAY”, and “OPTIONAL” in this document are to be interpreted
as described in [RFC 2119].
1.3 Normative References [comment?]
[RFC
2119]
Bradner, S., “Key words for use in RFCs to Indicate Requirement Levels”,
BCP 14, RFC 2119, March 1997. http://www.ietf.org/rfc/rfc2119.txt.
1.4 Terms and Definitions [comment?]
This document uses the Terms and Definitions defined in the
TAXII Services Specification and TAXII Overview. In addition, this document defines
terms that are assigned a specific meaning within this specification.
1.4.1 Default TAXII[™] Query
Terms [comment?]
Capability Module – A defined set of relationships
(e.g., equals, greater than) that can be used in specifying selection criteria.
Targeting Expression – An expression that specifies
the target region of a record for searching.
Targeting Expression Vocabulary – A defined set of
vocabulary items to be used in a Targeting Expression.
Node – One vocabulary item in a Targeting
Expression Vocabulary.
This document defines three Status Types to use when responding
with an error condition related to a TAXII Default Query. This section contains three
tables: one table describing the new status types (akin to the ‘TAXII Status
Types’ table in the TAXII Services Specification 1.1.1); one table describing
the XML representation of the Status Types (akin to the ‘Defined Status
Types’ table in the XML Message Binding Specification 1.1.1); and one table
describing the XML representation of the Status Detail for each Status Type (akin to
the ‘Defined <Status_Detail>/<Detail> Names and Values table in the
XML Message Binding Specification 1.1.1).
Table 1 - Status Types for TAXII[™] Default Query
|
Status Type
|
Description
|
|
Unsupported Capability Module
|
The requester specified a Capability Module that is not
supported by the TAXII Service.
|
Status Detail Name
|
Status Detail Value
|
|
Supported Capability Modules
|
A list of acceptable Capability Modules.
|
|
|
Unsupported Targeting Expression
|
The requester specified a Targeting Expression that is not
supported by the TAXII Service.
|
Status Detail Name
|
Status Detail Value
|
|
Preferred Scope
|
This field contains a Targeting Expression that
identifies a subset of valid Targeting Expressions. The query provider is
able to provide a response more rapidly to requests that contain a query
when Targeting Expressions in the Preferred Scope are used. For more
information on Preferred Scope, see Section 3.2.1.1.
|
|
Allowed Scope
|
This field contains a Targeting Expression that
identifies a subset of valid Targeting Expressions. The query provider is
able to provide a response to requests that contain a query when
Targeting Expressions in the Allowed Scope are used. For more information
on Allowed Scope, see Section 3.2.1.1.
|
|
|
Unsupported Targeting Expression Vocabulary
|
The requester specified a Targeting Expression Vocabulary
that was not supported.
|
Status Detail Name
|
Status Detail Value
|
|
Supported Targeting Expression IDs
|
A list of acceptable Targeting Expression IDs. Each
Targeting Expression ID indicates an acceptable Targeting Expression
Vocabulary.
|
|
Table 2 – Defined Status Types for TAXII Default
Query
|
@status_type
Value
|
Error Status Type
|
<Status_Detail> name-values
|
|
Name
|
Reqd?
|
|
UNSUPPORTED_CAPABILITY_MODULE
|
Unsupported Capability Module
|
CAPABILITY_MODULE
|
No
|
|
UNSUPPORTED_TARGETING_EXPRESSION
|
Unsupported Targeting Expression
|
PREFERRED_SCOPE
|
Yes*
|
|
ALLOWED_SCOPE
|
|
UNSUPPORTED_TARGETING_EXPRESSION_ID
|
Unsupported Targeting Expression ID
|
TARGETING_EXPRESSION_ID
|
No
|
*At least one of PREFERRED_SCOPE or ALLOWED_SCOPE MUST be
present. Both MAY be present. All PREFERRED_SCOPE Status Details should come before
all ALLOWED_SCOPE Status Details.
Table 3 - Defined <Status_Detail>/<Detail>
Names and Values for TAXII Default Query
|
@status_type Value
|
<Detail> @name
|
<Detail> Value
|
|
UNSUPPORTED_CAPABILITY_MODULE
|
CAPABILITY_MODULE
|
An XML AnyURI indicating a supported Capability Module.
This field may be repeated.
|
|
UNSUPPORTED_TARGETING_EXPRESSION
|
PREFERRED_SCOPE
|
An XML string containing a Targeting Expression
|
|
UNSUPPORTED_TARGETING_EXPRESSION
|
ALLOWED_SCOPE
|
An XML string containing a Targeting Expression.
|
|
UNSUPPORTED_TARGETING_EXPRESSION_ID
|
TARGETING_EXPRESSION_ID
|
An XML AnyURI indicating a supported Targeting Expression
Vocabulary. This field may be repeated.
|
TAXII Default Query allows a Consumer to provide a
Producer with selection criteria to use when fulfilling requests for data from a
TAXII Data Collection. This section defines The TAXII Default Query.
The following table details the query structure of the Default
Query Structure. This structure is used within the Query field of a Poll Request and
the Query field of a Manage Collection Subscription Request with an Action of
SUBSCRIBE. This structure contains the criteria that content should be evaluated
against when fulfilling a subscription or Poll Request.
Table 4 – Default Query Structure
|
Name
|
Required?
|
Multiple?
|
Description
|
|
Default Query
|
|
|
This field contains a TAXII Default Query.
|
|
|
Targeting Expression Vocabulary ID
|
Yes
|
No
|
This field identifies the Target Expression Vocabulary
used in this query. All Target fields in this query MUST use the identified
vocabulary. If the TAXII Service does not support this Targeting Expression ID,
a Status Message with a status of ‘Unsupported Targeting Expression
Vocabulary’ SHOULD be returned.
|
|
Criteria
|
Yes
|
No
|
This field contains the criteria. If
the criteria evaluates to true for a piece of content, that content is said to
match the query.
|
|
|
Operator
|
Yes
|
No
|
This field indicates the logical
operator that should be applied to child Criteria and Criterion to determine
whether content matches this query. Valid values are “and” and
“or”.
- “And” indicates that this Criteria evaluates
to True if and only if all child Criteria and Criterion evaluate to True.
- “Or” indicates that this Criteria evaluates
to True if any child Criteria or Criterion evaluate to True.
|
|
Criteria
|
At least one of either. Can be
multiple of both. All criteria must appear before all criterion.
|
Yes
|
This field contains a Criteria. The subfields of
this Criteria are the same as the parent Criteria (e.g., this is a recursive
field), though they are not listed here.
|
|
Criterion
|
Yes
|
This field contains the criterion.
|
|
|
Negate
|
No
|
No
|
This field indicates whether the
final result of the Criterion should be negated. If absent, treat this field as
“false”.
|
|
Target
|
Yes
|
No
|
This field contains the Targeting Expression for this
Criterion, identifying the region of the record that is being targeted. The
Targeting Expression MUST only use Nodes from the specified Target Expression
Vocabulary. If the TAXII Service does not support this Targeting Expression, a
Status Message with a status of ‘Unsupported Targeting Expression’
SHOULD be returned.
|
|
Test
|
Yes
|
No
|
This field contains the test for the
region of the record identified by the Target.
|
|
|
Capability ID
|
Yes
|
No
|
Contains the Capability ID, which identifies a Capability
Module. If the TAXII Service does not support this Capability Module, a Status
Message with a status of ‘Unsupported Capability Module’ SHOULD be
returned.
|
|
Relationship
|
Yes
|
Yes
|
Contains the relationship. This
value MUST be defined by the Capability Module identified by the Capability
ID.
|
|
Parameter
|
-
|
-
|
Contains the parameter(s) for this test, which take for
form of a name-value pair. Whether a parameter is required, the permissible
values and their meanings, and whether multiple parameters of the same name are
permitted is defined by the Capability Module.
|
|
|
Name
|
Yes
|
No
|
Contains the name of the
parameter.
|
|
|
|
|
|
|
|
|
|
3.1.1 XML Representation [comment?]
This section defines the XML representation of the Query
Structure. This structure is intended for use with the TAXII XML Message Binding
1.1.1 (urn:oasis:cti:taxii:xml:1.1.1).
The XML Namespace for this representation is:
http://docs.oasis-open.org/cti/ns/taxii/default-query-1.1.1
Table 5 - XML Representation of TAXII[™] Default
Query
|
XML Name
|
Data Model Name
|
#
|
Description
|
|
<Default_Query>
|
Default Query
|
1
|
The element name indicates that this is a TAXII Default
Query. Its body MUST consist of only the indicated XML Fields.
|
|
|
@targeting_expression_id
|
Targeting Expression ID
|
1
|
An XML AnyURI indicating the Targeting Expression
Vocabulary that will be used in this query’s Target field(s).
|
|
<Criteria>
|
Criteria
|
1
|
An XML element. Its body consists only of the indicated
XML fields.
|
|
|
@operator
|
Operator
|
1
|
An XML string containing an operator. Must be one of "AND"
or "OR".
|
|
<Criteria>
|
Criteria
|
1-n
|
An XML element. This element MUST
consist only of the indicated XML fields. The subfields of this Criteria are
the same as the parent Criteria (e.g., this is a recursive field), though they
are not listed here.
|
|
<Criterion>
|
Criterion
|
An XML element. This element MUST
consist only of the indicated XML fields.
|
|
|
@negate
|
Negate
|
0-1
|
An XML boolean indicating whether the result of the
Criterion should be negated. The default value for this field is
‘false’.
|
|
<Target>
|
Target
|
1
|
An XML string containing a Targeting Expression
identifying the region of the record that is being targeted.
|
|
<Test>
|
Test
|
1
|
An XML element containing the Test. This element MUST
consist only of the indicated XML fields.
|
|
|
@capability_id
|
Capability ID
|
1
|
An XML AnyURI indicating the Capability Module used in
this Test.
|
|
@relationship
|
Relationship
|
1
|
An XML string containing the relationship.
|
|
<Parameter>
|
Parameter
|
0-n
|
An XML string containing the value of this parameter.
|
|
|
@name
|
Name
|
1
|
An XML string containing the name of this parameter.
|
|
|
|
|
|
|
|
|
|
3.2 Query Information Structure [comment?]
The following table details the query structure of the Default
Query Information Structure. This structure is used within the Supported Query field
of a Discovery Response.
Table 6 - Default Query Information Structure
|
Name
|
Required?
|
Multiple?
|
Description
|
|
Default Query Information
|
Yes
|
No
|
This field contains the query information. This field
indicates which Targeting Expressions and Capability Modules are
supported.
|
|
|
Targeting Expression Information
|
Yes
|
Yes
|
This field contains information related to the Targeting
Expressions that are supported.
|
|
|
Targeting Expression ID
|
Yes
|
No
|
A Targeting Expression ID, Indicating a supported
Targeting Expression Vocabulary.
|
|
Preferred Scope
|
At least one of MUST be present; both MAY be
present.
|
Yes
|
This field contains a Targeting Expression that
identifies a subset of valid Targeting Expressions. The query provider is
able to provide a response more rapidly to requests that contain a query when
Targeting Expressions in the Preferred Scope are used. For more information
on Preferred Scope, see Section 3.2.1.1.
|
|
Allowed Scope
|
Yes
|
This field contains a Targeting Expression that
identifies a subset of valid Targeting Expressions. The query provider is
able to provide a response to requests that contain a query when Targeting
Expressions in the Allowed Scope are used. For more information on Allowed
Scope, see Section 3.2.1.1.
|
|
Capability Module
|
Yes
|
Yes
|
Contains a Capability Module ID,
indicating a supported Capability Module. This may be a Capability Module
defined by this specification or by a third party.
|
3.2.1.1
Preferred Scope and Allowed Scope [comment?]
The Default Query Information structure contains two fields that
indicate the permissible scope of queries: Preferred Scope and Allowed scope. This
section discusses and defines the format of these fields.
Query providers that support a particular
Targeting Expression Vocabulary (e.g., STIX[™]
1.1) may want to support queries against only particular regions of
that Targeting Expression Vocabulary (e.g., Indicators). For this reason, the TAXII
Default Query provides a mechanism for query providers to define the scope of
supported Targeting Expressions (within the overall set of expressions allowed in the
Targeting Expression structure). The scope of permissible Targeting Expressions is
divided into two query-provider defined regions: Preferred Scope (quicker
responses can be provided) and Allowed Scope (responses can
be provided). Generally speaking, Targeting Expressions within a
query provider's Preferred Scope can be serviced more rapidly than Targeting
Expressions within a query provider’s Allowed Scope.
The values of all Preferred Scope and Allowed Scope fields MUST
be Targeting Expressions that are valid per the Targeting Expression ID field of the
Default Query Information structure. Requests that contain queries MUST use Targeting
Expressions that are within the scope described by either the Preferred Scope or
Allowed Scope. Query providers that wish to indicate that all Targeting Expressions
are in scope should use ‘**’ in either the Preferred Scope (if the query
provider can provide a rapid response to any query) or Allowed Scope field (if the
query provider can provide a response to any query).
Figure 1 is a visual representation of how the Preferred and
Allowed Scope are related to the set of all valid Targeting Expressions for a
particular Targeting Expression Vocabulary. Both the Allowed Scope and Preferred
Scope are subsets of all valid Targeting Expressions. If an expression is preferred,
it is by definition allowed.
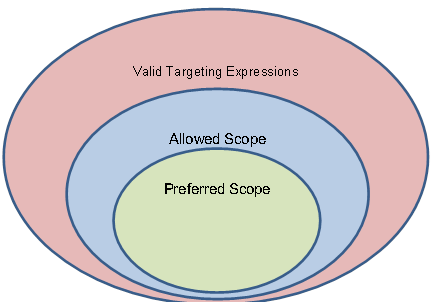
Figure 1- Venn Diagram of Targeting Expression Scope
Example values of these fields (and their meanings):
1. STIX_Package/Indicators/Indicator/** - Indicates that all fields in the STIX
Indicator construct are in scope.
2. **/@id
– Indicates that all STIX id fields are in scope.
3. STIX_Package/STIX_Header/Title – Indicates that the Title of a
STIX document is in scope.
4. ** -
Indicates that all fields are in scope.
3.2.2 XML Representation [comment?]
This section defines the XML representation of the Query
Information Structure. This structure is intended for use with the TAXII XML Message
Binding 1.1.1 (urn:oasis:cti:taxii:xml:1.1.1).
The XML Namespace for this representation is:
http://docs.oasis-open.org/cti/ns/taxii/default-query-1.1.1
|
XML Name
|
Data Model Name
|
Multiple?
|
Description
|
|
<Default_Query_Info>
|
Default Query Information
|
1
|
The element name indicates that this is a query
information structure. Its body consists only of the indicated fields.
|
|
|
<Targeting_Expression_Info>
|
Targeting Expression Information
|
1-n
|
The element name indicates that this is a Targeting
Expression Information field. Its body consists only of the indicated XML
Fields.
|
|
|
@targeting_expression_id
|
Targeting Expression ID
|
1
|
An XML AnyURI containing a Targeting Expression
Vocabulary ID.
|
|
<Preferred_Scope>
|
Preferred Scope
|
1-n
|
An XML String containing a Targeting Expression.
|
|
<Allowed_Scope>
|
Allowed Scope
|
An XML String containing a Targeting Expression.
|
|
<Capability_Module>
|
Capability Module
|
1-n
|
An XML AnyURI indicating a Capability Module.
|
3.3 Query Evaluation [comment?]
This section defines how queries are evaluated.
When a Query structure is present, the consumer is requesting
only the records from a TAXII Data Collection that meet the specified criteria. If a
Query is present and the producer is incapable or unwilling to process the Query, the
producer should indicate this condition with a Status Message, nominally of
“Query Not Supported”.
Queries should be fulfilled in a manner that produces the same
result as following these steps:
1. As an optional first step, inspect
the Query structure for errors (e.g., a relationship that is not valid for a given
Capability Module) and unsupported features (e.g., an unsupported Capability Module
or Targeting Expression). If an error or unsupported feature is detected, respond
with a Status Message that identifies the error condition.
2. For each record in the identified
TAXII Data Collection (the Data Collection name is specified outside of the Query
structure), evaluate the Criteria. If the Criteria evaluates to “true”
the record should be included in the result set.
Criteria should be evaluated in a manner that produces the same
result as following these steps:
1. Create a list of all Child Criteria
(Note that Criteria can be a Child of Criteria. For the purposes of this workflow,
they are distinguished as the Parent Criteria, which is the Criteria that is
evaluated in this workflow, and the Child Criteria, which are immediate descendants
of the Parent Criteria) and Child Criterion.
2. For each Child
Criteria/Criterion:
a. If the Child is a Criteria, evaluate
the Child Criteria to determine if it is True or False by following this workflow
from Step #1.
(Note: This is recursive. Eventually there will be a Criteria that has only Criterion
children.)
b. If the Child is a Criterion, evaluate the
Target against the Test, and apply negation if necessary to determine if the Child
Criterion is True or False.
Note: The authors recognize that this is a non-trivial
“exercise left for the reader”. However, evaluation of individual
Criterion is implementation specific and therefore out of scope for this
specification.
c. If the Child Criteria/Criterion
evaluates to True and the Operator is OR, the Parent Criteria evaluates to True.
d. If the Child Criteria/Criterion evaluates
to True and the Operator is AND, processing continues unless there are no more Child
Criteria/Criterion. If there are no more Child Criteria/Criterion, the Parent
Criteria evaluates to True.
e. If the Child Criteria/Criterion evaluates
to False and the Operator is OR, processing continues unless there are no more Child
Criteria/Criterion. If there are no more Child Criteria/Criterion, the Parent
Criteria evaluates to False.
f. If the Child
Criteria/Criterion evaluates to False and the Operator is AND, the Parent Criteria
evaluates to False.
A Targeting Expression is contained by the Target field of a
Query Structure. Within a Criterion, the Target is used to identify a specific region
of a record to which the Test should be applied. This section defines the Targeting
Expression syntax used by all TAXII Default Queries. The Targeting Expression syntax,
in conjunction with a Targeting Expression Vocabulary, are used to form a Targeting
Expression. This section defines one Targeting Vocabulary that Query providers may
choose to use. Third parties may define additional vocabularies for use with the
Targeting Expression syntax defined by this section.
4.1 Targeting Expression Syntax [comment?]
All Targeting Expressions use a syntax called Slash Notation.
Using the Slash Notation Targeting Expression syntax, a Targeting Expression consists
of one or more of Nodes (recall that one or more Nodes make up a Targeting Expression
Vocabulary) separated by a forward slash (/). A Node can be one of four things:
1. Node – The name of a Node in
the indicated Targeting Expression Vocabulary (This is indicated by the Targeting
Expression ID property of a Query). Field Names are case sensitive unless the
Targeting Expression Vocabulary defines them to be case insensitive.
2. Field Wildcard – This
indicates any Node. Only a single Node is represented. This is indicated by a star
(*).
3. Multi-field Wildcard – This
indicates any Node or series of Nodes. This is indicated by two stars (**).
4.2 Targeting Expression Vocabularies [comment?]
A Targeting Expression vocabulary defines which Nodes are
permitted in a Targeting Expression, the Node hierarchy, and whether wildcards are
permitted. Targeting Expression Vocabularies can range from a list of allowed Nodes
to hierarchy of Nodes.
This document defines one Targeting Expression Vocabulary for
STIX, which query providers may choose to use (or not). Third parties may define
their own Targeting Expression Vocabularies.
4.2.1 STIX[™] Targeting Expression
Vocabulary [comment?]
The Targeting Expression Vocabulary ID that identifies the STIX
Targeting Expression Vocabulary is the Content Binding ID for STIX. Recall that the
formula for a STIX Content Binding ID is:
"urn:oasis:cti:stix:" + format +
":" + version
The set of allowed Nodes within a Targeting Expression using
this vocabulary are:
1. Any XML element defined by the
version of STIX identified by the version portion of
the Targeting Expression Vocabulary ID. These Nodes do not have any additional
marking (e.g., the ‘STIX_Package’ element Node name is
‘STIX_Package’).
2. Any XML attribute defined by the
version of STIX identified by the version portion of
the Targeting Expression Vocabulary ID. These Nodes are prefixed by an at (@) symbol
(e.g., the ‘version’ attribute Node name is ‘@version’).
The Node ordering is defined by the version of STIX identified
by the version portion of the Targeting Expression
Vocabulary ID. Specifically, the Node hierarchy follows the following rules:
1. The STIX root element (e.g.,
STIX_Package) is the root Node and is at the top of the hierarchy.
2. Child elements and attributes of a
STIX element are children of that Node
a. e.g., ‘Indicators’, an
XML element, and ‘version’, an XML attribute, are both child Nodes of the
STIX_Package Node.
b. The ‘Indicators’ Node name is
‘Indicators’
c. The ‘version’ Node name
is ‘@version’
3. The Field Wildcard (*) is
permitted.
4. The Multi-field Wildcard (**) is
permitted.
Examples:
1. STIX_Package/* - targets any element
or attribute child of the STIX_Package XML Element
2. STIX_Package/Indicators/** - targets
any element or attribute descendant of the Indicators XML Element.
3. **/@id - targets any attribute named
‘id’ within the STIX structure.
4.2.2 Third Party Targeting Expression Vocabularies [comment?]
All Third Party Targeting Expression Vocabularies MUST define
the following information:
1. The Targeting Expression Vocabulary
ID, which MUST be in URI format.
2. The set of allowed Nodes
3. The hierarchy of allowed nodes
4. The meaning of the Field Wildcard
(the Field Wildcard MAY be prohibited)
5. The meaning of the Multi-field
Wildcard (the Multi-field Wildcard MAY be prohibited)
6. At least one example Targeting
Expression. The example should include a statement as to which record region is
targeted by that Targeting Expression.
4.2.3 Example Third Party Targeting Expression Vocabulary [comment?]
This section provides an example that only permits a single
field of “File_Hash”. A Third Party might define this vocabulary if they
wish to provide a service that permits only queries that look for information on a
particular file hash.
Targeting Expression Vocabulary ID:
urn:example.com:vocab:filehash
Allowed Nodes: ‘File_Hash’
Node Hierarchy: There is no hierarchy, as there is only one level of Nodes
Field Wildcard: This is prohibited
Multi-field Wildcard: This is prohibited
Examples:
1. File_Hash - targets the file hash
portion of the record.
This section contains the Capability Modules defined by this
document. Third parties may define additional capability modules for use with the
TAXII Default Query.
This section defines thee capability modules:
· Core – A
common set of relationships that are expected to be implementable across a wide range
of systems.
· Regular
Expression – Defines the ability to use a regular expression in a Default
Query.
· Timestamps
– Relationships that can be used to compare timestamps.
5.1 Capability Module: Core [comment?]
This section defines the Core Capability Module. The Core
Capability Module includes a set of relationships that can be expressed in a wide
range of database systems.
The Capability Module ID that identifies this capability module
is:
urn:oasis:cti:taxii:query:capability:core-1
5.1.1 Relationship: equals [comment?]
The equals relationship returns true if the target matches the
value exactly. If the target merely contains the value (but does not match exactly)
the relationship returns false.
Table 7 - Parameters for Core Equals
|
Parameter Name
|
Permitted Values
|
Description
|
|
match_type
|
Only the following values are permitted:
·
case_sensitive_string
·
case_insensitive_string
· number
|
case_sensitive_string indicates that a case sensitive
string comparison should be performed.
case_insensitive_string indicates that a case insensitive
string comparison should be performed.
number indicates that a numeric comparison should be
performed.
Other match types (e.g., Date/Time) are not permitted for
this relationship.
|
|
value
|
Any string is permitted
|
The string that the target is compared against.
|
5.1.2 Relationship: not_equals [comment?]
The not equals relationship returns true
if the target does not match the value.
Table 8 - Parameters for Core Not Equals
|
Parameter Name
|
Permitted Values
|
Description
|
|
match_type
|
Only the following values are permitted:
·
case_sensitive_string
·
case_insensitive_string
· number
|
case_sensitive_string indicates that a case sensitive
string comparison should be performed.
case_insensitive_string indicates that a case insensitive
string comparison should be performed.
number indicates that a numeric comparison should be
performed.
Other match types (e.g., Date/Time) are not permitted for
this relationship.
|
|
value
|
Any string is permitted
|
The string that the target is compared against.
|
5.1.3 Relationship: greater_than [comment?]
The greater than relationship returns true if the target is
numerically greater than the value. This relationship is only valid for numeric
comparisons (e.g., it is not valid for string comparisons).
Table 9 - Parameters for Core Greater Than
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any number is permitted
|
The number that the target is compared against.
|
5.1.4 Relationship:
greater_than_or_equal [comment?]
The greater than or equal relationship returns true if the
target is numerically greater than or equal to the value. This relationship is only
valid for numeric comparisons (e.g., it is not valid for string comparisons).
Table 10 - Parameters for Core Greater Than or Equals
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any number is permitted
|
The number that the target is compared against.
|
5.1.5 Relationship: less_than [comment?]
The less than relationship returns true if the target is
numerically less than the value. This relationship is only valid for numeric
comparisons (e.g., it is not valid for string comparisons).
Table 11 - Parameters for Core Less Than
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any number is permitted
|
The number that the target is compared against.
|
5.1.6 Relationship:
less_than_or_equal [comment?]
The less than or equal relationship returns true if the target
is numerically less than or equal to the value. This relationship is only valid for
numeric comparisons (e.g., it is not valid for string comparisons).
Table 12 - Parameters for Core Less Than or Equal
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any number is permitted
|
The number that the target is compared against.
|
5.1.7 Relationship:
does_not_exist [comment?]
The greater than relationship returns true if the target does
not exist.
Table 13 - Parameters for Core Does Not Exist
|
Parameter Name
|
Permitted Values
|
Description
|
|
There are not any parameters for this
relationship.
|
5.1.8 Relationship: exists [comment?]
The contains relationship returns true if the target exists.
Table 14 - Parameters for Core Exists
|
Parameter Name
|
Permitted Values
|
Description
|
|
There are not any parameters for this
relationship.
|
5.1.9 Relationship: begins_with [comment?]
The begins with relationship returns true if the target begins
with the value. This relationship is only valid for string comparisons.
Table 15 - Parameters for Core Begins With
|
Parameter Name
|
Permitted Values
|
Description
|
|
case_sensitive
|
Only the following values are permitted:
· true
· false
|
If true, a case sensitive comparison should be performed.
If false, a case insensitive comparison should be performed. If this field is
absent, this parameter should be treated as “true”.
|
|
value
|
Any string is permitted
|
The string that the target is compared against.
|
5.1.10 Relationship: ends_with [comment?]
The ends with relationship returns true if the target ends with
the value. This relationship is only valid for string comparisons.
Table 16 - Parameters for Core Ends With
|
Parameter Name
|
Permitted Values
|
Description
|
|
case_sensitive
|
Only the following values are permitted:
· true
· false
|
If true, a case sensitive comparison should be performed.
If false, a case insensitive comparison should be performed. If this field is
absent, this parameter should be treated as “true”.
|
|
value
|
Any string is permitted
|
The string that the target is compared against.
|
5.1.11 Relationship: contains [comment?]
The contains relationship returns true if the target contains
the value. This relationship is only valid for string comparisons.
Table 17 - Parameters for Core Contains
|
Parameter Name
|
Permitted Values
|
Description
|
|
case_sensitive
|
Only the following values are permitted:
· true
· false
|
If true, a case sensitive comparison should be performed.
If false, a case insensitive comparison should be performed. If this field is
absent, this parameter should be treated as “true”.
|
|
value
|
Any string is permitted
|
The string that the target is compared against.
|
5.2 Capability Module: Regular Expression [comment?]
This section defines the Regular Expression Capability Module.
The Regular Expression Capability Module includes a single relationship that is used
to perform Regular Expression Matching.
The Capability Module ID that identifies this capability module
is:
urn:oasis:cti:taxii:query:capability:regex-1
5.2.1 Relationship: matches [comment?]
The matches relationship returns true if the target matches the
regular expression contained in the value.
Table 18 - Parameters for Regex Matches
|
Parameter Name
|
Permitted Values
|
Description
|
|
case_sensitive
|
Only the following values are permitted:
· true
· false
|
true indicates that the regular expression should be
matched in a case sensitive manner. False indicates that the regular expression
should be matched in a case insensitive manner.
|
|
value
|
Regular expressions that conform to the CybOX[™] common subset of regular expression syntax.
|
The regular expression that the target is compared
against. The regular expressions in this field must conform to the regular
expression syntax used by CybOX: http://cybox.mitre.org/language/regular_expression_support.pdf.
|
5.3 Capability Module –
Timestamp [comment?]
The Capability Module ID that identifies this capability module
is:
urn:oasis:cti:taxii:query:capability:timestamp-1
This capability module includes relationships that operate on
timestamps.
5.3.1 Relationship: equals [comment?]
The equals relationship returns true if the target and the value
indicate the same time and date. This relationship is only valid for timestamp
comparisons.
Table 19 - Parameters for Timestamp Equals
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any RFC 3339 conformant timestamp is permitted
|
The timestamp that the target is compared against.
|
5.3.2 Relationship: greater_than [comment?]
The greater than relationship returns true if the target occurs
after the value. This relationship is only valid for timestamp comparisons.
Table 20 - Parameters for Timestamp Greater Than
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any RFC 3339 conformant timestamp is permitted
|
The timestamp that the target is compared against.
|
5.3.3 Relationship:
greater_than_or_equals [comment?]
The greater than or equals relationship returns true if the
target occurs after the value or the target and value indicate the same time and
date. This relationship is only valid for timestamp comparisons.
Table 21 - Parameters for Timestamp Greater Than or
Equals
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any RFC 3339 conformant timestamp is permitted
|
The timestamp that the target is compared against.
|
5.3.4 Relationship: less_than [comment?]
The less than relationship returns true if the target occurs
before the value. This relationship is only valid for timestamp comparisons.
Table 22 - Parameters for Timestamp Less Than
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any RFC 3339 conformant timestamp is permitted
|
The timestamp that the target is compared against.
|
5.3.5 Relationship:
less_than_or_equals [comment?]
The less than or equals relationship returns true if the target
occurs before the value or the target and value indicate the same time and date. This
relationship is only valid for timestamp comparisons.
Table 23 - Parameters for Timestamp Less Than or Equals
|
Parameter Name
|
Permitted Values
|
Description
|
|
value
|
Any RFC 3339 conformant timestamp is permitted
|
The timestamp that the target is compared against.
|
6.1 Query Information Structure Example [comment?]
<!-- An example of a Supported_Query field
-->
<taxii:Supported_Query
xmlns:taxii="http://docs.oasis-open.org/cti/ns/taxii/xml-binding-1.1.1"
format_id="urn:oasis:cti:taxii:query:1.1.1">
<!-- The format_id indicates that
this is a TAXII Default Query -->
<tdq:Default_Query_Info
xmlns:tdq="http://docs.oasis-open.org/cti/ns/taxii/default-query-1.1.1">
<!-- This
Targeting_Expression_Info element indicates the following:
- STIX 1.1
is supported
- The
Indicators portion of STIX is the preferred scope
- All of
STIX is in the allowed scope
-->
<tdq:Targeting_Expression_Info
targeting_expression_id="urn:oasis:cti:stix:xml:1.2.1">
<tdq:Preferred_Scope>STIX_Package/Indicators/**</tdq:Preferred_Scope>
<tdq:Allowed_Scope>**</tdq:Allowed_Scope>
</tdq:Targeting_Expression_Info>
<!-- The
Capability_Module element indicates that:
- The Core
capability module is supported
- The Regex
capability module is supported
-->
<tdq:Capability_Module>urn:oasis:cti:taxii:query:capability:core-1</tdq:Capability_Module>
<tdq:Capability_Module>urn:oasis:cti:taxii:query:capability:regex-1</tdq:Capability_Module>
</tdq:Default_Query_Info>
</taxii:Supported_Query>
6.2 Query Structure Example - 1 [comment?]
<!-- An example of a Query field. The
format_id indicates that this is a TAXII Default Query. -->
<taxii:Query
xmlns:taxii="http://docs.oasis-open.org/cti/ns/taxii/xml-binding-1.1.1"
format_id="urn:oasis:cti:taxii:query:1.1.1">
<!-- This query tests for id
attributes that begin with 'EXAMPLE' (case insensitive) -->
<tdq:Default_Query
xmlns:tdq="http://docs.oasis-open.org/cti/ns/taxii/default-query-1.1.1"
targeting_expression_id="urn:oasis:cti:stix:xml:1.2.1">
<tdq:Criteria operator="OR"><!-- Any child Criteria/Criterion evaluates
to true -->
<tdq:Criterion negate="false"><!-- This
criterion is not negated -->
<tdq:Target>**/@id</tdq:Target><!-- Matches any ID attribute, anywhere -->
<!-- This test looks uses the 'begins with' relationship in
the
core capability module, looking for values that begin with
'EXAMPLE'
(Case insensitie).
-->
<tdq:Test
capability_id="urn:oasis:cti:taxii:query:capability:core-1"
relationship="begins_with">
<tdq:Parameter name="case_sensitive">false</tdq:Parameter>
<tdq:Parameter name="value">EXAMPLE</tdq:Parameter>
</tdq:Test>
</tdq:Criterion>
</tdq:Criteria>
</tdq:Default_Query>
</taxii:Query>
6.3 Query Structure Example – 2 [comment?]
<!-- An example of a Query field. The
format_id indicates that this is a TAXII Default Query. -->
<taxii:Query
xmlns:taxii="http://docs.oasis-open.org/cti/ns/taxii/xml-binding-1.1.1"
format_id="urn:oasis:cti:taxii:query:1.1.1">
<!-- This query tests for id
attributes that begin with 'example' (case sensitive) and
have a description that contains 'The quick brown fox jumped over the very
lazy dogs.' (case
insensitive).
-->
<tdq:Default_Query
xmlns:tdq="http://docs.oasis-open.org/cti/ns/taxii/default-query-1.1.1"
targeting_expression_id="urn:oasis:cti:stix:xml:1.2.1">
<tdq:Criteria operator="AND"><!-- All Child Criteria/Criterion evaluate to
true -->
<tdq:Criterion negate="false"><!--
Criterion is not negated -->
<tdq:Target>**/@id</tdq:Target><!-- Matches any ID attribute, anywhere -->
<!-- This test looks for any value that begins with example,
and is case sensitive -->
<tdq:Test capability_id="urn:oasis:cti:taxii:query:capability:core-1" relationship="begins_with">
<tdq:Parameter name="case_sensitive">true</tdq:Parameter>
<tdq:Parameter name="value">example</tdq:Parameter>
</tdq:Test>
</tdq:Criterion>
<tdq:Criterion negate="false"><!--
Criterion is not negated -->
<tdq:Target>**/Description</tdq:Target><!-- Matches any Description, anywhere -->
<!-- This test looks for any value that contains the value,
case insensisive -->
<tdq:Test capability_id="urn:oasis:cti:taxii:query:capability:core-1" relationship="contains">
<tdq:Parameter name="case_sensitive">false</tdq:Parameter>
<tdq:Parameter name="value">The quick brown
fox jumped over the very lazy dogs.</tdq:Parameter>
</tdq:Test>
</tdq:Criterion>
</tdq:Criteria>
</tdq:Default_Query>
</taxii:Query>
Implementations have discretion over which parts of TAXII they
implement (e.g., Discovery Service).
Conformant implementations must conform to all Normative
Statements that apply to the portions of TAXII they implement (e.g., Implementers of
the Discovery Service must conform to all Normative Statements regarding the
Discovery Service).
Conformant implementations are free to ignore Normative
Statements that do not apply to the portions of TAXII they implement (e.g.,
Non-implementers of the Discovery Service are free to ignore all Normative Statements
regarding the Discovery Service).
The conformance section of this document is intentionally broad
and attempts to reiterate what already exists in this document. The TAXII 1.1
Specifications, which this specification is based on, did not have a conformance
section. Instead, the TAXII 1.1 Specifications relied on normative text. TAXII 1.1.1
represents a minimal change from TAXII 1.1, and in that spirit no new requirements
have been defined in this document.
The individuals listed in this specification have participated
in the creation of this specification and are gratefully acknowledged.
Authors of initial MITRE TAXII Specifications:
Mark Davidson, MITRE
Charles Schmidt, MITRE
Participants:
The following individuals were members of the OASIS CTI
Technical Committee during the creation of this specification and their contributions
are gratefully acknowledged:
· David Crawford,
Aetna
· Joerg Eschweiler,
Airbus Group SAS
· Marcos Orallo,
Airbus Group SAS
· Roman Fiedler,
AIT Austrian Institute of Technology
· Florian Skopik,
AIT Austrian Institute of Technology
· Dean Thompson,
Australia and New Zealand Banking Group (ANZ Bank)
· Alexander Foley,
Bank of America
· Yogesh Mudgal,
Bloomberg
· Owen Johnson,
Blue Coat Systems, Inc.
· Bret Jordan, Blue
Coat Systems, Inc.
· Adnan Baykal,
Center for Internet Security (CIS)
· Ron Davidson,
Check Point Software Technologies
· David McGrew,
Cisco Systems
· Pavan Reddy,
Cisco Systems
· Omar Santos,
Cisco Systems
· Jyoti Verma,
Cisco Systems
· Liron Schiff,
Comilion (mobile) Ltd.
· Guy Wertheim,
Comilion (mobile) Ltd.
· Doug DePeppe,
Cyber Threat Intelligence Network, Inc. (CTIN)
· Jane Ginn, Cyber
Threat Intelligence Network, Inc. (CTIN)
· Ben Othman, Cyber
Threat Intelligence Network, Inc. (CTIN)
· Jeff Williams,
Dell
· Richard Struse,
DHS Office of Cybersecurity and Communications (CS&C)
· Marlon Taylor,
DHS Office of Cybersecurity and Communications (CS&C)
· Dan Brown,
DTCC
· Gordon Hundley,
DTCC
· Chris Koutras,
DTCC
· Robert Griffin,
EMC
· Jeff Odom,
EMC
· Ravi Sharda,
EMC
· David Eilken,
Financial Services Information Sharing and Analysis Center (FS-ISAC)
· Sarah Brown,
Fox-IT
· Ryusuke Masuoka,
Fujitsu Limited
· Eric Burger,
Georgetown University
· Peter Allor,
IBM
· Eldan Ben-Haim,
IBM
· Peter Clark,
IBM
· Sandra Hernandez,
IBM
· Jason Keirstead,
IBM
· John Morris,
IBM
· Arvid Van Essche,
IBM
· Ron Williams,
IBM
· Paul Martini,
iboss, Inc.
· Chris Richardson,
IID
· Jerome Athias,
Individual
· Peter Brown,
Individual
· Elysa Jones,
Individual
· Sanjiv Kalkar,
Individual
· Bar Lockwood,
Individual
· Terry MacDonald,
Individual
· Alex Pinto,
Individual
· Michael Schwartz,
Individual
· Patrick Maroney,
Integrated Networking Technologies, Inc.
· Andres More,
Intel Corporation
· Wouter
Bolsterlee, Intelworks BV
· Marko
Dragoljevic, Intelworks BV
· Joep Gommers,
Intelworks BV
· Sergey Polzunov,
Intelworks BV
· Rutger Prins,
Intelworks BV
· Andrei
Sîrghi, Intelworks BV
· Raymon van der
Velde, Intelworks BV
· Niels van Dijk,
Intelworks BV
· Robert Huber,
iSIGHT Partners, Inc.
· Ben Huguenin,
Johns Hopkins University Applied Physics Laboratory
· Mark Moss, Johns
Hopkins University Applied Physics Laboratory
· Pamela Smith,
Johns Hopkins University Applied Physics Laboratory
· Terrence
Driscoll, JPMorgan Chase Bank, N.A.
· David Laurance,
JPMorgan Chase Bank, N.A.
· Brandon Hoffman,
Lumeta Corporation
· Jonathan Baker,
Mitre Corporation
· Sean Barnum,
Mitre Corporation
· Mark Davidson,
Mitre Corporation
· Jasen Jacobsen,
Mitre Corporation
· Ivan Kirillov,
Mitre Corporation
· Jon Salwen, Mitre
Corporation
· Charles Schmidt,
Mitre Corporation
· John Wunder,
Mitre Corporation
· James Cabral, MTG
Management Consultants, LLC.
· Scott Algeier,
National Council of ISACs (NCI)
· Denise Anderson,
National Council of ISACs (NCI)
· Josh Poster,
National Council of ISACs (NCI)
· Mike Boyle,
National Security Agency
· Jessica
Fitzgerald-McKay, National Security Agency
· Takahiro
Kakumaru, NEC Corporation
· John-Mark Gurney,
New Context Services, Inc.
· Christian Hunt,
New Context Services, Inc.
· Daniel Riedel,
New Context Services, Inc.
· Andrew Storms,
New Context Services, Inc.
· Nat Sakimura,
Nomura Research Institute, Ltd. (NRI)
· David Darnell,
North American Energy Standards Board
· Cory Casanave,
Object Management Group
· Don Thibeau, Open
Identity Exchange
· Vishaal
Hariprasad, Palo Alto Networks
· John Tolbert,
Queralt, Inc.
· Daniel
Wyschogrod, Raytheon Company-SAS
· Ted Julian,
Resilient Systems, Inc..
· Brian Engle,
Retail Cyber Intelligence Sharing Center (R-CISC)
· Igor Baikalov,
Securonix
· Bernd Grobauer,
Siemens AG
· John Anderson,
Soltra
· Aishwarya Asok
Kumar, Soltra
· Peter Ayasse,
Soltra
· Jeff Beekman,
Soltra
· Jonathan Bush,
Soltra
· Michael Butt,
Soltra
· Cynthia Camacho,
Soltra
· Aharon Chernin,
Soltra
· Mark Clancy,
Soltra
· Brady Cotton,
Soltra
· Trey Darley,
Soltra
· Paul Dion,
Soltra
· Daniel Dye,
Soltra
· Brandon Hanes,
Soltra
· Robert Hutto,
Soltra
· Ali Khan,
Soltra
· Chris Kiehl,
Soltra
· Michael Pepin,
Soltra
· Natalie Suarez,
Soltra
· David Waters,
Soltra
· Chip Wickenden,
Soltra
· Benjamin Yates,
Soltra
· Cedric LeRoux,
Splunk Inc.
· Brian Luger,
Splunk Inc.
· Kathy Wang,
Splunk Inc.
· Curtis Kostrosky,
Symantec Corp.
· Greg Reaume,
TELUS
· Alan Steer,
TELUS
· Crystal Hayes,
The Boeing Company
· Tyron Miller,
Threat Intelligence Pty Ltd
· Andrew van der
Stock, Threat Intelligence Pty Ltd
· Andrew
Pendergast, ThreatConnect, Inc.
· Jason Spies,
ThreatConnect, Inc.
· Nick Keuning,
ThreatQuotient, Inc.
· Wei Huang,
ThreatStream
· Hugh Njemanze,
ThreatStream
· Chris Roblee,
TruSTAR Technology
· Mark Angel, U.S.
Bank
· Brad Butts, U.S.
Bank
· Mona Magathan,
U.S. Bank
· Adam Cooper,
United Kingdom Cabinet Office
· Mike McLellan,
United Kingdom Cabinet Office
· Chris O'Brien,
United Kingdom Cabinet Office
· James Penman,
United Kingdom Cabinet Office
· Howard Staple,
United Kingdom Cabinet Office
· Alastair
Treharne, United Kingdom Cabinet Office
· Julian White,
United Kingdom Cabinet Office
· Evette
Maynard-Noel, US Department of Homeland Security
· Justin
Stekervetz, US Department of Homeland Security
· Robert Coderre,
VeriSign
· Kyle Maxwell,
VeriSign
· Lee Chieffalo,
ViaSat, Inc.
· Wilson Figueroa,
ViaSat, Inc.
· Anthony
Rutkowski, Yaana Technologies, LLC
Special Thanks:
A special thanks to the US Department of Homeland
Security’s (DHS) National Cybersecurity and Communications Integration Center
(NCCIC), and to Richard Struse, Chief Advanced Technology Officer of the DHS NCCIC.
Without your sponsorship, vision, and relentless vigor, none of this would have been
possible.
|
Revision
|
Date
|
Editor
|
Changes Made
|
|
Working Draft 01
|
01 July 2015
|
Bret Jordan
|
Initial working draft based on MITRE specification
|

